PI System and NERC CIP Security PART II - OSIsoft
PI System and NERC CIP Security PART II - OSIsoft
PI System and NERC CIP Security PART II - OSIsoft
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
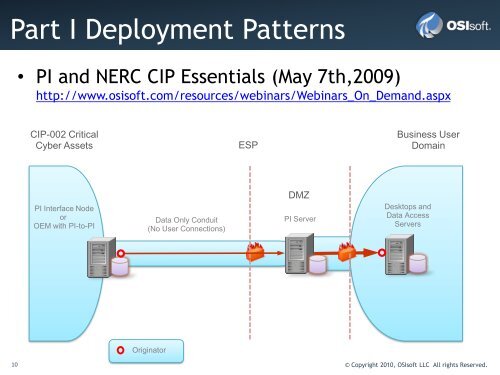
Part I Deployment Patterns<br />
• <strong>PI</strong> <strong>and</strong> <strong>NERC</strong> <strong>CIP</strong> Essentials (May 7th,2009)<br />
http://www.osisoft.com/resources/webinars/Webinars_On_Dem<strong>and</strong>.aspx<br />
<strong>CIP</strong>-002 Critical<br />
Cyber Assets<br />
<strong>PI</strong> Interface Node<br />
or<br />
OEM with <strong>PI</strong>-to-<strong>PI</strong><br />
Data Only Conduit<br />
(No User Connections)<br />
Originator<br />
ESP<br />
10 © Copyright 2010, <strong>OSIsoft</strong> LLC All rights Reserved.<br />
DMZ<br />
<strong>PI</strong> Server<br />
Business User<br />
Domain<br />
Desktops <strong>and</strong><br />
Data Access<br />
Servers