- Page 1 and 2:
conference proceedings ISBN 978-1-9
- Page 4 and 5:
Proceedings of NSDI ’17: 14th USE
- Page 6 and 7:
NSDI ’17: 14th USENIX Symposium o
- Page 8 and 9:
Data-Driven Systems Encoding, Fast
- Page 10:
Message from the NSDI ’17 Program
- Page 13 and 14:
• Security. Before reading input
- Page 15 and 16:
3.3 Details of Lepton’s probabili
- Page 17 and 18:
5 Deployment at Scale To deploy Lep
- Page 19 and 20:
p50/p75/p95/p99 time (s) 1.6 1.4 1.
- Page 21 and 22:
0.7 0.6 0.5 0.4 0.3 0.2 0.1 0.0 21:
- Page 23 and 24:
configuration change, it took two h
- Page 25 and 26:
? ? Figure 16: An entire row (or co
- Page 28 and 29:
Decibel: Isolation and Sharing in D
- Page 30 and 31:
Single dVol instance: Per-core runt
- Page 32 and 33:
3K\VLFDO%ORFN$GGUHVVELWV : , ' / EL
- Page 34 and 35:
Throughput (K IOPS) Throughput (K I
- Page 36 and 37:
are admitted. The dVol metadata is
- Page 38 and 39:
Throughput (K IOPS) Latency (us) 18
- Page 40 and 41:
not at the cost of the throughput o
- Page 42 and 43:
ceedings of the 9th USENIX Conferen
- Page 44:
[57] SCHROEDER, B., LAGISETTY, R.,
- Page 47 and 48:
materialized streams. Unlike stream
- Page 49 and 50:
"sequencers": 10.0.0.1, "segments":
- Page 51 and 52:
class User { String name; String pa
- Page 53 and 54:
class CSMRMap implements Map { fina
- Page 55 and 56:
ack to using backpointers. Since th
- Page 57 and 58:
● ● ● ● ● ● ● ● ●
- Page 59 and 60:
[20] Robert Escriva, Bernard Wong,
- Page 62 and 63:
Curator: Self-Managing Storage for
- Page 64 and 65:
Figure 1: Cluster architecture and
- Page 66 and 67:
finds all the extent groups that ha
- Page 68 and 69:
Fraction of Clusters 1 0.8 0.6 0.4
- Page 70 and 71:
decisions on where to put a piece o
- Page 72 and 73:
use negative latencies, 18 i.e., th
- Page 74 and 75:
References [1] Q-learning with Neur
- Page 76 and 77:
D ML-driven Policies Workloads We u
- Page 78 and 79:
Abstract Evaluating the Power of Fl
- Page 80 and 81:
cannot guarantee that forwarded pac
- Page 82 and 83:
Estimate Error (%) 100 80 60 40 20
- Page 84 and 85:
since the last update as t ∆ . Be
- Page 86 and 87:
CDF 1 0.8 0.6 RCP 0.4 RCP-Approx XC
- Page 88 and 89:
perform RCP for long flows and perf
- Page 90 and 91:
References [1] AL-FARES, M., RADHAK
- Page 92 and 93:
A Building Blocks and their Use in
- Page 94 and 95:
APUNet: Revitalizing GPU as Packet
- Page 96 and 97:
Excavator CPU L1 Cache L2 Cache GCN
- Page 98 and 99:
CPU GPU RAM CPU GPU RAM OS CPU / Di
- Page 100 and 101:
W RQ CPU Master M Data Queue Worker
- Page 102 and 103:
Packet latency (us) 18 15 12 9 6 3
- Page 104 and 105:
Throughput (Gbps) 20 15 10 5 0 CPU
- Page 106 and 107:
References [1] Amazon. https://www.
- Page 108 and 109:
Stateless Network Functions: Breaki
- Page 110 and 111:
2 Motivation Simply running virtual
- Page 112 and 113:
Network Function State Key Value Ac
- Page 114 and 115:
network-wide capabilities, and sing
- Page 116 and 117:
create or destroy network functions
- Page 118 and 119: cate with RAMCloud is higher than I
- Page 120 and 121: References [1] Algo-logic systems.
