Magic Quadrant for Network Access Control.pdf - WIT
Magic Quadrant for Network Access Control.pdf - WIT
Magic Quadrant for Network Access Control.pdf - WIT
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
1 of 18 19/8/2553 15:31<br />
2 July 2010<br />
Lawrence Orans, John Pescatore<br />
Gartner RAS Core Research Note G00201432<br />
The network access control market continued to mature, squeezing hype out of the market and intensifying the focus on<br />
ease of implementation and near-term payback. Several point solutions persist, with some continuing to provide<br />
differentiated value.<br />
What You Need to Know<br />
<strong>Network</strong> access control (NAC) will increasingly be used to help enterprises<br />
manage the consumerization trend, as more enterprises allow employees to "bring<br />
their own PC to work." NAC will enable network managers to gain back some<br />
control over their networks by allowing access to some devices, while denying<br />
access to others. When evaluating NAC solutions, look <strong>for</strong> vendors that<br />
understand the consumerization trend and support, or have plans to support,<br />
policies <strong>for</strong> managing the non-Microsoft endpoints that will inevitably attempt to<br />
connect to your network.<br />
Return to Top<br />
Vendors Added or Dropped<br />
We review and adjust our inclusion criteria <strong>for</strong><br />
<strong>Magic</strong> <strong>Quadrant</strong>s and MarketScopes as markets<br />
change. As a result of these adjustments, the<br />
mix of vendors in any <strong>Magic</strong> <strong>Quadrant</strong> or<br />
MarketScope may change over time. A vendor<br />
appearing in a <strong>Magic</strong> <strong>Quadrant</strong> or MarketScope<br />
one year and not the next does not necessarily<br />
indicate that we have changed our opinion of<br />
that vendor. This may be a reflection of a<br />
change in the market and, there<strong>for</strong>e, changed<br />
evaluation criteria, or a change of focus by a<br />
vendor.<br />
Evaluation Criteria Definitions<br />
<strong>Magic</strong> <strong>Quadrant</strong><br />
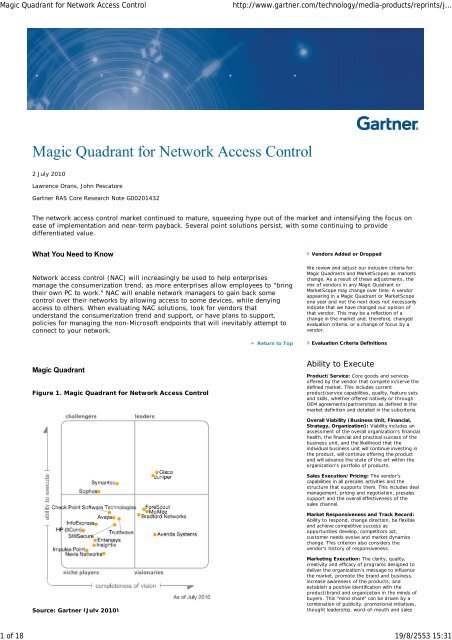
Figure 1. <strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
Ability to Execute<br />
Product/Service: Core goods and services<br />
offered by the vendor that compete in/serve the<br />
defined market. This includes current<br />
product/service capabilities, quality, feature sets<br />
and skills, whether offered natively or through<br />
OEM agreements/partnerships as defined in the<br />
market definition and detailed in the subcriteria.<br />
Overall Viability (Business Unit, Financial,<br />
Strategy, Organization): Viability includes an<br />
assessment of the overall organization's financial<br />
health, the financial and practical success of the<br />
business unit, and the likelihood that the<br />
individual business unit will continue investing in<br />
the product, will continue offering the product<br />
and will advance the state of the art within the<br />
organization's portfolio of products.<br />
Sales Execution/Pricing: The vendor's<br />
capabilities in all presales activities and the<br />
structure that supports them. This includes deal<br />
management, pricing and negotiation, presales<br />
support and the overall effectiveness of the<br />
sales channel.<br />
Market Responsiveness and Track Record:<br />
Ability to respond, change direction, be flexible<br />
and achieve competitive success as<br />
opportunities develop, competitors act,<br />
customer needs evolve and market dynamics<br />
change. This criterion also considers the<br />
vendor's history of responsiveness.<br />
Source: Gartner (July 2010)<br />
Marketing Execution: The clarity, quality,<br />
creativity and efficacy of programs designed to<br />
deliver the organization's message to influence<br />
the market, promote the brand and business,<br />
increase awareness of the products, and<br />
establish a positive identification with the<br />
product/brand and organization in the minds of<br />
buyers. This "mind share" can be driven by a<br />
combination of publicity, promotional initiatives,<br />
thought leadership, word-of-mouth and sales
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
2 of 18 19/8/2553 15:31<br />
Market Overview<br />
Return to Top<br />
Although NAC adoption increased (primarily to support guest networking) in<br />
2009, as we predicted in "<strong>Network</strong> <strong>Access</strong> <strong>Control</strong> Market Overview" in December<br />
2004, the increasing availability of NAC functionality in network infrastructure and<br />
endpoint protection (EPP) products put severe pressure on NAC revenue. In 2004,<br />
we said, "However, as organizations progress through the technology refresh<br />
cycle and upgrade to solutions with built-in NAC functions, many will no longer<br />
pay extra <strong>for</strong> independent NAC solutions." We saw many enterprises decide to<br />
look to their EPP vendors <strong>for</strong> embedded NAC capabilities, as well as many that<br />
decided to wait until they rolled out Windows 7 on desktops to make NAC<br />
decisions. Although this was partly driven by the economic slowdown, it mostly<br />
represents what will be the continuing market reality.<br />
This led to the exit of ConSentry <strong>Network</strong>s from the NAC market, while other NAC<br />
vendors attempted to broaden their products' appeal beyond NAC functionality.<br />
Aruba, which had been reselling a private-labeled version of Brad<strong>for</strong>d <strong>Network</strong>s'<br />
NAC appliance, decided it made more sense to focus on selling rich wireless<br />
networking solutions with embedded NAC capabilities, rather than to pursue<br />
specific NAC revenue.<br />
The pressure on the NAC market and the failure of several NAC vendors have led<br />
to a common misconception that "NAC is dead" — classic Trough of<br />
Disillusionment behavior. However, in working with Gartner clients evaluating and<br />
deploying NAC during the past year, as well as in talking to the reference<br />
customers supplied by vendors as part of this <strong>Magic</strong> <strong>Quadrant</strong> analysis, we<br />
continue to see early adopters expanding beyond basic NAC functionality, while<br />
new NAC installations continue to focus on meeting immediate guest networking<br />
needs. The "consumerization of IT" trend is driving the need <strong>for</strong> guest networking<br />
to rapidly expand beyond contractors and visitors to employees using their own<br />
laptops or smartphones. To a large extent, many enterprises are starting to look<br />
more like the early adopters of NAC, college campuses, with an increasingly<br />
chaotic mix of managed and unmanaged IT on the corporate network. Because<br />
employee-owned laptops or smartphones will typically not have corporate<br />
endpoint security software on them, stand-alone NAC capabilities will see higher<br />
demand.<br />
As targeted botnet attacks (such as that suffered by Google and many other<br />
high-profile businesses in 2010) cause increasing damage, Gartner believes those<br />
initial guest networking implementations will be expanded to include the endpoint<br />
baselining/health check — provided that NAC vendors move beyond simple<br />
vulnerability checking and build in support <strong>for</strong> detecting whether an endpoint is<br />
dangerous versus just missing patches or being behind in antivirus signatures.<br />
The increasing publicity around targeted malware has also caused increased<br />
demand <strong>for</strong> post-connect containment capabilities, but we have seen very limited<br />
demand <strong>for</strong> advanced identity-aware NAC capabilities, outside of the traditional<br />
high-security "belt and suspenders" enterprises. We believe that NAC vendors that<br />
manage to grow in 2010 and beyond will be the ones that increase their<br />
capabilities <strong>for</strong> enterprises to safely allow unmanaged PCs and mobile devices to<br />
be used to meet business needs.<br />
activities.<br />
Customer Experience: Relationships, products<br />
and services/programs that enable clients to be<br />
successful with the products evaluated.<br />
Specifically, this includes the ways customers<br />
receive technical support or account support.<br />
This can also include ancillary tools, customer<br />
support programs (and the quality thereof),<br />
availability of user groups, service-level<br />
agreements and so on.<br />
Operations: The ability of the organization to<br />
meet its goals and commitments. Factors include<br />
the quality of the organizational structure,<br />
including skills, experiences, programs, systems<br />
and other vehicles that enable the organization<br />
to operate effectively and efficiently on an<br />
ongoing basis.<br />
Completeness of Vision<br />
Market Understanding: Ability of the vendor<br />
to understand buyers' wants and needs and to<br />
translate those into products and services.<br />
Vendors that show the highest degree of vision<br />
listen to and understand buyers' wants and<br />
needs, and can shape or enhance those with<br />
their added vision.<br />
Marketing Strategy: A clear, differentiated set<br />
of messages consistently communicated<br />
throughout the organization and externalized<br />
through the website, advertising, customer<br />
programs and positioning statements.<br />
Sales Strategy: The strategy <strong>for</strong> selling<br />
products that uses the appropriate network of<br />
direct and indirect sales, marketing, service and<br />
communication affiliates that extend the scope<br />
and depth of market reach, skills, expertise,<br />
technologies, services and the customer base.<br />
Offering (Product) Strategy: The vendor's<br />
