G - 16th workshop on Elliptic Curve Cryptography
G - 16th workshop on Elliptic Curve Cryptography
G - 16th workshop on Elliptic Curve Cryptography
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
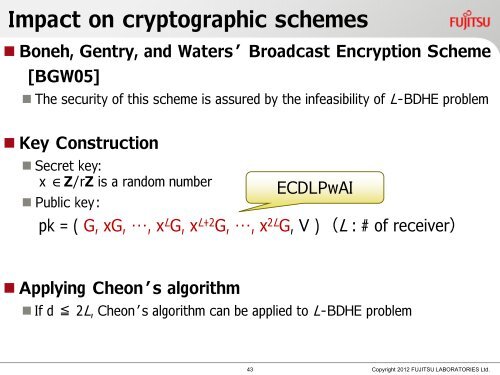
Impact <strong>on</strong> cryptographic schemes<br />
• B<strong>on</strong>eh, Gentry, and Waters’ Broadcast Encrypti<strong>on</strong> Scheme<br />
[BGW05]<br />
• The security of this scheme is assured by the infeasibility of L-BDHE problem<br />
• Key C<strong>on</strong>structi<strong>on</strong><br />
• Secret key:<br />
x ∈Z/rZ is a random number<br />
• Public key:<br />
ECDLPwAI<br />
pk = ( G, xG, …, x L G, x L+2 G, …, x 2L G, V ) (L : # of receiver)<br />
• Applying Che<strong>on</strong>’s algorithm<br />
• If d ≦ 2L, Che<strong>on</strong>’s algorithm can be applied to L-BDHE problem<br />
43<br />
Copyright 2012 FUJITSU LABORATORIES Ltd.