- Page 122 and 123: [43] R. Potharaju and N. Jain. Demy
- Page 124 and 125: mOS: A Reusable Networking Stack fo
- Page 126 and 127: eassembling bi-directional bytestre
- Page 128 and 129: To detect the free-riding attack, w
- Page 130 and 131: (a) (b) (c) seq x Receive buffer si
- Page 132 and 133: ever enough flow data is reassemble
- Page 134 and 135: Throughput (Gbps) 60 50 40 30 20 10
- Page 136 and 137: 8 Acknowledgments We would like to
- Page 138 and 139: [56] S. Peter, J. Li, I. Zhang, D.
- Page 140: Appendix B 1 // count # of packets
- Page 143 and 144: 132 14th USENIX Symposium on Networ
- Page 145 and 146: 134 14th USENIX Symposium on Networ
- Page 147 and 148: 136 14th USENIX Symposium on Networ
- Page 149 and 150: 138 14th USENIX Symposium on Networ
- Page 151 and 152: 140 14th USENIX Symposium on Networ
- Page 153 and 154: 142 14th USENIX Symposium on Networ
- Page 155 and 156: 144 14th USENIX Symposium on Networ
- Page 157 and 158: microarchitectures. We ask ourselve
- Page 159 and 160: ing, generating certificates, and c
- Page 161 and 162: User process (Tor application) Tor-
- Page 163 and 164: are SGX-enabled. However, we also s
- Page 165 and 166: Data structure Tor Network-level ad
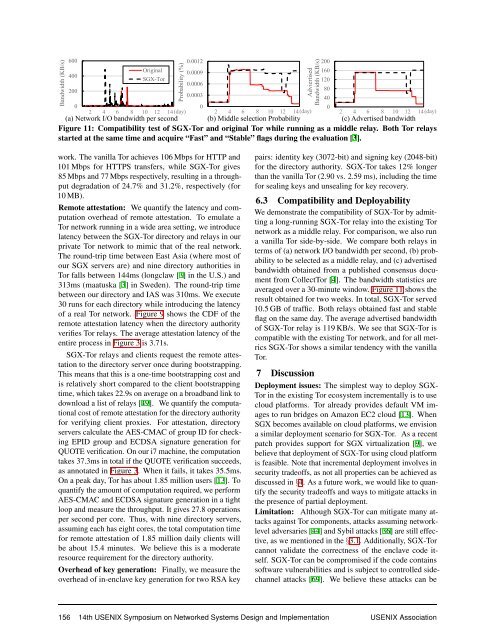
- Page 167: Bandwidth (KB/s) 600 Probability (%
- Page 171 and 172: [61] F. Schuster, M. Costa, C. Four
- Page 174 and 175: ViewMap: Sharing Private In-Vehicle
- Page 176 and 177: samples. Time-series analysis on lo
- Page 178 and 179: time t 1 time t 60 A B VP v B VP x
- Page 180 and 181: Platform Blur time I/O time Frame r
- Page 182 and 183: !""#$%"&'()*' :%,-'45.()*;' 100% 20
- Page 184 and 185: Vehicle 1 Vehicle 2 Vehicle 1 Vehic
- Page 186 and 187: References [1] Top Rider. 2015. Res
- Page 188 and 189: A System to Verify Network Behavior
- Page 190 and 191: OpenSSL and BoringSSL. Verification
- Page 192 and 193: PQ PT PR ! "#$ 1-:$'HF7$5 PS Figure
- Page 194 and 195: void Client ( int x, int y, int iv)
- Page 196 and 197: ●●●●●●●●●●●
- Page 198 and 199: ●●●●●●● ● ●●●
- Page 200 and 201: References [1] B. Anderson, S. Paul
- Page 202 and 203: scheduler thread and one or more wo
- Page 204 and 205: DEFINE_MODEL (void , AES_encrypt ,
- Page 206: int main () { unsigned int x, y; MA
- Page 209 and 210: processing load of a large MIMO sys
- Page 211 and 212: Find the path with the minimum c(s
- Page 213 and 214: 15 th 12 th 13th 16th 8 th 6 th 10
- Page 215 and 216: §3), the corresponding overhead ca
- Page 217 and 218: Througput (Mbit/s) (bars) Geosphere
- Page 219 and 220:
throughput gains for the same numbe
- Page 221 and 222:
Units. European Wireless Conference
- Page 224 and 225:
Facilitating Robust 60 GHz Network
- Page 226 and 227:
AoD Tx array Reflecting point AoA R
- Page 228 and 229:
Algorithm 1 Virtual Beamforming 1:
- Page 230 and 231:
Reflector Reflector Rx’’’ Rx
- Page 232 and 233:
True AoA/AoD (deg.) 360 300 240 180