approach to product development and delivery<br />
that emphasizes differentiation, functionality,<br />
methodology and feature sets as they map to<br />
current and future requirements.<br />
Business Model: The soundness and logic of<br />
the vendor's underlying business proposition.<br />
Vertical/Industry Strategy: The vendor's<br />
strategy to direct resources, skills and offerings<br />
to meet the specific needs of individual market<br />
segments, including vertical markets.<br />
Innovation: Direct, related, complementary and<br />
synergistic layouts of resources, expertise or<br />
capital <strong>for</strong> investment, consolidation, defensive<br />
or pre-emptive purposes.<br />
Geographic Strategy: The vendor's strategy<br />
to direct resources, skills and offerings to meet<br />
the specific needs of geographies outside the<br />
"home" or native geography, either directly or<br />
through partners, channels and subsidiaries as<br />
appropriate <strong>for</strong> that geography and market.<br />
The four most common uses <strong>for</strong> NAC are:<br />
Guest network services: Isolating guests and visitors from the corporate<br />
network and providing them with limited connectivity — typically, Internet<br />
access only. Guest networking was the primary driver in approximately 75%<br />
of NAC deployments. Most organizations are starting with wireless guest<br />
access and are planning to extend guest networking capabilities to the<br />
wired network.<br />
Endpoint baselining: Determining whether endpoints on the corporate<br />
network are compliant with device configuration policies (<strong>for</strong> example,<br />
up-to-date patches and antivirus signatures). Endpoint baselining was the<br />
primary driver in approximately 15% of NAC deployments.<br />
Quarantine/containment: Restricting network access either when<br />
endpoints are noncompliant with configuration policies, or when suspicious<br />
traffic from the endpoint presents a risk to the network or to other<br />
endpoints. Quarantining noncompliant endpoints is common in educational<br />
environments (where schools often don't control the endpoints); however,<br />
in other environments, it is only the primary driver in approximately 5% of<br />
deployments. Remediating noncompliant endpoints and "dangerous"<br />
endpoints is an important aspect of this use case.<br />
Identity-aware networking: Providing greater visibility and control over
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
3 of 18 19/8/2553 15:31<br />
user behavior on the network. Organizations add identity awareness to the<br />
network to monitor user traffic and en<strong>for</strong>ce access to critical resources.<br />
Identity-aware networking was the primary driver in approximately 5% of<br />
NAC deployments.<br />
Return to Top<br />
Market Definition/Description<br />
The NAC market consists of several categories, as outlined below:<br />
Infrastructure: Most enterprise-class LAN switch manufacturers offer NAC<br />
solutions. Seven of the eight vendors analyzed in "<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong><br />
Enterprise LAN (Global)," sell NAC products. The LAN switch vendors<br />
primarily target their NAC solutions to their installed base. That is a good<br />
strategy, because network managers, who are the buyers of LAN switches,<br />
are usually the buyers of NAC solutions. Infrastructure vendors have had<br />
limited success in selling their NAC solutions outside of their installed bases<br />
and into their competitors' accounts.<br />
EPP: Some vendors that sell EPP suites also offer NAC solutions (<strong>for</strong><br />
example, Check Point Software Technologies, McAfee, Sophos and<br />
Symantec). All these vendors benefit from their existing desktop "footprint,"<br />
which gives them an advantage in the endpoint baselining usage case.<br />
<strong>Network</strong> security vendors: A mix of intrusion prevention system (IPS),<br />
firewall and virtual private network (VPN) vendors offer NAC solutions.<br />
Because they already serve as en<strong>for</strong>cement points in the network, these<br />
products can be easily repurposed to become NAC policy en<strong>for</strong>cement<br />
points.<br />
Pure-play vendors: Several vendors are pure-play NAC vendors or<br />
vendors with multifunctional offerings whose primary focus is NAC (<strong>for</strong><br />
example, Avenda Systems, Brad<strong>for</strong>d <strong>Network</strong>s, ForeScout, Impulse Point,<br />
InfoExpress and Nevis <strong>Network</strong>s). The pure-play vendors face the biggest<br />
challenges, as vendors in the other three categories continue to enhance<br />
their NAC offerings.<br />
When measured by annual revenue, the NAC market is declining. Gartner<br />
estimates that the size of the NAC market in 2009 was approximately $199<br />
million, a decrease of approximately 10% over the market in 2008. We had<br />
anticipated a slowdown in market growth to 25%, but market factors detailed<br />
above and the severity of the economic slump contributed to the shrinking<br />
market. Also, some vendors exited the market, and others entered, but the overall<br />
effect was a net loss in market size. As we predicted back in 2004, the NAC<br />
capabilities existing or promised in network infrastructure, EPP plat<strong>for</strong>ms and the<br />
latest Windows desktop operating system impacted the growth of NAC-specific<br />
revenue, even as NAC "seats" increased. For 2010, we expect a flat market, with<br />
total revenue of approximately $200 million. Positive NAC demand factors, such<br />
as support <strong>for</strong> consumerization, will be offset by embedded NAC and a focus on<br />
inexpensive authentication, particularly 802.1X.<br />
Return to Top<br />
Inclusion and Exclusion Criteria<br />
The goal of the inclusion/exclusion criteria listed below is to identify those<br />
vendors that own core NAC technology. Vendors whose solutions are based<br />
heavily on technology that is licensed from original equipment manufacturers<br />
have been excluded from this <strong>Magic</strong> <strong>Quadrant</strong>.<br />
To be included in this <strong>Magic</strong> <strong>Quadrant</strong>, the vendors' solutions must include the<br />
policy, baseline and access control elements of NAC, as defined by the following<br />
criteria:<br />
Policy: The NAC solution must include a dedicated policy management<br />
server with a management interface <strong>for</strong> defining and administering security<br />
configuration requirements and <strong>for</strong> specifying the access control actions<br />
(<strong>for</strong> example, allow or quarantine) <strong>for</strong> compliant and noncompliant<br />
endpoints. The ability to report on the overall state of endpoint compliance<br />
is a critical component of the policy function. Because policy administration<br />
and reporting functions are key areas of NAC innovation and differentiation,<br />
vendors must own the core policy function to be included in this <strong>Magic</strong><br />
<strong>Quadrant</strong>.<br />
Baseline: A baseline determines the security state of an endpoint that is<br />
attempting a network connection (LAN, wireless LAN or VPN) so that a<br />
decision can be made about the level of access that will be allowed.<br />
Baselining must include the ability to assess policy compliance (<strong>for</strong>
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
4 of 18 19/8/2553 15:31<br />
example, up-to-date patches and antivirus signatures) and may include the<br />
ability to detect installed malware. Various technologies may be used <strong>for</strong><br />
the baseline function, including agentless solutions (such as vulnerability<br />
assessment scans), dissolvable agents and persistent agents. NAC solutions<br />
must include a baseline function, but "reinventing the wheel" is not<br />
necessary. Baseline functionality may be obtained via an OEM or licensing<br />
partnership.<br />
<strong>Access</strong> control: The NAC solution must include the ability to block,<br />
quarantine or grant full access to an endpoint. The solution must be flexible<br />
enough to en<strong>for</strong>ce access control in a multivendor network infrastructure,<br />
and it must be able to en<strong>for</strong>ce access in both LAN and remote-access<br />
environments. En<strong>for</strong>cement must be accomplished either via the network<br />
infrastructure — <strong>for</strong> example, 802.1X, virtual LANs (VLANs), access control<br />
lists (ACLs) — or via the vendor's NAC solution — <strong>for</strong> example,<br />
dropping/filtering packets or Address Resolution Protocol (ARP) spoofing.<br />
Dynamic Host Configuration Protocol (DHCP) en<strong>for</strong>cement qualifies <strong>for</strong><br />
inclusion, provided that policy en<strong>for</strong>cement can be delivered via<br />
partnerships with two or more DHCP solutions. Vendors that rely solely on<br />
agent-based endpoint self-en<strong>for</strong>cement do not qualify as NAC solutions.<br />
Additional criteria:<br />
Solutions must link to remediation systems (<strong>for</strong> example, patch and<br />
configuration management), but they do not need to own core mitigation<br />
technology.<br />
The products with the required features and functions must be shipping as<br />
of 1 February 2010.<br />
The vendor must have at least $2 million in NAC sales during the 12 months<br />
leading up to 1 February 2010.<br />
Vendors Considered but Not Included in the 2010 <strong>Magic</strong> <strong>Quadrant</strong><br />
LAN Switch Manufacturers<br />
LAN switch manufacturers that base critical components of their NAC solutions on<br />
OEM technology or that resell NAC solutions from other vendors have been<br />
