2013-12-05_tcpflow-and-BE-update
2013-12-05_tcpflow-and-BE-update
2013-12-05_tcpflow-and-BE-update
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
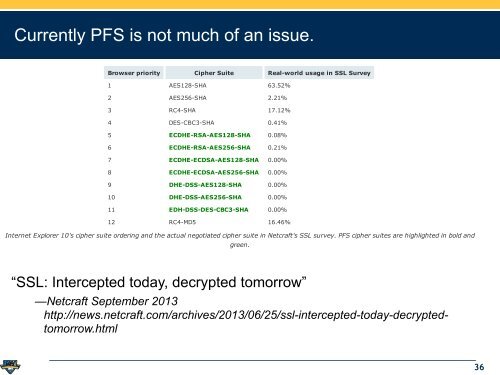
The actual cipher suites used when connecting to 2.4 Million SSL sites with the cipher suite settings extracted from each browser. *Opera does not includeits TLS 1.2 cipher suites.nternet Explorer does particularly poorly as it does not support any cipher suite that uses both RSA public keys <strong>and</strong> non-elliptic-curve DH key exchange,Currently PFS is not much of an issue.hich includes the most popular PFS cipher suite. The PFS cipher suites that IE does support have a lower priority than some of the most commonlyupported non-PFS cipher suites. Curiously, IE does support DHE-DSS-AES256-SHA, which uses the rarer DSS authentication method, but not the veryopular DHE-RSA-AES256-SHA.Browser priority Cipher Suite Real-world usage in SSL Survey1 AES<strong>12</strong>8-SHA 63.52%2 AES256-SHA 2.21%3 RC4-SHA 17.<strong>12</strong>%4 DES-CBC3-SHA 0.41%5 ECDHE-RSA-AES<strong>12</strong>8-SHA 0.08%6 ECDHE-RSA-AES256-SHA 0.21%7 ECDHE-ECDSA-AES<strong>12</strong>8-SHA 0.00%8 ECDHE-ECDSA-AES256-SHA 0.00%9 DHE-DSS-AES<strong>12</strong>8-SHA 0.00%10 DHE-DSS-AES256-SHA 0.00%11 EDH-DSS-DES-CBC3-SHA 0.00%<strong>12</strong> RC4-MD5 16.46%Internet Explorer 10's cipher suite ordering <strong>and</strong> the actual negotiated cipher suite in Netcraft's SSL survey. PFS cipher suites are highlighted in bold <strong>and</strong>green.afari supports many PFS cipher suites but non-elliptic-curve cipher suites are used only as a last resort. As several non-PFS ciphers have a higher priority,“SSL: Intercepted today, decrypted tomorrow”eb servers respecting the browser's preferences will end up selecting a non-PFS cipher suite even if the web server itself does support some (non ellipticurve)PFS cipher suites.hrome, Firefox, <strong>and</strong> Opera all do better, preferring PFS cipher suites ahead of non-PFS at any given strength level — for example Opera's preference list—Netcraft September <strong>2013</strong>http://news.netcraft.com/archives/<strong>2013</strong>/06/25/ssl-intercepted-today-decryptedtomorrow.htmltarts: DHE-RSA-AES256-SHA, DHE-DSS-AES256-SHA, AES256-SHA, DHE-RSA-AES<strong>12</strong>8-SHA, DHE-DSS-AES<strong>12</strong>8-SHA, AES<strong>12</strong>8-SHA. Netcraft did notnclude any cipher suites only present in TLS 1.2 which includes many of Opera's PFS cipher suites, so the results for Opera form a lower bound on theumber of SSL sites using PFS with Opera.one of the browsers change their user interface perceptibly to reflect the presence of PFS akin to the way EV certificates are treated to a green addressar. Google Chrome <strong>and</strong> Opera show the cipher suite used (in popups or dialog boxes), but they rely on a user underst<strong>and</strong>ing the implications of wordinguch as "[..] ECDHE_RSA as the key exchange mechanism".eb server support for PFS36