- Page 234 and 235:
360 300 LOS 0 -5 240 -10 180 -15 12
- Page 236 and 237:
12. References [1] B. Wire, “FCC
- Page 238 and 239:
Skip-Correlation for Multi-Power Wi
- Page 240 and 241:
Figure 4: Example showing need for
- Page 242 and 243:
on a basic property of correlation-
- Page 244 and 245:
Figure 9: Running sum block in Schm
- Page 246 and 247:
A B B can sense A +3dB a) Experimen
- Page 248 and 249:
Probability 10 0 10 -1 η + 10 -2
- Page 250 and 251:
References [1] Aironet 1570 Series
- Page 252 and 253:
µ(C) = { LE 2 N /2 (LE S ) 2 /4 +
- Page 254 and 255:
FM Backscatter: Enabling Connected
- Page 256 and 257:
ter techniques described above and
- Page 258 and 259:
signal shown in Fig. 3. If we norma
- Page 260 and 261:
four FM stations. These plots confi
- Page 262 and 263:
Bit-error rate 0.35 0.3 0.25 0.2 0.
- Page 264 and 265:
PESQ score -20 dBm -30 dBm -40 dBm
- Page 266 and 267:
(a) (b) Figure 15: Talking Poster a
- Page 268 and 269:
[16] Silicon labs si4713-b30-gmr. h
- Page 270 and 271:
Prio: Private, Robust, and Scalable
- Page 272 and 273:
Privacy. Prio provides f -privacy,
- Page 274 and 275:
4.2 Constructing SNIPs To run the S
- Page 276 and 277:
the servers can execute the verific
- Page 278 and 279:
Workstation Phone Field size: 87-bi
- Page 280 and 281:
Client time (s) Lower is better. 10
- Page 282 and 283:
(a) RAPPOR [57] provides differenti
- Page 284 and 285:
[27] Brickell, J., and Shmatikov, V
- Page 286 and 287:
[78] Janosi, A., Steinbrunn, W., Pf
- Page 288 and 289:
there exists an efficient simulator
- Page 290 and 291:
arithmetic confirm that σ i is a s
- Page 292 and 293:
where y i is the true value associa
- Page 294 and 295:
Opaque: An Oblivious and Encrypted
- Page 296 and 297:
other process on the same processor
- Page 298 and 299:
Note that Opaque protects most cons
- Page 300 and 301:
all records that have the same grou
- Page 302 and 303:
SQL Query Opaque Logical Plan SELEC
- Page 304 and 305:
Patient SELECT FROM WHERE ⨝ ⨝ D
- Page 306 and 307:
Normalized runtime 10 2 10 1 10 0 1
- Page 308 and 309:
References [1] AMPlab, University o
- Page 310 and 311:
Splinter: Practical Private Queries
- Page 312 and 313:
answer = r1 + r2 ItemId Price ItemI
- Page 314 and 315:
true on an interval of the range of
- Page 316 and 317:
putation time is O(nlogn) and the c
- Page 318 and 319:
Dataset Query Desc. FSS Scheme Inpu
- Page 320 and 321:
Figure 12: Per-core throughput of v
- Page 322 and 323:
Acknowledgements We thank our anony
- Page 324:
[55] R. J. Rosen. Study: Consumers
- Page 327 and 328:
or desirable. Instead, we created a
- Page 329 and 330:
IGMP Snooping [3], that we don’t
- Page 331 and 332:
On the inbound direction, the layer
- Page 333 and 334:
updated to take as input a FlowID a
- Page 335 and 336:
VFP from the stack, uninstall VFP (
- Page 337 and 338:
however, that our controllers neede
- Page 339 and 340:
[22] Overview of Single Root I/O Vi