excluded from this <strong>Magic</strong> <strong>Quadrant</strong>. For example, Extreme <strong>Network</strong>s has not been<br />
included in our analysis, because its Sentriant AG200 NAC solution is based on<br />
StillSecure's Safe <strong>Access</strong> product. Alcatel-Lucent has not been included, because<br />
its approach to NAC is to resell the CyberGatekeeper solution from InfoExpress.<br />
Small or Midsize Business (SMB) Vendors<br />
SMB vendors that lack enterprise-class features and functions have been excluded<br />
from this <strong>Magic</strong> <strong>Quadrant</strong>. For example, NetClarity is a vendor that targets SMBs.<br />
Its NetClarity family of NACwall appliances use an agentless (no additional<br />
software on the PCs) approach to baseline the health of the endpoints. NACwalls<br />
are deployed out of band in LANs, so they install easily and are not in the line of<br />
traffic (no additional latency to the network). NACwall appliances interface with<br />
existing switches and firewalls to en<strong>for</strong>ce access control. ARP manipulation can<br />
also be used to en<strong>for</strong>ce access. Napera <strong>Network</strong>s, an SMB-focused vendor that<br />
previously sold a family of switches with embedded support <strong>for</strong> Microsoft <strong>Network</strong><br />
<strong>Access</strong> Protection (NAP), has shifted its strategy to offer a cloud-based<br />
subscription service that per<strong>for</strong>ms endpoint baselining.<br />
Microsoft<br />
Microsoft embeds NAC functionality (branded as Microsoft NAP) within its more<br />
recent operating systems (Windows 7, Vista and XP Service Pack 3) and within<br />
Windows Server 2008. Consistent with our practice from 2009, we did not include<br />
Microsoft in this year's <strong>Magic</strong> <strong>Quadrant</strong> because of the requirement that<br />
organizations need to upgrade to the required Microsoft products. None of the<br />
other solutions in this <strong>Magic</strong> <strong>Quadrant</strong> require a desktop operating system update.<br />
However, we will re-evaluate Microsoft and the market penetration of Microsoft<br />
NAP-ready endpoints in 2011.<br />
Return to Top<br />
Added<br />
Avaya (via its acquisition of Nortel's Enterprise Solutions unit).<br />
Avenda Systems<br />
HP (via its acquisition of 3Com)<br />
Nevis <strong>Network</strong>s<br />
Return to Top
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
5 of 18 19/8/2553 15:31<br />
Dropped<br />
Aruba has terminated its licensing agreement with Brad<strong>for</strong>d <strong>Network</strong>s,<br />
which was the OEM of Aruba's Endpoint Compliance Systems appliance.<br />
Aruba is re-evaluating its NAC strategy.<br />
ConSentry effectively went out of business in August 2009 (although its<br />
website, at the time of this <strong>Magic</strong> <strong>Quadrant</strong>'s publication, is still operational<br />
and makes no mention of the company's change in status).<br />
Return to Top<br />
Evaluation Criteria<br />
Ability to Execute<br />
The Ability to Execute criteria are:<br />
Product/Service: An evaluation of the features and functions of the<br />
vendor's NAC solution. Because the most common usage case <strong>for</strong> NAC is<br />
guest networking (blocking unmanaged endpoints from the main network,<br />
and granting them limited access or Internet access only), those solutions<br />
with strong support <strong>for</strong> guest networking will score strongly. Support <strong>for</strong><br />
endpoint baselining and, to a lesser extent, identity-aware networking is<br />
also an important part of this criterion. Ease of use and the overall quality<br />
of the management and reporting features will be important considerations.<br />
Those solutions that support a variety of en<strong>for</strong>cement options (<strong>for</strong> example,<br />
VLAN steering, ACLs, DHCP and others) will score more highly than<br />
solutions with limited en<strong>for</strong>cement options.<br />
Overall Viability: Viability includes an assessment of the vendor's overall<br />
financial health, the financial and practical success of the business unit, and<br />
the likelihood of the individual business unit to continue to invest in an NAC<br />
solution.<br />
Sales Execution/Pricing: The vendors' capabilities in all presales<br />
activities and the structure that supports them. The ability of vendors to<br />
succeed in their target markets is important. Vendors that target large<br />
enterprises should demonstrate success in winning NAC deals of 10,000<br />
endpoints and more. Vendors that target SMBs should demonstrate a high<br />
volume of smaller and midsize deals.<br />
Market Responsiveness and Track Record: Ability to respond, change<br />
direction and be flexible as market dynamics vary. This criterion also<br />
considers the vendor's history of responsiveness, including how quickly it<br />
responded when the primary focus on NAC shifted from endpoint baselining<br />
to guest networking.<br />
Marketing Execution: This criterion assesses the effectiveness of the<br />
vendor's marketing programs and its ability to create awareness and "mind<br />
share" in the NAC market. Those vendors that frequently appear on client<br />
shortlists are succeeding in marketing execution.<br />
Customer Experience: Quality of the customer experience based on<br />
reference calls and input from Gartner clients.<br />
Operations: The ability of the organization to meet its goals and<br />
commitments in an efficient manner. Past per<strong>for</strong>mance is weighted heavily.<br />
Note — this criterion will not be evaluated <strong>for</strong> the NAC <strong>Magic</strong> <strong>Quadrant</strong>.<br />
Table 1. Ability to Execute Evaluation Criteria<br />
Evaluation Criteria<br />
Weighting<br />
Product/Service<br />
High<br />
Overall Viability (Business Unit, Financial, Strategy, Organization) High<br />
Sales Execution/Pricing<br />
Standard<br />
Market Responsiveness and Track Record<br />
Standard<br />
Marketing Execution<br />
Standard<br />
Customer Experience<br />
High<br />
Operations<br />
No rating<br />
Source: Gartner (July 2010)<br />
Return to Top<br />
Completeness of Vision
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
6 of 18 19/8/2553 15:31<br />
Completeness of Vision criteria are:<br />
Market Understanding: Ability of the vendor to understand buyers' needs<br />
and translate these needs into NAC products. This includes the ability to<br />
anticipate market trends and to quickly adapt via partnerships, acquisitions<br />
or internal development.<br />
Marketing Strategy: This criterion analyzes whether the vendor's<br />
marketing strategy succeeds in differentiating its NAC solution from its<br />
competitors.<br />
Sales Strategy: The vendor's strategy <strong>for</strong> selling to its target audience,<br />
including an analysis of the appropriate mix of direct and indirect sales<br />
channels.<br />
Offering (Product) Strategy: An evaluation of the vendor's strategic<br />
product direction and its road map <strong>for</strong> NAC. The product strategy should<br />
address the NAC trends reflected in Gartner's client inquiries.<br />
Business Model: The soundness and logic of the vendor's underlying value<br />
proposition. How well will the vendors' NAC strategy succeed in an<br />
environment where NAC is increasingly becoming a feature of broader<br />
network and security solutions.<br />
Vertical/Industry Strategy: The vendor's strategy <strong>for</strong> meeting the<br />
specific needs of individual vertical markets and market segments (<strong>for</strong><br />
example, higher education).<br />
Innovation: This criterion includes product leadership and the ability to<br />
deliver NAC features and functions that distinguish the vendor from its<br />
competitors.<br />
Geographic Strategy: The vendor's strategy <strong>for</strong> penetrating geographies<br />
outside its home or native market.<br />
Table 2. Completeness of Vision<br />
Evaluation Criteria<br />
Evaluation Criteria Weighting<br />
Market Understanding High<br />
Marketing Strategy Standard<br />
Sales Strategy<br />
Standard<br />
Offering (Product) Strategy High<br />
Business Model<br />
Standard<br />
Vertical/Industry Strategy Low<br />
Innovation<br />
Standard<br />
Geographic Strategy Low<br />
Source: Gartner (July 2010)<br />
Return to Top<br />
Leaders<br />
Leaders are successful in selling large NAC implementations (10,000 nodes and<br />
above) to multiple large enterprises as a primary offering. Leaders are networking<br />
and/or security companies that recognized early on that NAC would be an<br />
important component of their overall product portfolios and have been first to<br />
market with enhanced capabilities as the market matures. Leaders have the<br />
resources to maintain their commitment to NAC, have strong channel strength and<br />
have financial resources. They have also demonstrated a strong understanding of<br />
the future direction of NAC, including market demand <strong>for</strong> inexpensive guest<br />
network and authentication solutions. Leaders should not equate to a default<br />
choice <strong>for</strong> every buyer, and clients should not assume that they must buy only<br />
from vendors in the Leaders quadrant.<br />
Return to Top<br />
Challengers<br />
Challengers are networking and/or security companies that have been successful<br />
in selling NAC to their installed bases, although they are generally unsuccessful in<br />
selling NAC to the broader market. Challengers are generally not NAC innovators,<br />
but are large enough and diversified enough to continue investing in their NAC<br />
strategy. They are able to withstand challenges and setbacks more easily than<br />
Niche Players.
