IPv6 Security
IPv6 Security
IPv6 Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
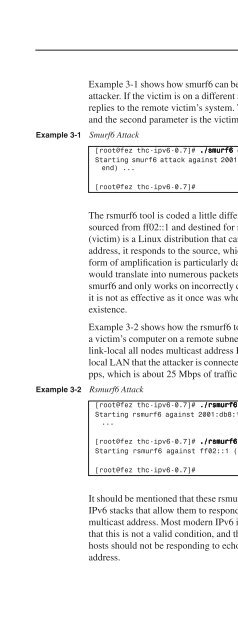
Large-Scale Internet Threats 75Example 3-1Example 3-1 shows how smurf6 can be used to affect a computer on the same subnet as theattacker. If the victim is on a different segment, the systems on this segment send the echoreplies to the remote victim’s system. The first parameter is the local attacker’s interface,and the second parameter is the victim’s <strong>IPv6</strong> address.Smurf6 Attack[root@fez thc-ipv6-0.7]# ./smurf6 eth0 2001:db8:11:0:b0f7:dd82:220:498bStarting smurf6 attack against 2001:db8:11:0:b0f7:dd82:220:498b (Press Control-C toend) ...[root@fez thc-ipv6-0.7]#Example 3-2The rsmurf6 tool is coded a little differently. It sends ICMPv6 echo reply packets that aresourced from ff02::1 and destined for remote computers. If the destination computer(victim) is a Linux distribution that can respond to packets sourced from a multicastaddress, it responds to the source, which causes a traffic flood on the remote LAN. Thisform of amplification is particularly dangerous because each packet generated by rsmurf6would translate into numerous packets on the remote LAN. Rsmurf6 is like a reversesmurf6 and only works on incorrectly coded implementations of the <strong>IPv6</strong> stack. Therefore,it is not as effective as it once was when more vulnerable operating systems were inexistence.Example 3-2 shows how the rsmurf6 tool can be used. The first part of the example targetsa victim’s computer on a remote subnet. The second part of the example is destined for thelink-local all nodes multicast address FF02::1 and essentially denies service to the entirelocal LAN that the attacker is connected to. Even the smallest systems can generate 25,000pps, which is about 25 Mbps of traffic to all hosts.Rsmurf6 Attack[root@fez thc-ipv6-0.7]# ./rsmurf6 -r eth0 2001:db8:12:0:a00:46ff:fe51:9e46Starting rsmurf6 against 2001:db8:12:0:a00:46ff:fe51:9e46 (Press Control-C to end)...[root@fez thc-ipv6-0.7]# ./rsmurf6 -r eth0 ff02::1Starting rsmurf6 against ff02::1 (Press Control-C to end) ...[root@fez thc-ipv6-0.7]#It should be mentioned that these rsmurf6 attacks are only effective on computers that have<strong>IPv6</strong> stacks that allow them to respond to an ICMPv6 packet that was sourced from amulticast address. Most modern <strong>IPv6</strong> implementations are intelligent enough to recognizethat this is not a valid condition, and they simply drop the packets. In other words, <strong>IPv6</strong>hosts should not be responding to echo request packets destined to a multicast groupaddress.