Wireless Technologies in Process Automation - Herkules.oulu.fi - Oulu
Wireless Technologies in Process Automation - Herkules.oulu.fi - Oulu
Wireless Technologies in Process Automation - Herkules.oulu.fi - Oulu
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
22<br />
outsider attacks are blocked and <strong>in</strong> case of <strong>in</strong>sider attack, the security gracefully degrades<br />
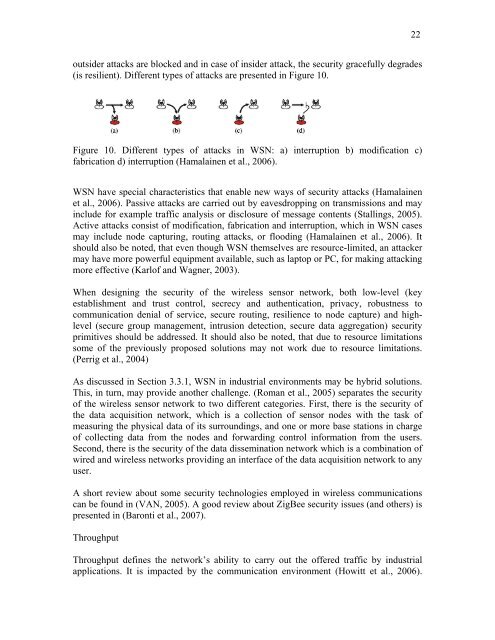
(is resilient). Different types of attacks are presented <strong>in</strong> Figure 10.<br />
Figure 10. Different types of attacks <strong>in</strong> WSN: a) <strong>in</strong>terruption b) modi<strong>fi</strong>cation c)<br />
fabrication d) <strong>in</strong>terruption (Hamala<strong>in</strong>en et al., 2006).<br />
WSN have special characteristics that enable new ways of security attacks (Hamala<strong>in</strong>en<br />
et al., 2006). Passive attacks are carried out by eavesdropp<strong>in</strong>g on transmissions and may<br />
<strong>in</strong>clude for example traf<strong>fi</strong>c analysis or disclosure of message contents (Stall<strong>in</strong>gs, 2005).<br />
Active attacks consist of modi<strong>fi</strong>cation, fabrication and <strong>in</strong>terruption, which <strong>in</strong> WSN cases<br />
may <strong>in</strong>clude node captur<strong>in</strong>g, rout<strong>in</strong>g attacks, or flood<strong>in</strong>g (Hamala<strong>in</strong>en et al., 2006). It<br />
should also be noted, that even though WSN themselves are resource-limited, an attacker<br />
may have more powerful equipment available, such as laptop or PC, for mak<strong>in</strong>g attack<strong>in</strong>g<br />
more effective (Karlof and Wagner, 2003).<br />
When design<strong>in</strong>g the security of the wireless sensor network, both low-level (key<br />
establishment and trust control, secrecy and authentication, privacy, robustness to<br />
communication denial of service, secure rout<strong>in</strong>g, resilience to node capture) and highlevel<br />
(secure group management, <strong>in</strong>trusion detection, secure data aggregation) security<br />
primitives should be addressed. It should also be noted, that due to resource limitations<br />
some of the previously proposed solutions may not work due to resource limitations.<br />
(Perrig et al., 2004)<br />
As discussed <strong>in</strong> Section 3.3.1, WSN <strong>in</strong> <strong>in</strong>dustrial environments may be hybrid solutions.<br />
This, <strong>in</strong> turn, may provide another challenge. (Roman et al., 2005) separates the security<br />
of the wireless sensor network to two different categories. First, there is the security of<br />
the data acquisition network, which is a collection of sensor nodes with the task of<br />
measur<strong>in</strong>g the physical data of its surround<strong>in</strong>gs, and one or more base stations <strong>in</strong> charge<br />
of collect<strong>in</strong>g data from the nodes and forward<strong>in</strong>g control <strong>in</strong>formation from the users.<br />
Second, there is the security of the data dissem<strong>in</strong>ation network which is a comb<strong>in</strong>ation of<br />
wired and wireless networks provid<strong>in</strong>g an <strong>in</strong>terface of the data acquisition network to any<br />
user.<br />
A short review about some security technologies employed <strong>in</strong> wireless communications<br />
can be found <strong>in</strong> (VAN, 2005). A good review about ZigBee security issues (and others) is<br />
presented <strong>in</strong> (Baronti et al., 2007).<br />
Throughput<br />
Throughput def<strong>in</strong>es the network’s ability to carry out the offered traf<strong>fi</strong>c by <strong>in</strong>dustrial<br />
applications. It is impacted by the communication environment (Howitt et al., 2006).