The Attacker’s Dictionary
rapid7-research-the-attackers-dictionary
rapid7-research-the-attackers-dictionary
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
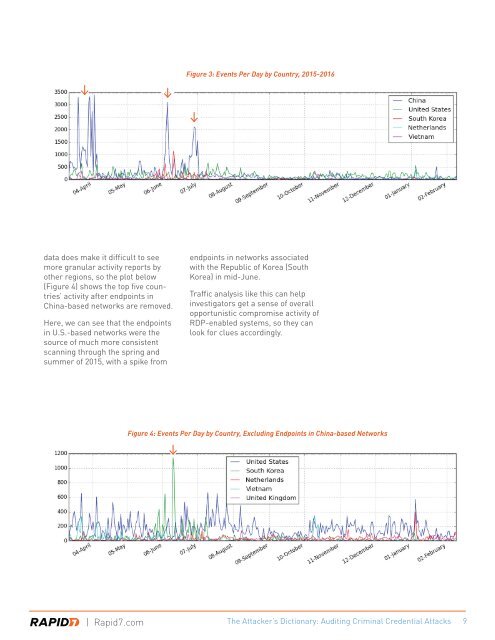
Figure 3: Events Per Day by Country, 2015-2016<br />
data does make it difficult to see<br />
more granular activity reports by<br />
other regions, so the plot below<br />
(Figure 4) shows the top five countries’<br />
activity after endpoints in<br />
China-based networks are removed.<br />
Here, we can see that the endpoints<br />
in U.S.-based networks were the<br />
source of much more consistent<br />
scanning through the spring and<br />
summer of 2015, with a spike from<br />
endpoints in networks associated<br />
with the Republic of Korea (South<br />
Korea) in mid-June.<br />
Traffic analysis like this can help<br />
investigators get a sense of overall<br />
opportunistic compromise activity of<br />
RDP-enabled systems, so they can<br />
look for clues accordingly.<br />
Figure 4: Events Per Day by Country, Excluding Endpoints in China-based Networks<br />
| Rapid7.com <strong>The</strong> <strong>Attacker’s</strong> <strong>Dictionary</strong>: Auditing Criminal Credential Attacks 9