Accenture-Cyber-Security-Leap-2015-Report
Accenture-Cyber-Security-Leap-2015-Report
Accenture-Cyber-Security-Leap-2015-Report
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
THEME 5<br />
<strong>Security</strong> technologies that support <strong>Leap</strong>frog companies<br />
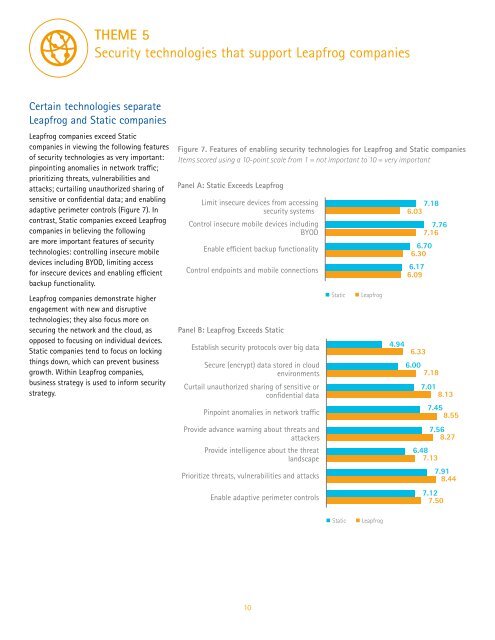
Certain technologies separate<br />
<strong>Leap</strong>frog and Static companies<br />
<strong>Leap</strong>frog companies exceed Static<br />
companies in viewing the following features<br />
of security technologies as very important:<br />
pinpointing anomalies in network traffic;<br />
prioritizing threats, vulnerabilities and<br />
attacks; curtailing unauthorized sharing of<br />
sensitive or confidential data; and enabling<br />
adaptive perimeter controls (Figure 7). In<br />
contrast, Static companies exceed <strong>Leap</strong>frog<br />
companies in believing the following<br />
are more important features of security<br />
technologies: controlling insecure mobile<br />
devices including BYOD, limiting access<br />
for insecure devices and enabling efficient<br />
backup functionality.<br />
<strong>Leap</strong>frog companies demonstrate higher<br />
engagement with new and disruptive<br />
technologies; they also focus more on<br />
securing the network and the cloud, as<br />
opposed to focusing on individual devices.<br />
Static companies tend to focus on locking<br />
things down, which can prevent business<br />
growth. Within <strong>Leap</strong>frog companies,<br />
business strategy is used to inform security<br />
strategy.<br />
Figure 7. Features of enabling security technologies for <strong>Leap</strong>frog and Static companies<br />
Items scored using a 10-point scale from 1 = not important to 10 = very important<br />
Panel A: Static Exceeds <strong>Leap</strong>frog<br />
Limit insecure devices from accessing<br />
security systems<br />
Control insecure mobile devices including<br />
BYOD<br />
Enable efficient backup functionality<br />
Control endpoints and mobile connections<br />
Panel B: <strong>Leap</strong>frog Exceeds Static<br />
Establish security protocols over big data<br />
Secure (encrypt) data stored in cloud<br />
environments<br />
Curtail unauthorized sharing of sensitive or<br />
confidential data<br />
Pinpoint anomalies in network traffic<br />
Provide advance warning about threats and<br />
attackers<br />
Provide intelligence about the threat<br />
landscape<br />
Prioritize threats, vulnerabilities and attacks<br />
Enable adaptive perimeter controls<br />
Static<br />
<strong>Leap</strong>frog<br />
6.03 7.18<br />
7.76<br />
7.16<br />
6.70<br />
6.30<br />
6.17<br />
6.09<br />
4.94<br />
6.33<br />
6.00<br />
7.18<br />
7.01<br />
8.13<br />
7.45<br />
8.55<br />
7.56<br />
8.27<br />
6.48<br />
7.13<br />
7.91<br />
8.44<br />
7.12<br />
7.50<br />
Static<br />
<strong>Leap</strong>frog<br />
10