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
7 of 18 19/8/2553 15:31<br />
Return to Top<br />
Visionaries<br />
Visionaries have led the market in product innovation and/or displayed an early<br />
understanding of market <strong>for</strong>ces and trends. They are either smaller pure-play NAC<br />
vendors or larger networking and/or security companies. A common theme in<br />
visionary vendors is that they don't have significant channel strength and have not<br />
succeeded in building installed bases as large as the leaders. Pure-play vendors in<br />
the Visionaries quadrant face challenges in moving into the Leaders quadrant, due<br />
to the trend of network and security companies embedding NAC functionality in<br />
their existing solutions.<br />
Return to Top<br />
Niche Players<br />
Niche Players represent a mix of small and large companies. The large companies<br />
are network and/or security vendors that have had some success in selling NAC to<br />
their traditional installed base, but typically face stiff competition from other NAC<br />
vendors. Large Niche Players have generally struggled to sell NAC to the broader<br />
market. Small Niche Players don't appear often on Gartner clients' shortlists, but<br />
some of them are successful in addressing subsets of the overall market. Niche<br />
Players are valid suppliers in the market and often provide solutions targeted to<br />
the needs of a particular vertical industry.<br />
Return to Top<br />
Vendor Strengths and Cautions<br />
Avaya<br />
Avaya appears in the NAC <strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> the first time, as a result of its<br />
acquisition of Nortel's Enterprise Solutions unit. The key component in Avaya's<br />
NAC strategy is its RADIUS-based policy server, known as the Ignition Server,<br />
which is part of a solution that Nortel gained by acquiring key intellectual<br />
property of Identity Engines. The Ignition Server is available only as a virtual<br />
machine on VMware. The Avaya Health Agent is capable of baselining Windows<br />
endpoints. The primary use case <strong>for</strong> Avaya's NAC solution is the installed base of<br />
Nortel switch and wireless LAN customers, although the Ignition Server is capable<br />
of supporting non-Nortel environments.<br />
Return to Top<br />
Strengths<br />
Support <strong>for</strong> Microsoft NAP makes the Ignition Server a good choice in<br />
all-Microsoft environments.<br />
The Identity Engines offering provides a strong guest networking solution<br />
that is complete with user provisioning, reporting and management<br />
capabilities.<br />
Avaya has strong multivendor 802.1X support and operational tools (<strong>for</strong><br />
example, authentication reports) <strong>for</strong> easing the operational challenges of<br />
managing an 802.1X environment.<br />
Return to Top<br />
Cautions<br />
Avaya's NAC solution does not include permanent agents <strong>for</strong> baselining OS<br />
X, Linux or other non-Microsoft endpoints. It also does not offer an<br />
agentless scanning option.<br />
The Avaya installed base of network infrastructure (the main target<br />
audience <strong>for</strong> Avaya NAC) remains somewhat cautious and skeptical about<br />
Avaya's commitment to the market after enduring a very difficult and<br />
uncertain period as Nortel consolidated investments and dispersed its<br />
assets.<br />
Avaya's NAC solution has little visibility in the broader market (beyond<br />
Nortel's installed base).
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
8 of 18 19/8/2553 15:31<br />
Return to Top<br />
Avenda Systems<br />
Avenda Systems is a new entrant in the NAC <strong>Magic</strong> <strong>Quadrant</strong>. Its focus on the<br />
guest network use case and on interoperability (it was an early supporter of<br />
Trusted <strong>Network</strong> Connect [TNC] protocols) has contributed to its position in the<br />
Visionaries quadrant. Founded in 2006, Avenda's flagship offering is a<br />
RADIUS-based policy server, known as Enterprise Trust & Identity Policy System<br />
(eTIPS), that can be used in heterogeneous environments (mixed endpoints<br />
and/or mixed network infrastructure). eTIPS is available in an appliance <strong>for</strong>m<br />
factor, and also as a virtual machine <strong>for</strong> VMware. It supports 802.1X and<br />
Web-based authentication <strong>for</strong> wireless, wired and VPN environments, and can also<br />
be used to enable the endpoint baselining use case <strong>for</strong> NAC (it supports<br />
permanent agents, dissolvable agents and agentless scans via Nessus). Multiple<br />
en<strong>for</strong>cement options are offered, including VLAN steering, ACLs and DHCP.<br />
Enterprises that can tolerate the risks of a startup and need a solution to support<br />
a heterogeneous environment should consider Avenda.<br />
Return to Top<br />
Strengths<br />
Support <strong>for</strong> the TNC's Statement of Health protocol enables Avenda to<br />
provide endpoint baselining <strong>for</strong> Microsoft NAP-enabled endpoints (Windows<br />
7, Vista and XP SP3) without requiring an additional agent. Avenda also<br />
provides agents that can baseline endpoints running Apple OS X and Linux<br />
operating systems.<br />
Avenda's Quick 1X tool simplifies the configuration of a broad set of<br />
supplicants, including supplicants native to Windows and Linux. It also<br />
supports supplicants on Mac OS X, iPhone and iPad operating systems.<br />
References <strong>for</strong> Avenda commented that its solution provides a flexible and<br />
granular approach to creating policies.<br />
Return to Top<br />
Cautions<br />
Avenda's prospects <strong>for</strong> success are tied heavily to 802.1X, <strong>for</strong> which<br />
adoption in wired networks has been slow thus far.<br />
Enterprise inertia is a challenge <strong>for</strong> Avenda. Most enterprises have already<br />
implemented RADIUS servers from Cisco, FreeRADIUS, Microsoft or Juniper<br />
<strong>for</strong> their VPN and wireless access, and they are likely to stay with these<br />
existing solutions as they begin to extend RADIUS-based authentication to<br />
their wired networks.<br />
Avenda is a small company with limited resources. Microsoft and other<br />
vendors with a focus on the TNC specifications (<strong>for</strong> example, Juniper) have<br />
the resources to thwart Avenda's progress by duplicating eTIPS functionality<br />
on their own policy servers.<br />
Return to Top<br />
Brad<strong>for</strong>d <strong>Network</strong>s<br />
Brad<strong>for</strong>d <strong>Network</strong>s was one of the earlier entrants into the NAC market,<br />
developing its Campus Manager product to meet the needs of universities to allow<br />
a wide variety of university-owned and student-owned PCs to connect without<br />
causing security problems. Brad<strong>for</strong>d has built on this vertical industry to attack<br />
the broader NAC market. In May 2009, it brought in a new CEO. Brad<strong>for</strong>d renamed<br />
its lead NAC product "<strong>Network</strong> Sentry" and took steps to put more discipline in its<br />
channel strategy to go after corporate markets. In 2009, Aruba terminated its<br />
agreement to license technology from Brad<strong>for</strong>d. The loss of that OEM deal offset<br />
gains in its ability to execute, brought by Brad<strong>for</strong>d expanding beyond the<br />
academic vertical market. Enterprises should evaluate Brad<strong>for</strong>d's capabilities when<br />
NAC requirements are driven by diverse IT environments.<br />
Return to Top<br />
Strengths<br />
Ease of deployment is rated very high <strong>for</strong> <strong>Network</strong> Sentry. Brad<strong>for</strong>d's<br />
out-of-band approach and wide plat<strong>for</strong>m support eliminate many potential
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
9 of 18 19/8/2553 15:31<br />
problems.<br />
Brad<strong>for</strong>d's experience in diverse university requirements puts it in a good<br />
position <strong>for</strong> satisfying enterprise needs to use NAC to secure the use of<br />
employee-owned PCs and smartphones.<br />
Brad<strong>for</strong>d consistently gets high marks <strong>for</strong> customer support and overall<br />
corporate responsiveness.<br />
In the past year, Brad<strong>for</strong>d had a number of wins outside of the university<br />
vertical market, some displacing other incumbent NAC vendors.<br />
Return to Top<br />
Cautions<br />
The ending of the OEM relationship with Aruba will slow Brad<strong>for</strong>d's<br />
progress in expanding beyond the academic vertical market.<br />
Like all other NAC pure-play vendors, Brad<strong>for</strong>d will be increasingly<br />
squeezed by NAC solutions offered by incumbent network infrastructure and<br />
EPP software vendors.<br />
Brad<strong>for</strong>d users consistently request improvements in <strong>Network</strong> Sentry's user<br />
interface and reporting.<br />
Return to Top<br />
Check Point Software Technologies<br />
Check Point Software Technologies is one of the largest pure-play security<br />
companies, with a large firewall and VPN gateway installed base, and a strong<br />
global channel. Check Point has been slowly accumulating the component pieces<br />
to compete in the EPP plat<strong>for</strong>m market, and is gradually building on its installed<br />
base from the acquisition of Pointsec in 2006. Thus, Check Point's NAC<br />
capabilities are features that can be enabled by enterprises using its network<br />
security, endpoint security products or both, rather than a stand-alone NAC<br />
offering. Check Point's planned support <strong>for</strong> advanced guest management<br />
capabilities and its embrace of industry standards gained it an increased vision<br />
rating this year. Check Point's offerings should be considered by enterprises using<br />
Check Point's network security and/or endpoint security products.<br />
Return to Top<br />
Strengths<br />
Check Point Cooperative En<strong>for</strong>cement works well across Checkpoint network<br />
security products and third-party Open Plat<strong>for</strong>m <strong>for</strong> Security (OPSEC)<br />
