A Tight Bound for EMAC - CWI
A Tight Bound for EMAC - CWI
A Tight Bound for EMAC - CWI
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
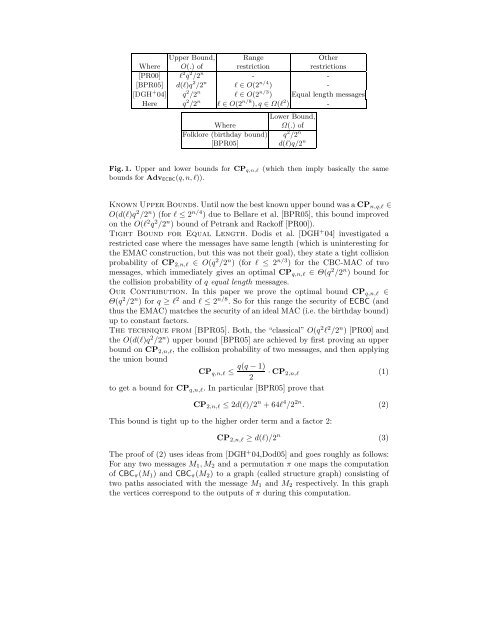
Upper <strong>Bound</strong>, Range Other<br />
Where O(.) of restriction restrictions<br />
[PR00] ℓ 2 q 2 /2 n<br />
- -<br />
[BPR05] d(ℓ)q 2 /2 n<br />
ℓ ∈ O(2 n/4 ) -<br />
[DGH + 04] q 2 /2 n<br />
ℓ ∈ O(2 n/3 ) Equal length messages<br />
Here q 2 /2 n<br />
ℓ ∈ O(2 n/8 ),q ∈ Ω(ℓ 2 ) -<br />
Lower <strong>Bound</strong>,<br />
Where Ω(.) of<br />
Folklore (birthday bound) q 2 /2 n<br />
[BPR05] d(ℓ)q/2 n<br />
Fig. 1. Upper and lower bounds <strong>for</strong> CPq,n,ℓ (which then imply basically the same<br />
bounds <strong>for</strong> AdvECBC(q, n, ℓ)).<br />
Known Upper <strong>Bound</strong>s. Until now the best known upper bound was a CPn,q,ℓ ∈<br />
O(d(ℓ)q2 /2n )(<strong>for</strong>ℓ≤2n/4 ) due to Bellare et al. [BPR05], this bound improved<br />
on the O(ℓ2q2 /2n ) bound of Petrank and Rackoff [PR00]).<br />
<strong>Tight</strong> <strong>Bound</strong> <strong>for</strong> Equal Length. Dodis et al. [DGH + 04] investigated a<br />
restricted case where the messages have same length (which is uninteresting <strong>for</strong><br />
the <strong>EMAC</strong> construction, but this was not their goal), they state a tight collision<br />
probability of CP2,n,ℓ ∈ O(q2 /2n )(<strong>for</strong>ℓ≤2n/3 ) <strong>for</strong> the CBC-MAC of two<br />
messages, which immediately gives an optimal CPq,n,ℓ ∈ Θ(q2 /2n ) bound <strong>for</strong><br />
the collision probability of q equal length messages.<br />
Our Contribution. In this paper we prove the optimal bound CPq,n,ℓ ∈<br />
Θ(q2 /2n )<strong>for</strong>q≥ℓ2 and ℓ ≤ 2n/8 . So <strong>for</strong> this range the security of ECBC (and<br />
thus the <strong>EMAC</strong>) matches the security of an ideal MAC (i.e. the birthday bound)<br />
up to constant factors.<br />
The technique from [BPR05]. Both, the “classical” O(q2ℓ2 /2n )[PR00]and<br />
the O(d(ℓ)q2 /2n ) upper bound [BPR05] are achieved by first proving an upper<br />
bound on CP2,n,ℓ, the collision probability of two messages, and then applying<br />
the union bound<br />
q(q − 1)<br />
CPq,n,ℓ ≤ · CP2,n,ℓ<br />
(1)<br />
2<br />
to get a bound <strong>for</strong> CPq,n,ℓ. In particular [BPR05] prove that<br />
CP2,n,ℓ ≤ 2d(ℓ)/2 n +64ℓ 4 /2 2n . (2)<br />
This bound is tight up to the higher order term and a factor 2:<br />
CP2,n,ℓ ≥ d(ℓ)/2 n<br />
The proof of (2) uses ideas from [DGH + 04,Dod05] and goes roughly as follows:<br />
For any two messages M1,M2 and a permutation π one maps the computation<br />
of CBCπ(M1) andCBCπ(M2) to a graph (called structure graph) consisting of<br />
two paths associated with the message M1 and M2 respectively. In this graph<br />
the vertices correspond to the outputs of π during this computation.<br />
(3)