A survey of Indian Cyber crime and law and its pre- vention approach
A survey of Indian Cyber crime and law and its pre- vention approach
A survey of Indian Cyber crime and law and its pre- vention approach
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
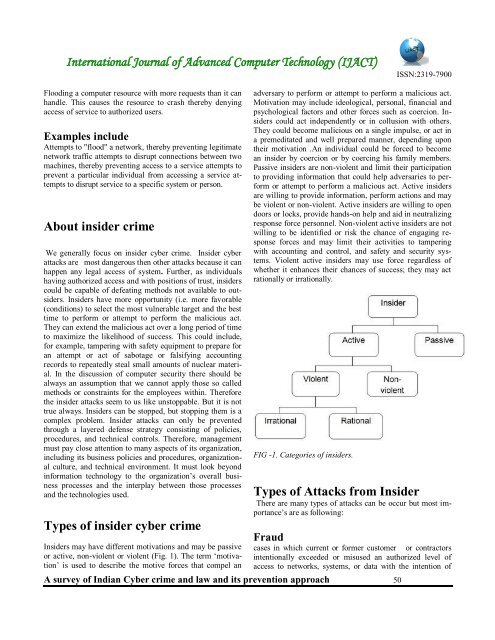
International Journal <strong>of</strong> Advanced Computer Technology (IJACT)ISSN:2319-7900Flooding a computer resource with more requests than it canh<strong>and</strong>le. This causes the resource to crash thereby denyingaccess <strong>of</strong> service to authorized users.Examples includeAttempts to "flood" a network, thereby <strong>pre</strong>venting legitimatenetwork traffic attempts to disrupt connections between twomachines, thereby <strong>pre</strong>venting access to a service attempts to<strong>pre</strong>vent a particular individual from accessing a service attemptsto disrupt service to a specific system or person.About insider <strong>crime</strong>We generally focus on insider cyber <strong>crime</strong>. Insider cyberattacks are most dangerous then other attacks because it canhappen any legal access <strong>of</strong> system. Further, as individualshaving authorized access <strong>and</strong> with positions <strong>of</strong> trust, insiderscould be capable <strong>of</strong> defeating methods not available to outsiders.Insiders have more opportunity (i.e. more favorable(conditions) to select the most vulnerable target <strong>and</strong> the besttime to perform or attempt to perform the malicious act.They can extend the malicious act over a long period <strong>of</strong> timeto maximize the likelihood <strong>of</strong> success. This could include,for example, tampering with safety equipment to <strong>pre</strong>pare foran attempt or act <strong>of</strong> sabotage or falsifying accountingrecords to repeatedly steal small amounts <strong>of</strong> nuclear material.In the discussion <strong>of</strong> computer security there should bealways an assumption that we cannot apply those so calledmethods or constraints for the employees within. Thereforethe insider attacks seem to us like unstoppable. But it is nottrue always. Insiders can be stopped, but stopping them is acomplex problem. Insider attacks can only be <strong>pre</strong>ventedthrough a layered defense strategy consisting <strong>of</strong> policies,procedures, <strong>and</strong> technical controls. Therefore, managementmust pay close attention to many aspects <strong>of</strong> <strong>its</strong> organization,including <strong>its</strong> business policies <strong>and</strong> procedures, organizationalculture, <strong>and</strong> technical environment. It must look beyondinformation technology to the organization‟s overall businessprocesses <strong>and</strong> the interplay between those processes<strong>and</strong> the technologies used.Types <strong>of</strong> insider cyber <strong>crime</strong>Insiders may have different motivations <strong>and</strong> may be passiveor active, non-violent or violent (Fig. 1). The term „motivation‟is used to describe the motive forces that compel anadversary to perform or attempt to perform a malicious act.Motivation may include ideological, personal, financial <strong>and</strong>psychological factors <strong>and</strong> other forces such as coercion. Insiderscould act independently or in collusion with others.They could become malicious on a single impulse, or act ina <strong>pre</strong>meditated <strong>and</strong> well <strong>pre</strong>pared manner, depending upontheir motivation .An individual could be forced to becomean insider by coercion or by coercing his family members.Passive insiders are non-violent <strong>and</strong> limit their participationto providing information that could help adversaries to performor attempt to perform a malicious act. Active insidersare willing to provide information, perform actions <strong>and</strong> maybe violent or non-violent. Active insiders are willing to opendoors or locks, provide h<strong>and</strong>s-on help <strong>and</strong> aid in neutralizingresponse force personnel. Non-violent active insiders are notwilling to be identified or risk the chance <strong>of</strong> engaging responseforces <strong>and</strong> may limit their activities to tamperingwith accounting <strong>and</strong> control, <strong>and</strong> safety <strong>and</strong> security systems.Violent active insiders may use force regardless <strong>of</strong>whether it enhances their chances <strong>of</strong> success; they may actrationally or irrationally.FIG -1. Categories <strong>of</strong> insiders.Types <strong>of</strong> Attacks from InsiderThere are many types <strong>of</strong> attacks can be occur but most importance‟sare as following:Fraudcases in which current or former customer or contractorsintentionally exceeded or misused an authorized level <strong>of</strong>access to networks, systems, or data with the intention <strong>of</strong>A <strong>survey</strong> <strong>of</strong> <strong>Indian</strong> <strong>Cyber</strong> <strong>crime</strong> <strong>and</strong> <strong>law</strong> <strong>and</strong> <strong>its</strong> <strong>pre</strong><strong>vention</strong> <strong>approach</strong> 50