partner technology.<br />
Check Point offers both a dissolvable agent and the Abra USB-based<br />
"portable personality" device <strong>for</strong> securing access by unmanaged PCs.<br />
Check Point's installed base and global channel provide a strong<br />
competitive advantage, especially where the NAC deployment is remoteaccess-centric.<br />
Return to Top<br />
Cautions<br />
In the EPP plat<strong>for</strong>m market, Check Point competes against more-established<br />
solutions from McAfee, Sophos and Symantec, putting Check Point at a<br />
disadvantage in competitive endpoint-centric NAC deployments.<br />
Although Checkpoint has supported guest access through a captive portal<br />
approach, it has been slow to add advanced guest networking management<br />
capabilities.<br />
Return to Top<br />
Cisco<br />
Cisco's execution in the NAC market has not mirrored its success in the network<br />
infrastructure market. The most common complaint about Cisco's NAC solution is<br />
that it is too complex and too expensive. Cisco was slow to recognize and adapt<br />
to these deficiencies — thus, its backward movement along the Completeness of<br />
Vision axis. Cisco also lost points in its ability to execute, because many of its<br />
customers chose to implement competing NAC solutions. However, Cisco is<br />
shifting its NAC strategy, and if it executes well, it should remain a leader in the
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
10 of 18 19/8/2553 15:31<br />
NAC market. The two main elements of the renewed strategy are an increased<br />
focus on 802.1X <strong>for</strong> controlling guest access and a new NAC appliance that<br />
consolidates functionality that is presently distributed among multiple NAC<br />
appliances. Cisco customers should consider the new NAC appliances once these<br />
products become available. Gartner expects that the new solutions will be<br />
shipping be<strong>for</strong>e year-end 2010.<br />
Return to Top<br />
Strengths<br />
Cisco's renewed focus on 802.1X in wired networks will enable it to deliver<br />
basic and inexpensive guest network access, thereby addressing the<br />
primary NAC requirement <strong>for</strong> most enterprises.<br />
AnyConnect, which combines VPN, NAC and other security technologies into<br />
a single endpoint client, will help Cisco grow its installed base of NAC<br />
endpoint software. Cisco has a strong market share in the VPN market, and<br />
when its customers upgrade to AnyConnect, they will also be installing the<br />
embedded NAC software.<br />
The combination of Cisco's profiling solution (NAC Profiler) and its guest<br />
networking solution (NAC Guest Server) make <strong>for</strong> a strong approach to<br />
guest networking. NAC Profiler (Great Bay Software is the OEM provider)<br />
discovers and monitors nonauthenticating devices (<strong>for</strong> example, IP phones<br />
and printers), thereby easing the process of supporting endpoints that are<br />
non-NAC capable. NAC Guest Server (this technology is also licensed from<br />
an OEM provider) provisions guest accounts and monitors guest activity on<br />
the network. (Note: functionality from NAC Profiler and NAC Guest Server<br />
will be included in Cisco's new NAC appliance.)<br />
Cisco's long-term strategy of embedding identity awareness into its Catalyst<br />
switches (a component of its TrustSec strategy) will enable it to support<br />
identity policies more granularly and more flexibly than most of its NAC<br />
competitors.<br />
Return to Top<br />
Cautions<br />
Be<strong>for</strong>e making further investments in Cisco's current family of NAC<br />
appliances (NAC Appliance 33XX Series, NAC Profiler and NAC Guest<br />
Server), Cisco customers should wait <strong>for</strong> Cisco to publicly announce its<br />
plans to upgrade these solutions and offer investment protection.<br />
Although Cisco's updated TrustSec positioning is a good start, it still needs<br />
improvements to its NAC marketing and branding. For example, Cisco needs<br />
to clarify the role that Secure <strong>Access</strong> <strong>Control</strong> System (ACS) plays in its<br />
broader NAC strategy.<br />
Despite a stated partnership with Microsoft, dating back to 2004, Cisco still<br />
does not support the Microsoft NAP protocols or the equivalent TNC<br />
specifications. Thus, Cisco software is required on Windows desktops to<br />
per<strong>for</strong>m anything beyond the most basic endpoint baselining functionality.<br />
Return to Top<br />
Enterasys<br />
In 2008, the Gores Group purchased Siemens Enterprise Communications and<br />
merged it with Enterasys (which it already owned). Since then, Enterasys has<br />
struggled to gain market share (currently 1% to 2%) in the wired network<br />
infrastructure market, its core competency. Enterasys offers out-of-band (NAC<br />
Gateway) and in-line (NAC <strong>Control</strong>ler) components. The NAC <strong>Control</strong>ler enables<br />
NAC <strong>for</strong> older third-party switches that do not support 802.1X or RADIUS-based<br />
authentication. The Enterasys solution per<strong>for</strong>ms endpoint baselining via agents<br />
(permanent and dissolvable) and agentless technology. The primary usage case<br />
<strong>for</strong> Enterasys NAC is Enterasys switch and wireless LAN customers, although the<br />
solution is capable of supporting non-Enterasys environments.<br />
Return to Top<br />
Strengths<br />
Enterasys' main product strength remains the flow-based technology in its<br />
S-Series and N-Series switches. NAC policies can be applied <strong>for</strong> each<br />
unique flow (by tracking the source/destination address pairing). For<br />
example, granular policies can be established to implement bandwidth rate<br />
limits or trigger deep-packet inspection.
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
11 of 18 19/8/2553 15:31<br />
Enterasys' NAC management console has an integrated profiling capability,<br />
which automatically discovers and identifies all endpoints on the network.<br />
Enterasys has integrated its Dragon IPS, as well as third-party IPS<br />
solutions, with its NAC offering, so that it can quarantine endpoints that<br />
Dragon identifies as suspicious.<br />
Return to Top<br />
Cautions<br />
Its shrinking market share limits Enterasys' ability to grow its NAC<br />
business, particularly because it has had limited success in selling NAC to<br />
the broader market.<br />
For a network infrastructure vendor, Enterasys lacks operational and<br />
troubleshooting tools <strong>for</strong> managing an 802.1X environment.<br />
Return to Top<br />
ForeScout<br />
ForeScout is a network security pure-play company that offers the CounterACT<br />
NAC appliance and the CounterACT Edge security appliance. CounterACT is highly<br />
rated by users <strong>for</strong> ease of deployment and flexible en<strong>for</strong>cement scenarios.<br />
ForeScout's out-of-band approach simplifies moving from guest networking to<br />
baselining to en<strong>for</strong>cement, the common success pattern <strong>for</strong> NAC deployments.<br />
ForeScout had a number of new customer wins since the publication of the 2009<br />
NAC <strong>Magic</strong> <strong>Quadrant</strong>, with a strong presence at government agencies, gaining it<br />
an increase in its Ability to Execute rating. ForeScout should be considered by<br />
enterprises looking at NAC solutions that are not tied to network infrastructure or<br />
EPP software.<br />
Return to Top<br />
Strengths<br />
CounterACT is highly rated <strong>for</strong> ease of deployment and price/per<strong>for</strong>mance in<br />
large installations, and ForeScout consistently gets good ratings <strong>for</strong><br />
responsiveness and support.<br />
CounterACT provides strong support <strong>for</strong> the guest network and endpoint<br />
baselining use cases, and it provides basic support <strong>for</strong> role-based policies.<br />
CounterACT also supports post-connect NAC, via its IDS-like functionality.<br />
ForeScout customers tend to grow their deployment of CounterACT<br />
appliances and scale their NAC solutions quickly.<br />
ForeScout's visibility (as reflected by how often it appears on the shortlists<br />
of Gartner clients) has improved since 2009.<br />
Return to Top<br />
Cautions<br />
Although CounterACT's price/per<strong>for</strong>mance is strong across large<br />
installations, users report that ForeScout's management console needs<br />
ease-of-use improvements <strong>for</strong> large-scale implementations.<br />
Like all other NAC pure-play vendors, ForeScout will be increasingly<br />
squeezed by NAC solutions offered by incumbent network infrastructure and<br />
EPP software vendors.<br />
Return to Top<br />
HP (3Com)<br />
HP Identity Driven Manager is HP's lead offering in NAC. In April 2010, HP<br />
completed the acquisition of 3Com, along with H3C, the joint venture between<br />
Huawei and 3Com. H3C has an NAC solution, as did TippingPoint, which 3Com<br />
had previously acquired in 2005. Prior to these acquisitions, HP's NAC solution<br />
consisted of Identity Driven Manager and the ProCurve <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
800 appliance, which was based on technology licensed from StillSecure (via an<br />
OEM agreement). HP discontinued the ProCurve <strong>Network</strong> <strong>Access</strong> <strong>Control</strong> 800<br />
appliance in April 2010, and it recommends the StillSecure branded NAC offering<br />
as a replacement (StillSecure is an HP AllianceONE NAC Specialization Partner).<br />
Until HP articulates a coherent strategy and road map <strong>for</strong> its NAC products, we<br />
continue to rate it as a Niche Player in the market. Users of HP network
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
12 of 18 19/8/2553 15:31<br />
infrastructure technology should consider HP's NAC offering.<br />
Return to Top<br />
Strengths<br />
Identity Driven Manager is a plug-in to HP's ProCurve Manager Plus,<br />
simplifying NAC deployment <strong>for</strong> ProCurve wired and wireless network users.<br />
