Hashing Methods for Temporal Data - Computer Science - Boston ...
Hashing Methods for Temporal Data - Computer Science - Boston ...
Hashing Methods for Temporal Data - Computer Science - Boston ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
KOLLIOS AND TSOTRAS: HASHING METHODS FOR TEMPORAL DATA 5<br />
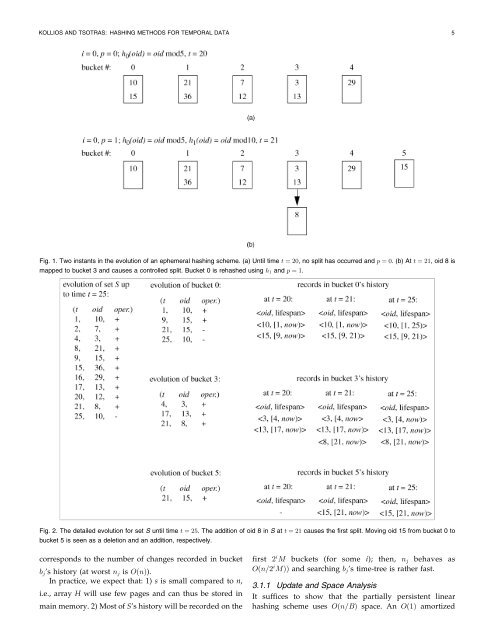
Fig. 1. Two instants in the evolution of an ephemeral hashing scheme. a) Until time t ˆ 20, no split has occurred and p ˆ 0. b)Att ˆ 21, oid 8 is<br />
mapped to bucket 3 and causes a controlled split. Bucket 0 is rehashed using h 1 and p ˆ 1.<br />
Fig. 2. The detailed evolution <strong>for</strong> set S until time t ˆ 25. The addition of oid 8 in S at t ˆ 21 causes the first split. Moving oid 15 from bucket 0 to<br />
bucket 5 is seen as a deletion and an addition, respectively.<br />
corresponds to the number of changes recorded in bucket<br />
b j 's history at worst n j is O…n†).<br />
In practice,we expect that: 1) s is small compared to n,<br />
i.e.,array H will use few pages and can thus be stored in<br />
main memory. 2) Most of S's history will be recorded on the<br />
first 2 i M buckets <strong>for</strong> some i); then, n j behaves as<br />
O…n=2 i M†† and searching b j 's time-tree is rather fast.<br />
3.1.1 Update and Space Analysis<br />
It suffices to show that the partially persistent linear<br />
hashing scheme uses O…n=B† space. An O…1† amortized