Tor - The Free Haven Project
Tor - The Free Haven Project
Tor - The Free Haven Project
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
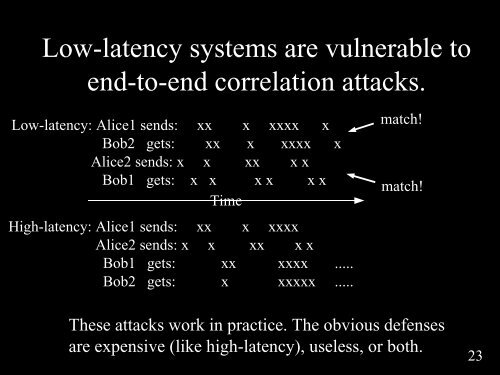
Low-latency systems are vulnerable toend-to-end correlation attacks.Low-latency: Alice1 sends: xx x xxxx xBob2 gets: xx x xxxx xAlice2 sends: x x xx x xBob1 gets: x x x x x xTimeHigh-latency: Alice1 sends: xx x xxxxAlice2 sends: x x xx x xBob1 gets: xx xxxx .....Bob2 gets: x xxxxx .....match!match!<strong>The</strong>se attacks work in practice. <strong>The</strong> obvious defensesare expensive (like high-latency), useless, or both.23