HP has tightly coupled Identity Driven Manager to Microsoft's NAP<br />
technology that is built into PCs running the XP SP3, Vista and Windows 7<br />
operating systems, easing NAC deployment <strong>for</strong> enterprises that have<br />
deployed these newer operating systems.<br />
As a large company with global support and significant R&D resources, and<br />
a good track record in supporting and driving industry standards, if HP<br />
chooses to focus on NAC as a key part of competing in the network<br />
infrastructure market, then it could become a major market factor.<br />
Return to Top<br />
Cautions<br />
Identity Driven Manager's integration to ProCurve puts it in direct<br />
competition with Cisco's NAC strategy. Although Gartner gives ProCurve a<br />
strong rating as a network infrastructure contender, Cisco's domination of<br />
the installed base is a major challenge to HP NAC adoption.<br />
HP's reliance on Microsoft NAP puts it at a disadvantage in environments<br />
with older Microsoft desktop operating systems (that do not support<br />
Microsoft NAP) and where consumerization demands are resulting in more<br />
use of PCs and smartphones that run non-Microsoft operating systems.<br />
Although HP has a large portfolio of security products, its overall strategy<br />
<strong>for</strong> security is unclear, and its NAC strategy and road map suffer as a result.<br />
Return to Top<br />
Impulse Point<br />
Impulse Point has shown growth in the higher education market, and also the<br />
K-12 sector, but it has not demonstrated an ability to penetrate the commercial<br />
enterprise market. Its strong vertical focus keeps it positioned in the Niche Players<br />
quadrant. En<strong>for</strong>cement is provided via ACLs at Layer 3 (<strong>for</strong> example, routers and<br />
switches), at Layer 4 (support is provided <strong>for</strong> Blue Coat proxies) or via firewall<br />
policies. This approach is suitable <strong>for</strong> some university environments, although it<br />
does not meet the en<strong>for</strong>cement requirements of most corporate environments,<br />
where en<strong>for</strong>cement is required at Layer 2 (at the LAN switch). Impulse Point<br />
delivers its solution as a managed service, which includes managing updates<br />
(patches and antivirus status) to its policy server and housing daily policy<br />
configuration backups. Safe Connect is available as an appliance or via software<br />
(it is certified to run in a virtualized VMware environment). Educational<br />
institutions dealing with heterogeneous endpoint environments should consider<br />
Impulse Point.<br />
Return to Top<br />
Strengths<br />
Safe Connect can be deployed quickly, because its Layer 3 approach to<br />
en<strong>for</strong>cement eliminates the need to test compatibility at Layer 2 (among an<br />
enterprise's LAN switches).<br />
Impulse Point provides a scalable and relatively inexpensive approach to<br />
NAC. In large environments (10,000 nodes and above), Impulse Point's<br />
pricing model is highly favorable.<br />
With several of its university customers, SafeConnect displaced its<br />
competitors' NAC equipment.<br />
Its endpoint agent provides continuous posture assessment and<br />
quarantining (agent-based self-en<strong>for</strong>cement). Many endpoint-based NAC<br />
solutions require scheduled posture assessment scans.<br />
Return to Top<br />
Cautions<br />
Safe Connect's Layer 3-based en<strong>for</strong>cement mechanism (ACLs on routers)<br />
makes it a poor choice <strong>for</strong> enterprises seeking to implement guest networks
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
13 of 18 19/8/2553 15:31<br />
in corporate environments. Endpoints are still able to gain access by<br />
connecting to a Layer 2 LAN switch. Impulse Point provides the option to<br />
integrate FreeRADIUS in the Safe Connect policy server to authenticate<br />
802.1X-enabled endpoints, although the solution is not competitive with<br />
other appliance-based RADIUS solutions that are more scalable and have<br />
better tools <strong>for</strong> troubleshooting failed authentications.<br />
Although its focus on NAC as a managed service shifts the daily support<br />
burden to Impulse Point, some of its customers have commented that<br />
product documentation quality is weak. In the most recent release, updated<br />
documentation was not available <strong>for</strong> several months after the product<br />
shipped.<br />
Outside the higher education market, Impulse Point suffers from low market<br />
visibility, because of its small size and its limited resources.<br />
Although Impulse Point has improved its reporting and graphical interface,<br />
its policy controls in the area of guest networking and its Windows patch<br />
management are weaker than many of its competitors.<br />
Return to Top<br />
InfoExpress<br />
InfoExpress is largely focused on the NAC market, although it also offers a<br />
personal firewall product. It is still a small company (fewer than 100 employees),<br />
but it was founded in 1993 and remains a "bootstrap" company — it has never<br />
needed to raise money from venture capitalists. In 2009, InfoExpress partnered<br />
with Alcatel-Lucent and integrated its technology with Alcatel-Lucent's LAN<br />
switches, wireless access points (from Aruba) and its VitalQIP Suite (which<br />
enables DHCP-based en<strong>for</strong>cement). Alcatel-Lucent is now a global reseller of<br />
InfoExpress solutions. Enterprises should evaluate InfoExpress' capabilities when<br />
NAC requirements are driven by diverse IT environments.<br />
Return to Top<br />
Strengths<br />
InfoExpress provides a broad array of deployment options <strong>for</strong> NAC.<br />
Persistent or dissolvable agents can be used to baseline endpoints. Its<br />
CyberGatekeeper appliances provide in-line and out-of-band en<strong>for</strong>cement<br />
<strong>for</strong> LAN, wireless LAN and VPN connections, and its policy server functions<br />
as a RADIUS proxy. InfoExpress' most popular NAC solution is its Dynamic<br />
NAC offering, which uses permanent agents to implement ARP-based<br />
en<strong>for</strong>cement of noncompliant endpoints.<br />
Dynamic NAC can be a cost-effective solution <strong>for</strong> organizations that have<br />
many sparsely populated branch offices, because it does not require<br />
additional hardware.<br />
InfoExpress' CyberGatekeeper NAC solution is a good complement to its<br />
personal firewall offering.<br />
Return to Top<br />
Cautions<br />
InfoExpress' policy management console lacks some of the user-friendly<br />
features (<strong>for</strong> example, drop-down menus and radio buttons) found in<br />
competitive offerings.<br />
Guest networking functionality is limited. Guest accounts must be<br />
provisioned on a RADIUS server or on Active Directory, and managing an<br />
exception list of endpoints is manually intensive.<br />
The company's technology differentiation has eroded as large competitors,<br />
such as McAfee and Symantec, have expanded their endpoint security<br />
solutions to include better personal firewalls and NAC support.<br />
Return to Top<br />
Insightix<br />
Insightix is a pure-play network visibility vendor with products branded under the<br />
Insightix Business Security Assurance (BSA) line. BSA Visibility is the main<br />
product, which uses a mixture of active and passive techniques to detect and<br />
profile devices connected to the network. Visibility greatly reduces the manual<br />
ef<strong>for</strong>t required to maintain a continuous and accurate inventory of everything<br />
connected to the network and the key attributes of each device. BSA NAC provides<br />
en<strong>for</strong>cement capabilities through ARP manipulation, while BSA Guest <strong>Access</strong>
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
14 of 18 19/8/2553 15:31<br />
<strong>Control</strong> provides a captive portal approach <strong>for</strong> allowing limited guest access.<br />
Insightix has improved its management and workflow capabilities and added<br />
integration to McAfee and Juniper environments, but its lack of visibility and<br />
limited large-scale deployments acted to offset these gains in the Ability to<br />
Execute and Completeness of Vision axes. Enterprises that have demand and<br />
funding <strong>for</strong> network discovery capabilities that later may be used as the<br />
foundation <strong>for</strong> broader NAC deployment should consider Insightix.<br />
Return to Top<br />
Strengths<br />
Ease of implementing discovery and baselining and the depth and accuracy<br />
of the profiling in<strong>for</strong>mation are Insightix's core strengths. Embracing the<br />
IF-MAP standard will help it increase partnerships with network<br />
infrastructure vendors that lack their own discovery capabilities.<br />
Insightix's en<strong>for</strong>cement technique is easy to deploy <strong>for</strong> organizations that<br />
are mostly interested in visibility and inventory, with limited quarantining<br />
requirements.<br />
Return to Top<br />
Cautions<br />
Insightix's visibility in North American and larger European companies is<br />
very limited, and it rarely appears on Gartner client shortlists in those<br />
geographies.<br />
Insightix's integration with remediation products and its support <strong>for</strong> guest<br />
access management are limited.<br />
Although Insightix can sell network visibility outside the NAC space, it will<br />
be increasingly squeezed in NAC opportunities by incumbent network<br />
infrastructure and EPP software vendors that embed NAC functionality.<br />
Return to Top<br />
Juniper<br />
Juniper has been an early promoter of NAC standards, and its Unified <strong>Access</strong><br />
<strong>Control</strong> (UAC) solution was one of the first to implement the TCG/TNC's protocols<br />
that enable NAC interoperability. Juniper has also been an early adopter of the<br />
TNC's IF-MAP specification, which creates an open and structured way <strong>for</strong> devices<br />
and users to share in<strong>for</strong>mation on a network. Juniper's success in selling UAC into<br />
