Trustwave Application Penetration Test Digitaltransactions-080815
Trustwave Application Penetration Test Digitaltransactions-080815
Trustwave Application Penetration Test Digitaltransactions-080815
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
CONFIDENTIAL INFORMATION – FOR INTERNAL USE ONLY<br />
<strong>Trustwave</strong><br />
<strong>Application</strong> <strong>Penetration</strong> <strong>Test</strong><br />
unexpected characters. These characters are sometimes referred to as “special” characters.<br />
Different shells, applications, command processors and languages respond in different but<br />
predictable ways to specific combinations of characters. If an application does not properly<br />
sanitize client input, a malicious user may, among other actions, be able to access or modify<br />
protected or privileged data, execute arbitrary code on a server, or induce a legitimate user to<br />
execute code on the attacker’s behalf.<br />
In testing for meta-character sanitization, <strong>Trustwave</strong> supplied data with specific characters and<br />
interpreted server responses. Meta-characters that have meaning to a wide variety of<br />
applications were tested; some of these characters are likely benign in the Boland Hills<br />
application infrastructure. Since application infrastructure changes cannot be accurately<br />
predicted, <strong>Trustwave</strong> feels that the best approach is to protect against all meta-characters, not<br />
just those known to the current environment.<br />
An analysis of each category can be found below.<br />
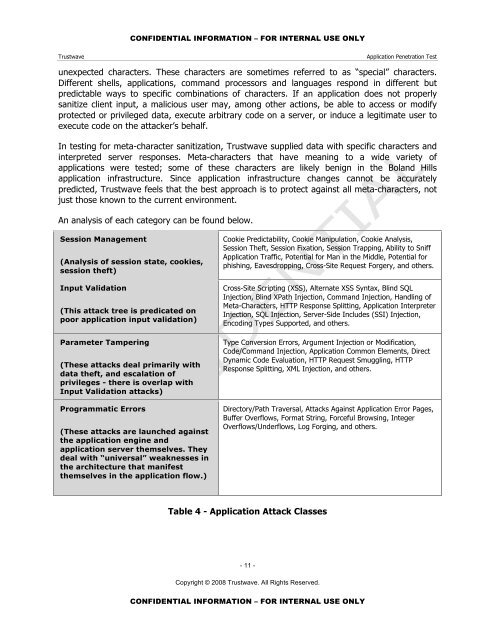
Session Management<br />
(Analysis of session state, cookies,<br />
session theft)<br />
Input Validation<br />
(This attack tree is predicated on<br />
poor application input validation)<br />
Parameter Tampering<br />
(These attacks deal primarily with<br />
data theft, and escalation of<br />
privileges - there is overlap with<br />
Input Validation attacks)<br />
Programmatic Errors<br />
(These attacks are launched against<br />
the application engine and<br />
application server themselves. They<br />
deal with “universal” weaknesses in<br />
the architecture that manifest<br />
themselves in the application flow.)<br />
Cookie Predictability, Cookie Manipulation, Cookie Analysis,<br />
Session Theft, Session Fixation, Session Trapping, Ability to Sniff<br />
<strong>Application</strong> Traffic, Potential for Man in the Middle, Potential for<br />
phishing, Eavesdropping, Cross-Site Request Forgery, and others.<br />
Cross-Site Scripting (XSS), Alternate XSS Syntax, Blind SQL<br />
Injection, Blind XPath Injection, Command Injection, Handling of<br />
Meta-Characters, HTTP Response Splitting, <strong>Application</strong> Interpreter<br />
Injection, SQL Injection, Server-Side Includes (SSI) Injection,<br />
Encoding Types Supported, and others.<br />
Type Conversion Errors, Argument Injection or Modification,<br />
Code/Command Injection, <strong>Application</strong> Common Elements, Direct<br />
Dynamic Code Evaluation, HTTP Request Smuggling, HTTP<br />
Response Splitting, XML Injection, and others.<br />
Directory/Path Traversal, Attacks Against <strong>Application</strong> Error Pages,<br />
Buffer Overflows, Format String, Forceful Browsing, Integer<br />
Overflows/Underflows, Log Forging, and others.<br />
Table 4 - <strong>Application</strong> Attack Classes<br />
- 11 -<br />
Copyright © 2008 <strong>Trustwave</strong>. All Rights Reserved.<br />
CONFIDENTIAL INFORMATION – FOR INTERNAL USE ONLY