- Page 341 and 342:
switch sends a notification to the
- Page 343 and 344:
messages in bounded time - this is
- Page 345 and 346:
Control Application Controller Prox
- Page 347 and 348:
Network Event Controller 1 Aware Aw
- Page 349 and 350:
1 0.8 SCL Consensus 1 0.8 SCL Conse
- Page 351 and 352:
CDF 1 0.8 0.6 0.4 SCL Consensus Tra
- Page 353 and 354:
References [1] A. Akella. Experimen
- Page 355 and 356:
a single path to ensure safety poli
- Page 358 and 359:
Robust validation of network design
- Page 360 and 361:
not discuss this extensively, our f
- Page 362 and 363:
(F)max v,λ,x ∑ t,i≠t d it (v i
- Page 364 and 365:
The robust optimization literature
- Page 366 and 367:
Maximum Link Utilization (MLU) 1.50
- Page 368 and 369:
Maximum Link Utilization (MLU) 3.00
- Page 370 and 371:
A Appendix Proof of Proposition 1:
- Page 372 and 373:
Experience with a globally-deployed
- Page 374 and 375:
Encoding, Fast and Slow: Low-Latenc
- Page 376 and 377:
At the time of writing, AWS Lambda
- Page 378 and 379:
computational power (TFLOPS) 10 9 8
- Page 380 and 381:
initializes the decoder’s state:
- Page 382 and 383:
threads start 25 s 50 s 75 s 100 s
- Page 384 and 385:
average bitrate (Mbit/s) 20 25 30 3
- Page 386 and 387:
er 9, 2015). http://techblog.netfli
- Page 388 and 389:
Live Video Analytics at Scale with
- Page 390 and 391:
1 " name ": " LicensePlate ", 2 " t
- Page 392 and 393:
Deep Neural Network (DNN) Classifie
- Page 394 and 395:
6 U Q 3 query 1 query 2 0 0 Q M 1 0
- Page 396 and 397:
We first distribute the query resou
- Page 398 and 399:
0.95 0.90 0.85 0.80 Quality 1.00 La
- Page 400 and 401:
Scheduling Time (s) 6 5 4 3 2 Numbe
- Page 402 and 403:
[38] G. Cormode, M. Garofalakis, P.
- Page 404 and 405:
Pytheas: Enabling Data-Driven Quali
- Page 406 and 407:
JoinTime (ms) 4000 3500 3000 2500 2
- Page 408 and 409:
Frontend Backend Frontend (a)$Logic
- Page 410 and 411:
6.1 Requirements The Pytheas system
- Page 412 and 413:
Control*decision* [Features,Decisio
- Page 414 and 415:
Throughput (Thousand RPS) 180 160 1
- Page 416 and 417:
[6] How a/b testing works. http://g
- Page 418 and 419:
Let it Flow: Resilient Asymmetric L
- Page 420 and 421:
Scheme Granularity Information need
- Page 422 and 423:
3 Design and Hardware Implementatio
- Page 424 and 425:
Probability 0.5 0.45 0.4 0.35 0.3 0
- Page 426 and 427:
FCT (ms) 15 10 ECMP CONGA Let
- Page 428 and 429:
(e.g. packet loss, increased delay)
- Page 430 and 431:
References [1] M. Al-Fares, A. Louk
- Page 432 and 433:
Flowtune: Flowlet Control for Datac
- Page 434 and 435:
utility 2.0 1.5 1.0 0.5 0.0 0 10 20
- Page 436 and 437:
lb lb lb lb fb fb fb fb lb src fb f
- Page 438 and 439:
Throughput (Gbps) 10.0 7.5 5.0 2.5
- Page 440 and 441:
DCTCP Flowtune pFabric sfqCoDel XCP
- Page 442 and 443:
over−allocation (Gbps) 200 150 10
- Page 444 and 445:
gathered statistics, and at any giv
- Page 446:
[18] GREENBERG, A., HAMILTON, J. R.