large accounts and its <strong>for</strong>esight with regard to NAC interoperability have enabled<br />
it to remain in the Leaders quadrant, although it lost points overall in the<br />
Completeness of Vision and Ability to Execute axes. With regard to vision, Gartner<br />
believes that Juniper is missing opportunities by not targeting UAC more strongly<br />
as a solution <strong>for</strong> the Guest <strong>Network</strong> use case. With regard to its ability to execute,<br />
Juniper lost points because it needs to create stronger mind share and sales <strong>for</strong><br />
UAC among its installed base of enterprise customers. Juniper customers and<br />
enterprises that emphasize NAC interoperability due to diverse IT environments<br />
should consider Juniper's UAC solution.<br />
Return to Top<br />
Strengths<br />
Junos Pulse, which combines VPN, NAC and WAN acceleration technology<br />
into a single endpoint client, will help Juniper grow its installed base of<br />
NAC endpoint software. Juniper has strong market share in the VPN market,<br />
and when its customers upgrade to Junos Pulse, they will also be installing<br />
the embedded NAC software.<br />
Integrating Webroot anti-spyware, another component of Junos Pulse,<br />
enables Juniper to go beyond basic endpoint compliance checking to also<br />
assess whether an endpoint is infected with malware.<br />
UAC support is embedded in Juniper's firewall, IPS and Ethernet switch<br />
product families. This integrated approach enables Juniper components to<br />
en<strong>for</strong>ce device policies and/or identity policies (user policies), and makes<br />
UAC a good option <strong>for</strong> multiple NAC use cases.<br />
Juniper's support <strong>for</strong> Microsoft NAP enables it to provide basic endpoint<br />
baselining on Windows PCs without requiring the Junos Pulse agent.<br />
Return to Top
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
15 of 18 19/8/2553 15:31<br />
Cautions<br />
Feedback from some Juniper references reflects poorly on the ease of UAC<br />
deployment. Gartner received complaints about the deployment and<br />
manageability of the UAC client, and also received similar input regarding<br />
Juniper's RADIUS functionality.<br />
Juniper is too focused on selling the complete UAC solution, and has not<br />
leveraged its 802.1X support to gain a beachhead in accounts <strong>for</strong> guest<br />
networking.<br />
For a solution with a strong emphasis on identity-aware networking,<br />
Juniper's policy management console lacks some important features <strong>for</strong><br />
enabling guest access. For example, setting up time-based access requires<br />
custom filters (instead of radio buttons), and guest credentials cannot be<br />
automatically e-mailed or texted in advance.<br />
Return to Top<br />
McAfee<br />
As an EPP vendor with a strong set of network security products, McAfee is<br />
well-positioned to sell NAC into its installed base of ePolicy Orchestrator (ePO)<br />
customers. In addition to embedding NAC functionality into its EPP suites, McAfee<br />
also offers NAC as a stand-alone component. An optional software module <strong>for</strong><br />
McAfee's IPS appliance enables it to en<strong>for</strong>ce NAC policies. Non-IPS customers<br />
have the option of purchasing a stand-alone NAC appliance, which runs the same<br />
software but without the IPS functionality. McAfee had purchased the assets of<br />
failed NAC vendor Lockdown <strong>Network</strong>s, which would have enabled it to deliver an<br />
inexpensive NAC solution <strong>for</strong> the SMB market, but it appears to have abandoned<br />
that strategy. McAfee's <strong>Network</strong> User Behavior Analysis, a solution that it gained<br />
with its acquisition of Secure Computing, monitors user behavior on an enterprise<br />
network and could be deployed as part of a post-connect NAC project, although<br />
McAfee does not market it as an NAC offering. Even with its strengths in network<br />
security, McAfee has yet to demonstrate that it can consistently win large NAC<br />
deals in its installed base of ePO accounts, and Gartner has positioned it below<br />
the Ability to Execute line in the Visionaries quadrant. McAfee customers should<br />
evaluate its NAC solution.<br />
Return to Top<br />
Strengths<br />
McAfee's <strong>Network</strong> Security Manager (NSM) enables organizations to build<br />
and en<strong>for</strong>ce rich policies, including identity policies and location-based<br />
policies.<br />
The user interface <strong>for</strong> provisioning guest accounts is good and includes<br />
several options <strong>for</strong> notifying guests of the account credentials (<strong>for</strong> example,<br />
SMS and e-mail).<br />
McAfee has gained additional network security experience through its<br />
acquisition of Secure Computing, which should help it compete in NAC sales<br />
against other EPP vendors.<br />
Return to Top<br />
Cautions<br />
McAfee's N-450 NAC Appliance is available in only one size, and it is not<br />
cost-effective <strong>for</strong> small environments or small remote sites.<br />
McAfee's NAC solution lacks the ability to en<strong>for</strong>ce policy by configuring<br />
ACLs on LAN switches, a common feature in competing offerings.<br />
Return to Top<br />
Nevis <strong>Network</strong>s<br />
Nevis <strong>Network</strong>s appears <strong>for</strong> the first time in the NAC <strong>Magic</strong> <strong>Quadrant</strong>, although it<br />
also appeared in Gartner's NAC MarketScope in 2007 and 2008. Nevis went<br />
through a period of transition in 2009, after a management buy-out that resulted<br />
in the management team relocating to India, where the company already had a<br />
development center. Due to the uncertainty surrounding the company, Gartner did<br />
not include Nevis in the 2009 NAC <strong>Magic</strong> <strong>Quadrant</strong>. Nevis offers an in-line<br />
approach to NAC via two options — an Ethernet switch (Secure Switch<br />
LANen<strong>for</strong>cer) and a LAN appliance (LANen<strong>for</strong>cer) that is positioned between an<br />
edge switch and a core switch. Both products are based on Nevis' ASIC
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
16 of 18 19/8/2553 15:31<br />
technology, which has enabled it to cost-effectively integrate basic IPS<br />
capabilities in the LAN. Organizations that need the benefits of an in-line<br />
approach to NAC and can accept dealing with a geographically remote support<br />
organization should consider Nevis. Organizations that are located in India or<br />
China should consider Nevis.<br />
Return to Top<br />
Strengths<br />
Nevis' in-line positioning enables it to en<strong>for</strong>ce granular user-based policies<br />
by dropping and filtering packets — a flexible approach to adding identity<br />
awareness to the network.<br />
The IPS capabilities in the LANen<strong>for</strong>cer products enable strong post-connect<br />
NAC functionality, using both signature and anomaly-based detection.<br />
LANen<strong>for</strong>cers provide application detection and control capability <strong>for</strong><br />
applications that companies typically seek to limit, including instant<br />
messaging and other peer-to-peer applications, as well as gaming and<br />
streaming audio/video applications.<br />
Return to Top<br />
Cautions<br />
Outside of India and China, Nevis has a small presence and low market<br />
visibility.<br />
The requirement to deploy appliances in-line can be expensive, particularly<br />
in network topologies where the Nevis appliances are only partially used<br />
(<strong>for</strong> example, if many ports are left unused). Often, it is not cost-effective<br />
to deploy Nevis appliances in small remote offices or to en<strong>for</strong>ce NAC in<br />
VPNs.<br />
Despite its increased market penetration in India and China, Nevis will be<br />
challenged to sell its LAN switches and NAC appliances against established<br />
network infrastructure vendors, such as Cisco, HP and Juniper.<br />
Return to Top<br />
Sophos<br />
In May 2010, Apax Partners, a private equity firm, announced plans to acquire<br />
70% of Sophos. The deal gives Sophos additional financial backing, and should<br />
have limited impact on Sophos customers in 2010. Sophos offers two NAC<br />
solutions (both are based on technology from its 2007 acquisition of End<strong>for</strong>ce).<br />
Sophos' EPP suite, Endpoint Security and <strong>Control</strong>, provides basic NAC policy,<br />
reporting and en<strong>for</strong>cement capabilities. Sophos' NAC Advanced solution, which<br />
requires a separate agent and management console, provides more-advanced<br />
features, such as custom policy creation, stronger reporting capabilities and more<br />
en<strong>for</strong>cement options (including support <strong>for</strong> 802.1X). Sophos' NAC solutions are a<br />
reasonable choice <strong>for</strong> Sophos customers. Larger customers, with<br />
more-sophisticated needs, should evaluate the NAC Advanced solution.<br />
Return to Top<br />
Strengths<br />
Basic NAC functions are embedded (at no extra charge) in Sophos' Endpoint<br />
Security and <strong>Control</strong> suite, although this version does not support VPN<br />
environments (the NAC Advanced Solution is required <strong>for</strong> VPNs).<br />
The Sophos policy server acts as a RADIUS proxy and provides very flexible<br />
and granular support (<strong>for</strong> example, configuring vendor-specific attributes<br />
and subattributes) <strong>for</strong> interoperating with policy en<strong>for</strong>cement points.<br />
Return to Top<br />
Cautions<br />
Sophos is behind its major EPP suite competitors (McAfee and Symantec) in<br />
delivering an integrated NAC and EPP solution. Its NAC Advanced solution<br />
still requires a separate agent and management console, whereas Symantec<br />
and McAfee offer integrated NAC agents with their EPP solutions.<br />
Although Sophos has made progress in selling to larger accounts, the<br />
majority of its client base are SMB customers and are less likely to adopt its<br />
enterprise-class Advanced NAC offering.
