Attacking AES via SAT - Department of Computer Science
Attacking AES via SAT - Department of Computer Science
Attacking AES via SAT - Department of Computer Science
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>AES</strong><br />
<strong>AES</strong> and <strong>SAT</strong><br />
Translation <strong>of</strong> <strong>AES</strong> into <strong>SAT</strong><br />
Evaluation <strong>of</strong> initial translation<br />
Future work<br />
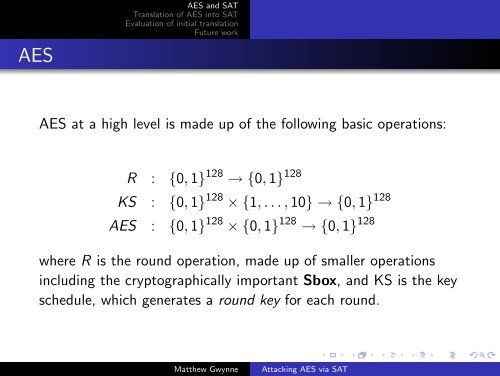
<strong>AES</strong> at a high level is made up <strong>of</strong> the following basic operations:<br />
R : {0, 1} 128 → {0, 1} 128<br />
KS : {0, 1} 128 × {1, . . . , 10} → {0, 1} 128<br />
<strong>AES</strong> : {0, 1} 128 × {0, 1} 128 → {0, 1} 128<br />
where R is the round operation, made up <strong>of</strong> smaller operations<br />
including the cryptographically important Sbox, and KS is the key<br />
schedule, which generates a round key for each round.<br />
Matthew Gwynne<br />
<strong>Attacking</strong> <strong>AES</strong> <strong>via</strong> <strong>SAT</strong>