- Page 449 and 450:
programmed scheme (Figure 1). The r
- Page 451 and 452:
For simplicity of emulation, all ab
- Page 453 and 454:
3.5 Flexplane APIs Flexplane expose
- Page 455 and 456:
y two. We run DropTail both in Flex
- Page 457 and 458:
6 DCTCP 20 ● 8 Normalized FCT 5 4
- Page 459 and 460:
Throughput (Gbits/s) 125 100 75 50
- Page 461 and 462:
[14] W. Bai, L. Chen, K. Chen, D. H
- Page 464 and 465:
I Can’t Believe It’s Not Causal
- Page 466 and 467:
Buffered Replicated Writes 1200 100
- Page 468 and 469:
# c l i t s i s t h e c l i e n t
- Page 470 and 471:
T 1 : s(1) r(x) w(y=10) c(2) T 3 :
- Page 472 and 473:
dinator recovery [32, 64]. Upon det
- Page 474 and 475:
Goodput (million ops/s) 1.4 1.2 1 0
- Page 476 and 477:
[5] ADYA, A. Weak Consistency: A Ge
- Page 478 and 479:
[65] ZHANG, Y., POWER, R., ZHOU, S.
- Page 480 and 481:
CherryPick: Adaptively Unearthing t
- Page 482 and 483:
Cost model: The cloud charges users
- Page 484 and 485:
leaving the interval between ⃗x 1
- Page 486 and 487:
Figure 6: Architecture of CherryPic
- Page 488 and 489:
(a) Running cost (b) S
- Page 490 and 491:
Figure 13: CherryPick learns dimini
- Page 492 and 493:
References [1] Apache Spark the fas
- Page 494 and 495:
AdaptSize: Orchestrating the Hot Ob
- Page 496 and 497:
Varnish Nginx AdaptSize SIZE-OPT +9
- Page 498 and 499:
average and 75% higher in some case
- Page 500 and 501:
HK trace US trace Total Requests 45
- Page 502 and 503:
Throughput (Gbps) 20 10 0 AdaptSize
- Page 504 and 505:
Byte Hit Ratio 1.00 0.75 0.50 0.25
- Page 506 and 507:
Appendix A Proof of Theorem 1 The r
- Page 508 and 509:
[37] JELENKOVIĆ, P. R., AND RADOVA
- Page 510 and 511:
Bringing IoT to Sports Analytics Ma
- Page 512:
Figure 2: Ball instrumentation: (a)
- Page 515 and 516:
Angle (degrees) 50 0 -50 Groundtrut
- Page 517 and 518:
jectory (derived from ViCon). The p
- Page 519 and 520:
(For example, if the integer ambigu
- Page 521 and 522:
Cumulative Angle (degrees) 4000 300
- Page 523 and 524:
[2] adidas micoach smart ball. http
- Page 526 and 527:
FarmBeats: An IoT Platform for Data
- Page 528 and 529:
as shown in Table 1), farms do not
- Page 530 and 531:
γ Minimum Data-Gap Parameters O T
- Page 532 and 533:
Front side (a) Omni-directional dro
- Page 534 and 535:
4 7.5 60 3.5 7 59 3 6.5 58 2.5 6 57
- Page 536 and 537:
3 4 5 Video Length (min) (a) (b) (c
- Page 538 and 539:
REFERENCES [1] IEEE 802.11af: https
- Page 540:
sist in UAV path planning. On a hig
- Page 543 and 544:
hand can block the signal. Said dif
- Page 545 and 546:
User rotated her head AP SNR (in dB
- Page 547 and 548:
