Slides - Inria
Slides - Inria
Slides - Inria
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
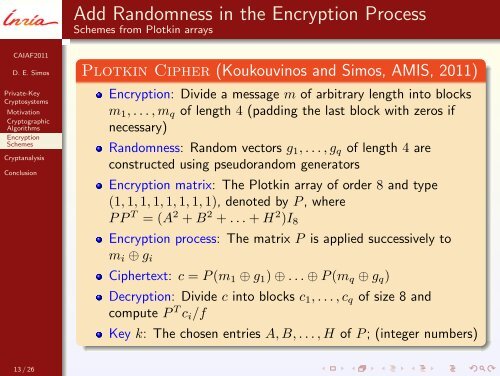
Add Randomness in the Encryption ProcessSchemes from Plotkin arraysCAIAF2011D. E. SimosPrivate-KeyCryptosystemsMotivationCryptographicAlgorithmsEncryptionSchemesCryptanalysisConclusionPlotkin Cipher (Koukouvinos and Simos, AMIS, 2011)Encryption: Divide a message m of arbitrary length into blocksm 1 , . . . , m q of length 4 (padding the last block with zeros ifnecessary)Randomness: Random vectors g 1 , . . . , g q of length 4 areconstructed using pseudorandom generatorsEncryption matrix: The Plotkin array of order 8 and type(1, 1, 1, 1, 1, 1, 1, 1), denoted by P , whereP P T = (A 2 + B 2 + . . . + H 2 )I 8Encryption process: The matrix P is applied successively tom i ⊕ g iCiphertext: c = P (m 1 ⊕ g 1 ) ⊕ . . . ⊕ P (m q ⊕ g q )Decryption: Divide c into blocks c 1 , . . . , c q of size 8 andcompute P T c i /fKey k: The chosen entries A, B, . . . , H of P ; (integer numbers)13 / 26