CSC 774 -- Network Security - Dr. Peng Ning
CSC 774 -- Network Security - Dr. Peng Ning
CSC 774 -- Network Security - Dr. Peng Ning
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
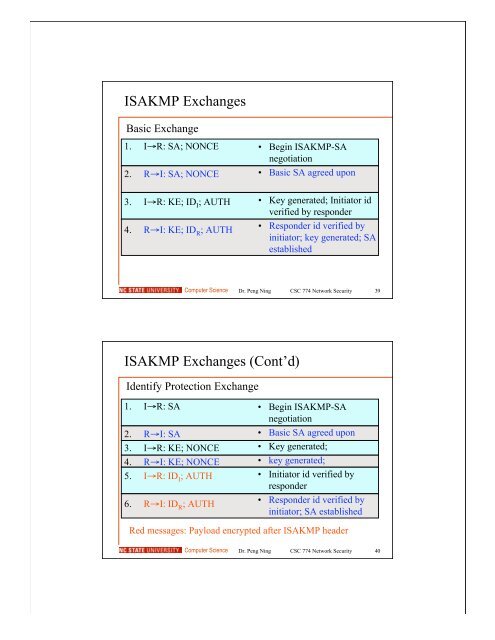
ISAKMP Exchanges<br />
Basic Exchange<br />
1. I→R: SA; NONCE<br />
2. R→I: SA; NONCE<br />
3. I→R: KE; ID I ; AUTH<br />
4. R→I: KE; ID R ; AUTH<br />
• Begin ISAKMP-SA<br />
negotiation<br />
• Basic SA agreed upon<br />
• Key generated; Initiator id<br />
verified by responder<br />
• Responder id verified by<br />
initiator; key generated; SA<br />
established<br />
Computer Science<br />
<strong>Dr</strong>. <strong>Peng</strong> <strong>Ning</strong> <strong>CSC</strong> <strong>774</strong> <strong>Network</strong> <strong>Security</strong> 39<br />
ISAKMP Exchanges (Cont’d)<br />
Identify Protection Exchange<br />
1. I→R: SA<br />
2. R→I: SA<br />
3. I→R: KE; NONCE<br />
4. R→I: KE; NONCE<br />
5. I→R: ID I ; AUTH<br />
6. R→I: ID R ; AUTH<br />
• Begin ISAKMP-SA<br />
negotiation<br />
• Basic SA agreed upon<br />
• Key generated;<br />
• key generated;<br />
• Initiator id verified by<br />
responder<br />
• Responder id verified by<br />
initiator; SA established<br />
Red messages: Payload encrypted after ISAKMP header<br />
Computer Science<br />
<strong>Dr</strong>. <strong>Peng</strong> <strong>Ning</strong> <strong>CSC</strong> <strong>774</strong> <strong>Network</strong> <strong>Security</strong> 40