Goals and Objectives: Implementation Matrix As part of the Shared ...
Goals and Objectives: Implementation Matrix As part of the Shared ...
Goals and Objectives: Implementation Matrix As part of the Shared ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
5.8<br />
communications, electronic processing <strong>of</strong> personnel assignments (eRPA)<br />
that is integrated with a position control system (PCS).<br />
Explore <strong>the</strong> implementation <strong>of</strong> a workflow system that allows electronic<br />
approval <strong>of</strong> submitted forms.<br />
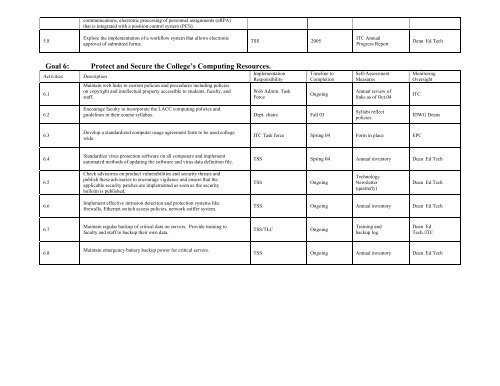
Goal 6: Protect <strong>and</strong> Secure <strong>the</strong> College’s Computing Resources.<br />
Activities Description<br />
6.1<br />
6.2<br />
6.3<br />
6.4<br />
6.5<br />
6.6<br />
6.7<br />
6.8<br />
Maintain web links to current policies <strong>and</strong> procedures including policies<br />
on copyright <strong>and</strong> intellectual property accessible to students, faculty, <strong>and</strong><br />
staff.<br />
Encourage faculty to incorporate <strong>the</strong> LACC computing policies <strong>and</strong><br />
guidelines in <strong>the</strong>ir course syllabus.<br />
Develop a st<strong>and</strong>ardized computer usage agreement form to be used college<br />
wide.<br />
St<strong>and</strong>ardize virus protection s<strong>of</strong>tware on all computers <strong>and</strong> implement<br />
automated methods <strong>of</strong> updating <strong>the</strong> s<strong>of</strong>tware <strong>and</strong> virus data definition file.<br />
Check advisories on product vulnerabilities <strong>and</strong> security threats <strong>and</strong><br />
publish <strong>the</strong>se advisories to encourage vigilance <strong>and</strong> ensure that <strong>the</strong><br />
applicable security patches are implemented as soon as <strong>the</strong> security<br />
bulletin is published.<br />
Implement effective intrusion detection <strong>and</strong> protection systems like<br />
firewalls, E<strong>the</strong>rnet switch access policies, network sniffer system.<br />
Maintain regular backup <strong>of</strong> critical data on servers. Provide training to<br />
faculty <strong>and</strong> staff to backup <strong>the</strong>ir own data.<br />
Maintain emergency battery backup power for critical servers.<br />
TSS 2005<br />
<strong>Implementation</strong><br />
Responsibility<br />
Web Admin. Task<br />
Force<br />
Timeline to<br />
Completion<br />
Ongoing<br />
Dept. chairs Fall 03<br />
ITC Annual<br />
Progress Report<br />
Self-<strong>As</strong>sessment<br />
Measures<br />
Annual review <strong>of</strong><br />
links as <strong>of</strong> Oct.04<br />
Syllabi reflect<br />
policies<br />
ITC Task force Spring 04 Form in place EPC<br />
Dean Ed Tech<br />
Monitoring<br />
Oversight<br />
ITC<br />
IDWG Deans<br />
TSS Spring 04 Annual inventory Dean Ed Tech<br />
TSS Ongoing<br />
Technology<br />
Newsletter<br />
(quarterly)<br />
Dean Ed Tech<br />
TSS Ongoing Annual inventory Dean Ed Tech<br />
TSS/TLC Ongoing<br />
Training <strong>and</strong><br />
backup log<br />
Dean Ed<br />
Tech./ITC<br />
TSS Ongoing Annual inventory Dean Ed Tech