Fraud Detection in Selection Exams Using Knowledge Engineering ...
Fraud Detection in Selection Exams Using Knowledge Engineering ...
Fraud Detection in Selection Exams Using Knowledge Engineering ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
mak<strong>in</strong>g the analysis of the behavior of other CBR software or<br />
others KE tools for a greater volume of data.<br />
ACKNOWLEDGMENT<br />
We want to thank Dr. Marcelo Sobottka of the Department<br />
of Mathematics at the Federal University of Santa Catar<strong>in</strong>a<br />
(Brazil) for his valuable help <strong>in</strong> determ<strong>in</strong><strong>in</strong>g the probability of<br />
IWA <strong>in</strong> a test of multiple-choice questions.<br />
REFERENCES<br />
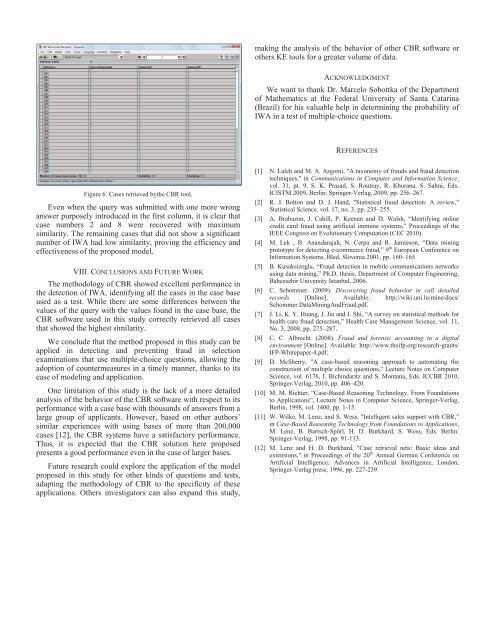
Figure 6. Cases retrieved bythe CBR tool.<br />
Even when the query was submitted with one more wrong<br />
answer purposely <strong>in</strong>troduced <strong>in</strong> the first column, it is clear that<br />
case numbers 2 and 8 were recovered with maximum<br />
similarity. The rema<strong>in</strong><strong>in</strong>g cases that did not show a significant<br />
number of IWA had low similarity, prov<strong>in</strong>g the efficiency and<br />
effectiveness of the proposed model.<br />
VIII. CONCLUSIONS AND FUTURE WORK<br />
The methodology of CBR showed excellent performance <strong>in</strong><br />
the detection of IWA, identify<strong>in</strong>g all the cases <strong>in</strong> the case base<br />
used as a test. While there are some differences between the<br />
values of the query with the values found <strong>in</strong> the case base, the<br />
CBR software used <strong>in</strong> this study correctly retrieved all cases<br />
that showed the highest similarity.<br />
We conclude that the method proposed <strong>in</strong> this study can be<br />
applied <strong>in</strong> detect<strong>in</strong>g and prevent<strong>in</strong>g fraud <strong>in</strong> selection<br />
exam<strong>in</strong>ations that use multiple-choice questions, allow<strong>in</strong>g the<br />
adoption of countermeasures <strong>in</strong> a timely manner, thanks to its<br />
ease of model<strong>in</strong>g and application.<br />
One limitation of this study is the lack of a more detailed<br />
analysis of the behavior of the CBR software with respect to its<br />
performance with a case base with thousands of answers from a<br />
large group of applicants. However, based on other authors’<br />
similar experiences with us<strong>in</strong>g bases of more than 200,000<br />
cases [12], the CBR systems have a satisfactory performance.<br />
Thus, it is expected that the CBR solution here proposed<br />
presents a good performance even <strong>in</strong> the case of larger bases.<br />
Future research could explore the application of the model<br />
proposed <strong>in</strong> this study for other k<strong>in</strong>ds of questions and tests,<br />
adapt<strong>in</strong>g the methodology of CBR to the specificity of these<br />
applications. Others <strong>in</strong>vestigators can also expand this study,<br />
[1] N. Laleh and M. A. Azgomi, "A taxonomy of frauds and fraud detection<br />
