Understanding Certification Path Construction - oasis pki
Understanding Certification Path Construction - oasis pki
Understanding Certification Path Construction - oasis pki
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
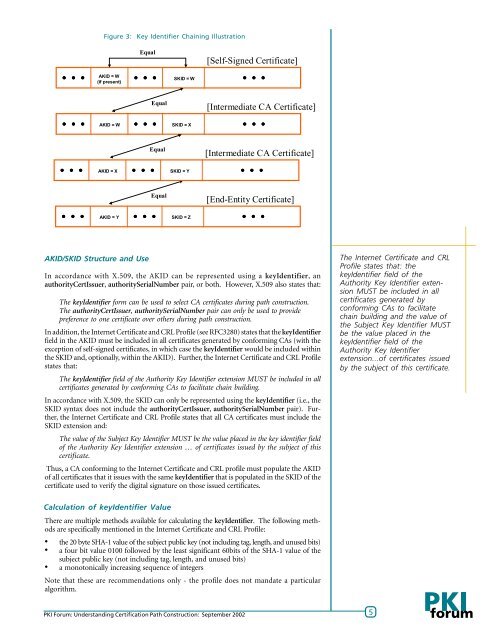
Figure 3: Key Identifier Chaining IllustrationEqual[Self-Signed Certificate]AKID = W(if present)SKID = WEqual[Intermediate CA Certificate]AKID = WSKID = XEqual[Intermediate CA Certificate]AKID = XSKID = YEqual[End-Entity Certificate]AKID = YSKID = ZAKID/SKID Structure and UseIn accordance with X.509, the AKID can be represented using a keyIdentifier, anauthorityCertIssuer, authoritySerialNumber pair, or both. However, X.509 also states that:The keyIdentifier form can be used to select CA certificates during path construction.The authorityCertIssuer, authoritySerialNumber pair can only be used to providepreference to one certificate over others during path construction.In addition, the Internet Certificate and CRL Profile (see RFC3280) states that the keyIdentifierfield in the AKID must be included in all certificates generated by conforming CAs (with theexception of self-signed certificates, in which case the keyIdentifier would be included withinthe SKID and, optionally, within the AKID). Further, the Internet Certificate and CRL Profilestates that:The keyIdentifier field of the Authority Key Identifier extension MUST be included in allcertificates generated by conforming CAs to facilitate chain building.In accordance with X.509, the SKID can only be represented using the keyIdentifier (i.e., theSKID syntax does not include the authorityCertIssuer, authoritySerialNumber pair). Further,the Internet Certificate and CRL Profile states that all CA certificates must include theSKID extension and:The value of the Subject Key Identifier MUST be the value placed in the key identifier fieldof the Authority Key Identifier extension … of certificates issued by the subject of thiscertificate.Thus, a CA conforming to the Internet Certificate and CRL profile must populate the AKIDof all certificates that it issues with the same keyIdentifier that is populated in the SKID of thecertificate used to verify the digital signature on those issued certificates.The Internet Certificate and CRLProfile states that: thekeyIdentifier field of theAuthority Key Identifier extensionMUST be included in allcertificates generated byconforming CAs to facilitatechain building and the value ofthe Subject Key Identifier MUSTbe the value placed in thekeyIdentifier field of theAuthority Key Identifierextension...of certificates issuedby the subject of this certificate.Calculation of keyIdentifier ValueThere are multiple methods available for calculating the keyIdentifier. The following methodsare specifically mentioned in the Internet Certificate and CRL Profile:• the 20 byte SHA-1 value of the subject public key (not including tag, length, and unused bits)• a four bit value 0100 followed by the least significant 60bits of the SHA-1 value of thesubject public key (not including tag, length, and unused bits)• a monotonically increasing sequence of integersNote that these are recommendations only - the profile does not mandate a particularalgorithm.PKI Forum: <strong>Understanding</strong> <strong>Certification</strong> <strong>Path</strong> <strong>Construction</strong>: September 2002 5