Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
By default <strong>fw</strong> moni<strong>to</strong>r captures packets at all four positions. With -m it is possible <strong>to</strong> capture packets at<br />
specific posi<strong>to</strong>ns. <strong>fw</strong> moni<strong>to</strong>r <strong>use</strong>s single letters as indica<strong>to</strong>rs for the position:<br />
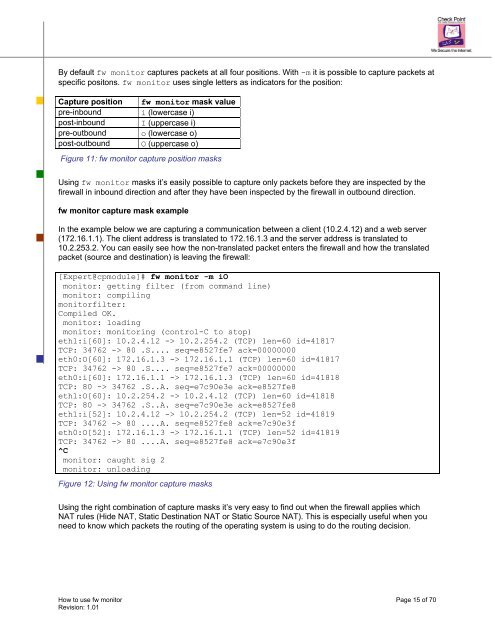
Capture position <strong>fw</strong> moni<strong>to</strong>r mask value<br />
pre-inbound i (lowercase i)<br />
post-inbound I (uppercase i)<br />
pre-outbound o (lowercase o)<br />
post-outbound O (uppercase o)<br />
Figure 11: <strong>fw</strong> moni<strong>to</strong>r capture position masks<br />
Using <strong>fw</strong> moni<strong>to</strong>r masks it’s easily possible <strong>to</strong> capture only packets before they are inspected by the<br />
firewall in inbound direction and after they have been inspected by the firewall in outbound direction.<br />
<strong>fw</strong> moni<strong>to</strong>r capture mask example<br />
In the example below we are capturing a communication between a client (10.2.4.12) and a web server<br />
(172.16.1.1). The client address is translated <strong>to</strong> 172.16.1.3 and the server address is translated <strong>to</strong><br />
10.2.253.2. You can easily see how the non-translated packet enters the firewall and how the translated<br />
packet (source and destination) is leaving the firewall:<br />
[Expert@cpmodule]# <strong>fw</strong> moni<strong>to</strong>r -m iO<br />
moni<strong>to</strong>r: getting filter (from command line)<br />
moni<strong>to</strong>r: compiling<br />
moni<strong>to</strong>rfilter:<br />
Compiled OK.<br />
moni<strong>to</strong>r: loading<br />
moni<strong>to</strong>r: moni<strong>to</strong>ring (control-C <strong>to</strong> s<strong>to</strong>p)<br />
eth1:i[60]: 10.2.4.12 -> 10.2.254.2 (TCP) len=60 id=41817<br />
TCP: 34762 -> 80 .S.... seq=e8527fe7 ack=00000000<br />
eth0:O[60]: 172.16.1.3 -> 172.16.1.1 (TCP) len=60 id=41817<br />
TCP: 34762 -> 80 .S.... seq=e8527fe7 ack=00000000<br />
eth0:i[60]: 172.16.1.1 -> 172.16.1.3 (TCP) len=60 id=41818<br />
TCP: 80 -> 34762 .S..A. seq=e7c90e3e ack=e8527fe8<br />
eth1:O[60]: 10.2.254.2 -> 10.2.4.12 (TCP) len=60 id=41818<br />
TCP: 80 -> 34762 .S..A. seq=e7c90e3e ack=e8527fe8<br />
eth1:i[52]: 10.2.4.12 -> 10.2.254.2 (TCP) len=52 id=41819<br />
TCP: 34762 -> 80 ....A. seq=e8527fe8 ack=e7c90e3f<br />
eth0:O[52]: 172.16.1.3 -> 172.16.1.1 (TCP) len=52 id=41819<br />
TCP: 34762 -> 80 ....A. seq=e8527fe8 ack=e7c90e3f<br />
^C<br />
moni<strong>to</strong>r: caught sig 2<br />
moni<strong>to</strong>r: unloading<br />
Figure 12: Using <strong>fw</strong> moni<strong>to</strong>r capture masks<br />
Using the right combination of capture masks it’s very easy <strong>to</strong> find out when the firewall applies which<br />
NAT rules (Hide NAT, Static Destination NAT or Static Source NAT). This is especially <strong>use</strong>ful when you<br />
need <strong>to</strong> know which packets the routing of the operating system is using <strong>to</strong> do the routing decision.<br />
<strong>How</strong> <strong>to</strong> <strong>use</strong> <strong>fw</strong> moni<strong>to</strong>r Page 15 of 70<br />
Revision: 1.01