techniques," <strong>in</strong> Communications <strong>in</strong> Computer and Information Science,<br />
vol. 31, pt. 9, S. K. Prasad, S. Routray, R. Khurana, S. Sahni, Eds.<br />
ICISTM 2009, Berl<strong>in</strong>: Spr<strong>in</strong>ger-Verlag, 2009, pp. 256–267.<br />
[2] R. J. Bolton and D. J. Hand, "Statistical fraud detection: A review,"<br />
Statistical Science, vol. 17, no. 3, pp. 235–255.<br />
[3] A. Brabazon, J. Cahill, P. Keenan and D. Walsh, “Identify<strong>in</strong>g onl<strong>in</strong>e<br />
credit card fraud us<strong>in</strong>g artificial immune systems,” Proceed<strong>in</strong>gs of the<br />
IEEE Congress on Evolutionary Computation (CEC 2010).<br />
[4] M. Lek , B. Anandarajah, N. Cerpa and R. Jamieson, “Data m<strong>in</strong><strong>in</strong>g<br />
prototype for detect<strong>in</strong>g e-commerce fraud,” 9 th European Conference on<br />
Information Systems, Bled, Slovenia 2001, pp. 160–165.<br />
[5] B. Kusaksizoglu, “<strong>Fraud</strong> detection <strong>in</strong> mobile communications networks<br />
us<strong>in</strong>g data m<strong>in</strong><strong>in</strong>g,” Ph.D. thesis, Department of Computer Eng<strong>in</strong>eer<strong>in</strong>g,<br />
Bahcesehir University Istanbul, 2006.<br />
[6] C. Schommer. (2009). Discover<strong>in</strong>g fraud behavior <strong>in</strong> call detailed<br />
records [Onl<strong>in</strong>e]. Available: http://wiki.uni.lu/m<strong>in</strong>e/docs/<br />
Schommer.DataM<strong>in</strong><strong>in</strong>gAnd<strong>Fraud</strong>.pdf.<br />
[7] J. Li, K. Y. Huang, J. J<strong>in</strong> and J. Shi, “A survey on statistical methods for<br />
health care fraud detection,” Health Care Management Science, vol. 11,<br />
No. 3, 2008, pp. 275–287.<br />
[8] C. C. Albrecht. (2008). <strong>Fraud</strong> and forensic account<strong>in</strong>g <strong>in</strong> a digital<br />
environment [Onl<strong>in</strong>e]. Available: http://www.theifp.org/research-grants/<br />
IFP-Whitepaper-4.pdf.<br />
[9] D. McSherry, "A case-based reason<strong>in</strong>g approach to automat<strong>in</strong>g the<br />
construction of multiple choice questions," Lecture Notes on Computer<br />
Science, vol. 6176, I. Bich<strong>in</strong>daritz and S. Montana, Eds. ICCBR 2010,<br />
Spr<strong>in</strong>ger-Verlag, 2010, pp. 406–420.<br />
[10] M. M. Richter, “Case-Based Reason<strong>in</strong>g Technology, From Foundations<br />
to Applications”, Lecture Notes <strong>in</strong> Computer Science, Spr<strong>in</strong>ger-Verlag,<br />
Berl<strong>in</strong>, 1998, vol. 1400, pp. 1-15.<br />
[11] W. Wilke, M. Lenz, and S. Wess, "Intelligent sales support with CBR,"<br />
<strong>in</strong> Case-Based Reason<strong>in</strong>g Technology from Foundations to Applications,<br />
M. Lenz, B. Bartsch-Spörl, H. D. Burkhard, S. Wess, Eds. Berl<strong>in</strong>:<br />
Spr<strong>in</strong>ger-Verlag, 1998, pp. 91-113.<br />
[12] M. Lenz and H. D. Burkhard, "Case retrieval nets: Basic ideas and<br />
extensions," <strong>in</strong> Proceed<strong>in</strong>gs of the 20 th Annual German Conference on<br />
Artificial Intelligence: Advances <strong>in</strong> Artificial Intelligence, London,<br />
Spr<strong>in</strong>ger-Verlag press, 1996, pp. 227-239.