CPNI - GPG - Guide 2 - Implement Secure Architecture
CPNI - GPG - Guide 2 - Implement Secure Architecture
CPNI - GPG - Guide 2 - Implement Secure Architecture
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Good Practice <strong>Guide</strong> – Process Control and SCADA Security<br />
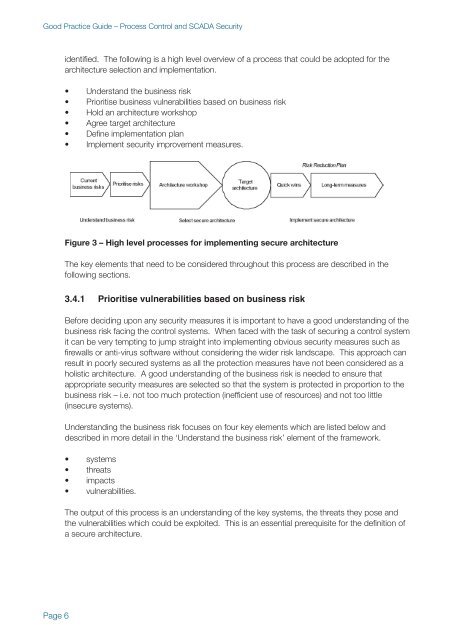
identified. The following is a high level overview of a process that could be adopted for the<br />
architecture selection and implementation.<br />
• Understand the business risk<br />
• Prioritise business vulnerabilities based on business risk<br />
• Hold an architecture workshop<br />
• Agree target architecture<br />
• Define implementation plan<br />
• <strong>Implement</strong> security improvement measures.<br />
Figure 3 – High level processes for implementing secure architecture<br />
The key elements that need to be considered throughout this process are described in the<br />
following sections.<br />
3.4.1 Prioritise vulnerabilities based on business risk<br />
Before deciding upon any security measures it is important to have a good understanding of the<br />
business risk facing the control systems. When faced with the task of securing a control system<br />
it can be very tempting to jump straight into implementing obvious security measures such as<br />
firewalls or anti-virus software without considering the wider risk landscape. This approach can<br />
result in poorly secured systems as all the protection measures have not been considered as a<br />
holistic architecture. A good understanding of the business risk is needed to ensure that<br />
appropriate security measures are selected so that the system is protected in proportion to the<br />
business risk – i.e. not too much protection (inefficient use of resources) and not too little<br />
(insecure systems).<br />
Understanding the business risk focuses on four key elements which are listed below and<br />
described in more detail in the ‘Understand the business risk’ element of the framework.<br />
• systems<br />
• threats<br />
• impacts<br />
• vulnerabilities.<br />
The output of this process is an understanding of the key systems, the threats they pose and<br />
the vulnerabilities which could be exploited. This is an essential prerequisite for the definition of<br />
a secure architecture.<br />
Page 6