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
17 of 18 19/8/2553 15:31<br />
Customer references said that Sophos' reporting capabilities are<br />
cumbersome and that its management dashboard does not provide enough<br />
drill-down troubleshooting capabilities.<br />
Return to Top<br />
StillSecure<br />
StillSecure sells IPS, NAC and vulnerability management products. In 2009,<br />
StillSecure acquired ProtectPoint, a small managed security service provider, to<br />
enter the security services business, but it does not offer managed NAC services.<br />
The StillSecure Safe <strong>Access</strong> NAC product offers a full-time agent, a dissolvable<br />
agent and an agentless assessment option. StillSecure has licensed its technology<br />
to network infrastructure vendors Extreme <strong>Network</strong>s, HP and Novell. Safe <strong>Access</strong><br />
should be considered in NAC deployments where heterogeneous networks are in<br />
use and where organizations want the flexibility of agent or agentless baselining<br />
options.<br />
Return to Top<br />
Strengths<br />
Safe <strong>Access</strong> supports a broad range of endpoint baselining and en<strong>for</strong>cement<br />
methods.<br />
StillSecure Safe <strong>Access</strong> has received Common Criteria certification, which<br />
simplifies procurement <strong>for</strong> defense and government agencies.<br />
References consistently quote the quality of StillSecure's technical support<br />
and Safe <strong>Access</strong> integration with LAN switches as leading reasons <strong>for</strong><br />
selecting Safe <strong>Access</strong>.<br />
Return to Top<br />
Cautions<br />
Safe <strong>Access</strong> has limited support <strong>for</strong> advanced guest network management<br />
functions. These features are on StillSecure's road map <strong>for</strong> 2010.<br />
As a relatively small security vendor, StillSecure's resources are spread<br />
across three product areas and the new management security services<br />
initiative.<br />
Return to Top<br />
Symantec<br />
Symantec's <strong>Network</strong> <strong>Access</strong> <strong>Control</strong> product consists of NAC agent capabilities<br />
integrated into Symantec's Endpoint Protection software, managed by the same<br />
Symantec Endpoint Protection manager. Like other EPP vendors, Symantec's<br />
strength in NAC is largely based on the capabilities of its Endpoint Protect agent,<br />
but it also supports a dissolvable agent and an agentless approach with an<br />
optional scanner. In 2010, Symantec acquired Gideon Technologies, and<br />
Symantec intends to integrate Gideon's SecureFusion vulnerability scanning into<br />
Symantec NAC by year-end 2010. Symantec also offers a Symantec NAC "Starter<br />
Edition" that does not offer 802.1X or DHCP en<strong>for</strong>cement. Symantec lost points in<br />
vision and moved into the Challengers quadrant, mainly because its support <strong>for</strong><br />
the guest network use case remains weak. Symantec NAC should be considered<br />
when Symantec is the incumbent desktop EPP vendor.<br />
Return to Top<br />
Strengths<br />
Symantec's share in the EPP market enables it to aggressively price NAC as<br />
an integrated capability. Where Symantec's Altiris desktop management<br />
product is also in use, Symantec has a very strong story <strong>for</strong> remediating<br />
noncompliant endpoints.<br />
Symantec's dissolvable agent and in-line VPN en<strong>for</strong>cement capabilities are<br />
given strong marks by references.<br />
Symantec's NAC status display is effective and provides a strong capability<br />
<strong>for</strong> rapid drill-down into endpoint status.<br />
Return to Top
<strong>Magic</strong> <strong>Quadrant</strong> <strong>for</strong> <strong>Network</strong> <strong>Access</strong> <strong>Control</strong><br />
http://www.gartner.com/technology/media-products/reprints/j...<br />
18 of 18 19/8/2553 15:31<br />
Cautions<br />
Users still report installation as being cumbersome and complex. Symantec<br />
tools <strong>for</strong> importing device in<strong>for</strong>mation and easing NAC startup are basic.<br />
Symantec's support <strong>for</strong> guest network administration is limited. Enhanced<br />
capabilities in this area are on Symantec's 2011 road map.<br />
Symantec's visibility in NAC is lower than its EPP market share would<br />
predict. This is likely due to Symantec's attempts recently to diversify into<br />
storage and system management, diluting its visibility in NAC-specific<br />
opportunities.<br />
Return to Top<br />
Trustwave<br />
Trustwave is a large Payment Card Industry Qualified Security Assessor (QSA) and<br />
security service provider that entered the NAC market in 2009 via its acquisition<br />
of Mirage <strong>Network</strong>s. Trustwave Enterprise NAC provides the full set of NAC<br />
functions using an out-of-band, clientless approach with ARP manipulation <strong>for</strong><br />
quarantining. Trustwave also offers NAC appliances with limited functionality <strong>for</strong><br />
smaller organizations, as well as a managed NAC service. Trustwave has made<br />
additional acquisitions in security in<strong>for</strong>mation and event management (SIEM),<br />
DLP, and mobile data protection to broaden its managed service offerings and<br />
increase its ef<strong>for</strong>ts to be visible outside the PCI compliance space. Trustwave is<br />
still primarily a service vendor and not a product vendor. It moved into the Niche<br />
Players quadrant due to its focus on the retail market and on PCI compliance.<br />
Trustwave moved upward on the Ability to Execute axis due to its rapid growth<br />
and its plans to broaden beyond the retail vertical industry. Trustwave NAC<br />
offerings should be evaluated by enterprises looking to meet PCI requirements,<br />
and those where a low cost of entry and minimal integration to third-party<br />
products are required.<br />
Return to Top<br />
Strengths<br />
References continually quote ease of deployment and low cost as the<br />
primary factors <strong>for</strong> selecting Trustwave NAC.<br />
Trustwave's QSA strength and broad business relationships with credit card<br />
payment acquirers/processors give it an edge in selling managed NAC<br />
services to merchants as part of a larger bundle of Trustwave services to<br />
reach PCI compliance.<br />
Trustwave NAC has received Common Criteria certification, which simplifies<br />
procurement <strong>for</strong> defense and government agencies.<br />
Return to Top<br />
Cautions<br />
Trustwave NAC offers a limited set of en<strong>for</strong>cement options and guest<br />
networking support.<br />
Because Trustwave has acquired many security technologies and offers a<br />
broad range of its own services, Trustwave NAC has a shortlist of resellers<br />
and has limited integration to third-party security products, such as SIEM or<br />
remediation.<br />
Trustwave is rarely mentioned by Gartner clients outside of the context of<br />
PCI-related services. To attack the broader market, and build up a base of<br />
users that drive product features that are beyond PCI requirements,<br />
Trustwave will need to invest in building out enterprise product support<br />
capabilities.<br />
Return to Top<br />
© 2010 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner,<br />
Inc. or its affiliates. Reproduction and distribution of this publication in any <strong>for</strong>m without prior written<br />
permission is <strong>for</strong>bidden. The in<strong>for</strong>mation contained herein has been obtained from sources believed to be<br />
reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such<br />
in<strong>for</strong>mation. Although Gartner's research may discuss legal issues related to the in<strong>for</strong>mation technology<br />
business, Gartner does not provide legal advice or services and its research should not be construed or<br />
used as such. Gartner shall have no liability <strong>for</strong> errors, omissions or inadequacies in the in<strong>for</strong>mation<br />
contained herein or <strong>for</strong> interpretations thereof. The opinions expressed herein are subject to change<br />
without notice.