You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
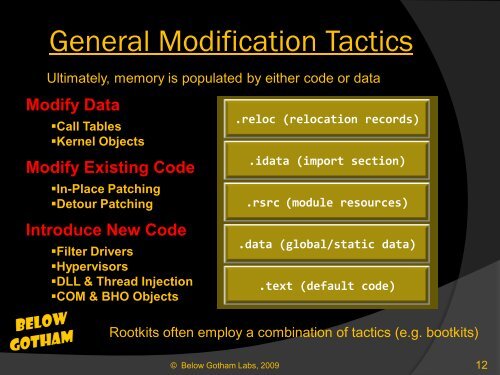
General Modification Tactics<br />
Ultimately, memory is populated by either code or data<br />
Modify Data<br />
Call Tables<br />
Kernel Objects<br />
Modify Existing Code<br />
In-Place Patching<br />
Detour Patching<br />
Introduce New Code<br />
Filter Drivers<br />
Hypervisors<br />
DLL & Thread Injection<br />
COM & BHO Objects<br />
© <strong>Below</strong> <strong>Gotham</strong> <strong>Labs</strong>, 2009<br />
.reloc (relocation records)<br />
.idata (import section)<br />
.rsrc (module resources)<br />
.data (global/static data)<br />
.text (default code)<br />
<strong>Rootkit</strong>s often employ a combination of tactics (e.g. bootkits)<br />
12