Chapter 5 Introducing SDN Control in MPLS Networks - High ...
Chapter 5 Introducing SDN Control in MPLS Networks - High ...
Chapter 5 Introducing SDN Control in MPLS Networks - High ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
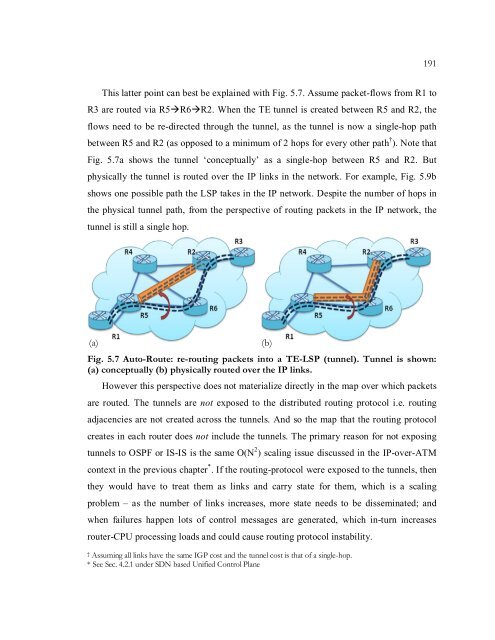
191This latter po<strong>in</strong>t can best be expla<strong>in</strong>ed with Fig. 5.7. Assume packet-flows from R1 toR3 are routed via R5R6R2. When the TE tunnel is created between R5 and R2, theflows need to be re-directed through the tunnel, as the tunnel is now a s<strong>in</strong>gle-hop pathbetween R5 and R2 (as opposed to a m<strong>in</strong>imum of 2 hops for every other path † ). Note thatFig. 5.7a shows the tunnel ‘conceptually’ as a s<strong>in</strong>gle-hop between R5 and R2. Butphysically the tunnel is routed over the IP l<strong>in</strong>ks <strong>in</strong> the network. For example, Fig. 5.9bshows one possible path the LSP takes <strong>in</strong> the IP network. Despite the number of hops <strong>in</strong>the physical tunnel path, from the perspective of rout<strong>in</strong>g packets <strong>in</strong> the IP network, thetunnel is still a s<strong>in</strong>gle hop.(a)Fig. 5.7 Auto-Route: re-rout<strong>in</strong>g packets <strong>in</strong>to a TE-LSP (tunnel). Tunnel is shown:(a) conceptually (b) physically routed over the IP l<strong>in</strong>ks.However this perspective does not materialize directly <strong>in</strong> the map over which packetsare routed. The tunnels are not exposed to the distributed rout<strong>in</strong>g protocol i.e. rout<strong>in</strong>gadjacencies are not created across the tunnels. And so the map that the rout<strong>in</strong>g protocolcreates <strong>in</strong> each router does not <strong>in</strong>clude the tunnels. The primary reason for not expos<strong>in</strong>gtunnels to OSPF or IS-IS is the same O(N 2 ) scal<strong>in</strong>g issue discussed <strong>in</strong> the IP-over-ATMcontext <strong>in</strong> the previous chapter * . If the rout<strong>in</strong>g-protocol were exposed to the tunnels, thenthey would have to treat them as l<strong>in</strong>ks and carry state for them, which is a scal<strong>in</strong>gproblem – as the number of l<strong>in</strong>ks <strong>in</strong>creases, more state needs to be dissem<strong>in</strong>ated; andwhen failures happen lots of control messages are generated, which <strong>in</strong>-turn <strong>in</strong>creasesrouter-CPU process<strong>in</strong>g loads and could cause rout<strong>in</strong>g protocol <strong>in</strong>stability.(b)† Assum<strong>in</strong>g all l<strong>in</strong>ks have the same IGP cost and the tunnel cost is that of a s<strong>in</strong>gle-hop.* See Sec. 4.2.1 under <strong>SDN</strong> based Unified <strong>Control</strong> Plane