2007 Issue 2 - Raytheon
2007 Issue 2 - Raytheon
2007 Issue 2 - Raytheon
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Feature<br />
Comprehensive Mission Assurance<br />
involves the disciplined application<br />
of systems engineering, thorough<br />
risk management, superior quality and<br />
sound management principles to achieve<br />
mission success. In a DoD network-centric<br />
environment, the warfighter is faced with<br />
both wired and wireless network–based<br />
threats. To mitigate wireless threats, innovative<br />
software technologies can be applied<br />
to identify wireless attacks and perform risk<br />
management. One such technology is the<br />
wireless honeypot.<br />
A honeypot is an information system<br />
resource whose purpose is to attract attackers,<br />
provide them with misinformation,<br />
cause confusion and monitor their actions.<br />
Even more importantly, a honeypot gathers<br />
valuable information to determine if a<br />
threat exists, and then provides details to<br />
help mitigation of these threats. A wireless<br />
version of a honeypot entices its attackers<br />
through a simulated wireless access point.<br />
<strong>Raytheon</strong> Network Centric Systems in St.<br />
Petersburg, Fla., recently sponsored a wireless<br />
honeypot research project at the<br />
University of Florida to help address wireless<br />
threats. The goal of the project, which was<br />
dubbed “The Hive,” was to design, build<br />
and test a simulated environment for a<br />
wireless networked system, or honeypot.<br />
In order to track and log suspicious nodes<br />
and traffic in mobile environments, the Hive<br />
research team developed a wireless honeypot<br />
as a live Linux bootable mini-CD. The<br />
Hive Linux is a Live-CD version of Debian<br />
Linux that was scaled down for operating<br />
system security, and contains the tools<br />
needed to run a standalone wireless honeypot<br />
with virtual services. It is currently available<br />
at the Hive’s project website 1 .<br />
14 <strong>2007</strong> ISSUE 2 RAYTHEON TECHNOLOGY TODAY<br />
Wireless<br />
Honeypots<br />
Innovative software technologies<br />
to identify wireless attacks<br />
and perform risk management<br />
Using a Hive Linux CD, any personal computer<br />
(including laptops) can easily be<br />
turned into a wireless honeypot. The experimental<br />
system operates on the IEEE<br />
802.11g wireless standard and instantiates<br />
a honeypot as a simulated wireless access<br />
point with tracking capabilities.<br />
The Hive honeypot runs Honeyd, a GNU<br />
Public License (GPL) open source honeypot<br />
program. Honeyd is described on its website<br />
as “… a small daemon that runs on<br />
both UNIX-like and Windows platforms. It is<br />
used to create multiple virtual honeypots<br />
on a single machine. Entire networks can<br />
be simulated using Honeyd. Honeyd can be<br />
configured to run a range of services like<br />
FTP, HTTP or SMTP. Furthermore, a personality<br />
can be configured to simulate a certain<br />
operating system. Honeyd allows a single host<br />
to claim as many as 65536 IP addresses.” 2<br />
The Hive lures its attacker by broadcasting a<br />
modifiable service set identifier (SSID) over<br />
the network. As an attacker attempts to<br />
connect to the honeypot, its Dynamic Host<br />
Configuration Protocol (DHCP) assigns the<br />
attacker an Internet Protocol (IP) address so<br />
that the attacker is placed on a simulated<br />
network. For the proof of concept, it was<br />
important to allow the attacker to see and<br />
gain access to the network. (An encrypted<br />
and secured wireless network would make<br />
the establishment of a network connection<br />
far more difficult, but may lure the more<br />
experienced attacker.)<br />
One of the first things that an attacker may<br />
do is to “fingerprint” computers that are<br />
local to their subnet. This can be done by<br />
port-scanning local nodes. In our case, the<br />
attacker port-scans the honeypot’s virtual<br />
services. The system tells the attacker that<br />
ports 22, 23, 80 and 110 are open, while<br />
Honeyd logs the probe. When an attacker<br />
connects to port 22 secure shell (SSH) or<br />
port 23 (Telnet), an authentication script is<br />
executed. The attacker may try a brute<br />
force attack to guess username and password<br />
combinations; such an attack can be<br />
done easily with a program named Hydra 3 ,<br />
and all connection attempts can be logged.<br />
Once the attacker gains access, all commands<br />
entered are logged. This connection<br />
is similarly made for the virtual services of<br />
port 80 Web and port 110 Post Office<br />
Protocol 3 (POP3).<br />
The honeypot itself is composed of a Linux<br />
operating system running a DHCP server,<br />
HostAP, Honeyd, and Sebek with Syslog.<br />
HostAP is a driver for Prism2-based wireless<br />
client cards that allows them to appear and<br />
act as a wireless access point. Sebek 4 is a<br />
data capture tool designed to capture the<br />
attacker’s activities on a honeypot, without<br />
their knowledge. Syslog is the system logger,<br />
which is similar to the Event Viewer in<br />
Microsoft ® Windows.<br />
The Hive was able to integrate and test the<br />
DCHP server, some scripts, the logging with<br />
Sebek, Honeyd, Syslog and the wireless<br />
access point emulation. This integration cre-<br />
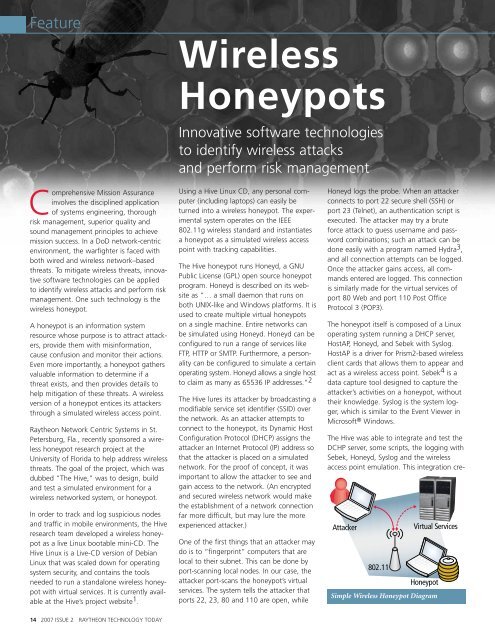
Attacker<br />
802.11<br />
Virtual Services<br />
Honeypot<br />
Simple Wireless Honeypot Diagram