Prototype Nation
ZekcFC
ZekcFC
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
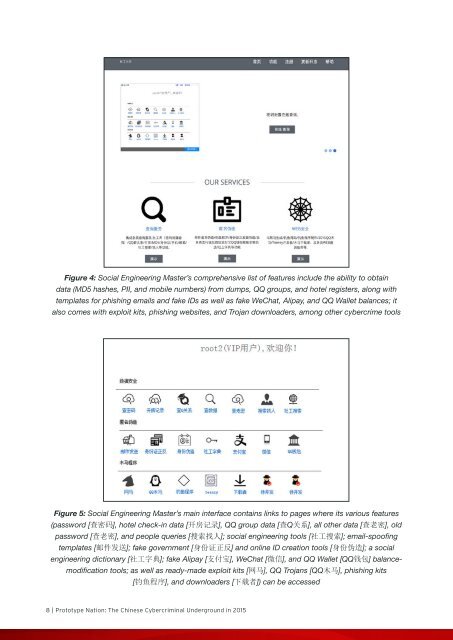
Figure 4: Social Engineering Master’s comprehensive list of features include the ability to obtain<br />
data (MD5 hashes, PII, and mobile numbers) from dumps, QQ groups, and hotel registers, along with<br />
templates for phishing emails and fake IDs as well as fake WeChat, Alipay, and QQ Wallet balances; it<br />
also comes with exploit kits, phishing websites, and Trojan downloaders, among other cybercrime tools<br />
Figure 5: Social Engineering Master’s main interface contains links to pages where its various features<br />
(password [ 查 密 码 ], hotel check-in data [ 开 房 记 录 ], QQ group data [ 查 Q 关 系 ], all other data [ 查 老 密 ], old<br />
password [ 查 老 密 ], and people queries [ 搜 索 找 人 ]; social engineering tools [ 社 工 搜 索 ]; email-spoofing<br />
templates [ 邮 件 发 送 ]; fake government [ 身 份 证 正 反 ] and online ID creation tools [ 身 份 伪 造 ]; a social<br />
engineering dictionary [ 社 工 字 典 ]; fake Alipay [ 支 付 宝 ], WeChat [ 微 信 ], and QQ Wallet [QQ 钱 包 ] balancemodification<br />
tools; as well as ready-made exploit kits [ 网 马 ], QQ Trojans [QQ 木 马 ], phishing kits<br />
[ 钓 鱼 程 序 ], and downloaders [ 下 载 者 ]) can be accessed<br />
8 | <strong>Prototype</strong> <strong>Nation</strong>: The Chinese Cybercriminal Underground in 2015