Outline Acknowledment Some references RSA and ECC challenges
Outline Acknowledment Some references RSA and ECC challenges
Outline Acknowledment Some references RSA and ECC challenges
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
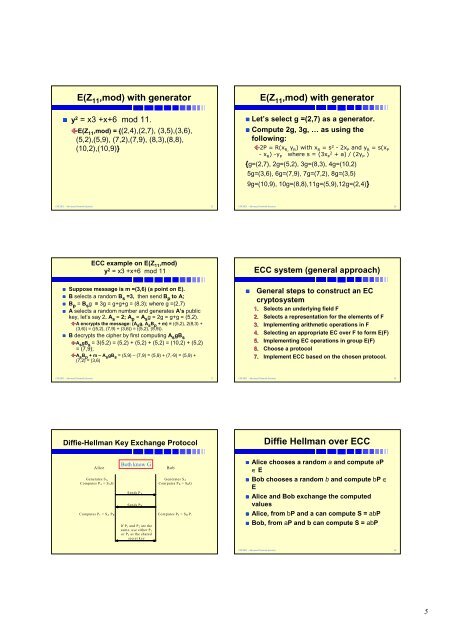
E(Z 11 ,mod) with generator<br />
• y 2 = x3 +x+6 mod 11.<br />
E( E(Z 11 ,mod) = {(2,4),(2,7),{<br />
(3,5),(3,6),<br />
(5,2),(5,9), (7,2),(7,9), (8,3),(8,8),<br />
(10,2),(10,9)}<br />
E(Z 11 ,mod) with generator<br />
• Let’s select g =(2,7) as a generator.<br />
• Compute 2g, , 3g, … as using the<br />
following:<br />
2P = R(x R,<br />
y ) with x R R = s2s<br />
- 2x <strong>and</strong> y P R = s(x P<br />
- x R<br />
) -y P<br />
where s = (3x 2 P<br />
+ a) / (2y P<br />
)<br />
{g=(2,7), 2g=(5,2), 3g=(8,3), 4g=(10,2)<br />
5g=(3,6), 6g=(7,9), 7g=(7,2), 8g=(3,5)<br />
9g=(10,9), 10g=(8,8),11g=(5,9),12g=(2,4)}<br />
CPE5021 - Advanced Network Security 25<br />
CPE5021 - Advanced Network Security 26<br />
<strong>ECC</strong> example on E(Z 11 ,mod)<br />
y 2 = x3 +x+6 mod 11<br />
<strong>ECC</strong> system (general approach)<br />
• Suppose message is m =(3,6) (a point on E).<br />
• B selects a r<strong>and</strong>om B s =3, then send B p to A;<br />
• B p = B s g = 3g = g+g+g = (8,3); where g =(2,7)<br />
• A selects a r<strong>and</strong>om number <strong>and</strong> generates A’s public<br />
key, let’s s say 2. A s = 2; A p = A s g = 2g = g+g = (5,2).<br />
A A encrypts the message: (A s g, A s B p + m) = ((5,2), 2(8,3) +<br />
(3,6)) = ((5,2), (7,9) + (3,6)) = ((5,2), (5,9)).<br />
• B decrypts the cipher by first computing A s gB s<br />
A s gB s = 3(5,2) = (5,2) + (5,2) + (5,2) = (10,2) + (5,2)<br />
= (7,9);<br />
A s B p + m – A s gB s = (5,9) – (7,9) = (5,9) + (7,-9) = (5,9) +<br />
(7,2) = (3,6)<br />
• General steps to construct an EC<br />
cryptosystem<br />
1. Selects an underlying field F<br />
2. Selects a representation for the elements of F<br />
3. Implementing arithmetic operations in F<br />
4. Selecting an appropriate EC over F to form E(F)<br />
5. Implementing EC operations in group E(F)<br />
6. Choose a protocol<br />
7. Implement <strong>ECC</strong> based on the chosen protocol.<br />
CPE5021 - Advanced Network Security 27<br />
CPE5021 - Advanced Network Security 28<br />
Diffie-Hellman<br />
Key Exchange Protocol<br />
Diffie Hellman over <strong>ECC</strong><br />
Alice<br />
Generates SA<br />
Computes PA = SAG<br />
Computes P1 = SA PB<br />
Both know G<br />
Sends PA<br />
Sends PB<br />
If P1 <strong>and</strong> P2 are the<br />
same, use either P1<br />
or P2 as the shared<br />
secret key<br />
Bob<br />
Generates SA<br />
Computes PB = SBG<br />
Computes P2 = SB PA<br />
• Alice chooses a r<strong>and</strong>om a <strong>and</strong> compute aP<br />
∈ E<br />
• Bob chooses a r<strong>and</strong>om b <strong>and</strong> compute bP ∈<br />
E<br />
• Alice <strong>and</strong> Bob exchange the computed<br />
values<br />
• Alice, from bP <strong>and</strong> a can compute S = abP<br />
• Bob, from aP <strong>and</strong> b can compute S = abP<br />
CPE5021 - Advanced Network Security 30<br />
5