Leakage TX to RX(in dB) -50 -60 -70
- Page 549 and 550:
MoVR estimates φ AP . To estimate
- Page 551 and 552:
CDF 1 0.8 0.6 0.4 0.2 0 0 200 400 6
- Page 553 and 554:
10 No Mirror 30 8 Concluding Remark
- Page 555 and 556:
[44] SUR, S., VENKATESWARAN, V., ZH
- Page 557 and 558:
that exhibit high degree of collect
- Page 559 and 560:
time (s) 35 30 25 20 15 10 5 Lab us
- Page 561 and 562:
Figure 6: A heatmap of the collecti
- Page 563 and 564:
Figure 9: WebGaze architecture. 5.2
- Page 565 and 566:
Alternative # WebGaze # WebGaze # W
- Page 567 and 568:
8 Discussions There are several tec
- Page 569 and 570:
[27] GAZEPOINTER. Control mouse cur
- Page 572 and 573:
RAIL: A Case for Redundant Arrays o
- Page 574 and 575:
(a) 10Gbps multi-mode (b) 10Gbps si
- Page 576 and 577:
Figure 7: Price and reach of standa
- Page 578 and 579:
The speed of the above algorithm de
- Page 580 and 581:
Figure 10: Our 10G-SR testbed. We s
- Page 582 and 583:
(a) 10Gbps (b) 40Gbps Figure 14: To
- Page 584 and 585:
Acknowledgments We thank Keren Berg
- Page 586 and 587:
Today, data center operators chose
- Page 588 and 589:
Enabling Wide-spread Communications
- Page 590 and 591:
copies of data to be stored in diff
- Page 592 and 593:
40dB 30dB 20dB 0 5 10 15 # nodes on
- Page 594 and 595:
Figure 8: The OWS box we implemente
- Page 596 and 597:
Mbps Mbps 4×10 5 2×10 5 (a) 0 0s
- Page 598 and 599:
1.0 0.5 0 1.0 0.5 0 (a) % Full Bise
- Page 600 and 601:
References [1] AL-FARES, M., LOUKIS
- Page 602 and 603:
internet applications. ACM SIGCOMM
- Page 604:
when the capacity of basemesh is in
- Page 607 and 608:
the topological regularity of Faceb
- Page 609 and 610:
Figure 1: High-level system overvie
- Page 611 and 612:
metrics can be used to find under-p
- Page 613 and 614:
computes a lightweight statistic fo
- Page 615 and 616:
0.80 0.60 0.40 0.20 0.05 10 40 60 1
- Page 617 and 618:
the majority of traffic is routed a
- Page 619 and 620:
8. REFERENCES [1] ab - Apache HTTP
- Page 621 and 622:
Syscall latency (nsec) 10 8 10 7 10
- Page 623 and 624:
Syscall latency (nsec) 10 7 10 6 10
- Page 625 and 626:
Consequently, models can be modifie
- Page 627 and 628:
over, the low and bounded latency d
- Page 629 and 630:
Latency (¹s) Latency (¹s) 35000 3
- Page 631 and 632:
Throughput (10K qps) Latency (ms) 1
- Page 633 and 634:
Cumulative Average Error 0.5 0.4 0.
- Page 635 and 636:
duced by Clipper’s layered archit
- Page 637 and 638:
References [1] M. Abadi, A. Agarwal
- Page 640 and 641:
Gaia: Geo-Distributed Machine Learn
- Page 643:
Network Bandwidth (Mb/s) 1000 900 8
- Page 648 and 649:
ization factorizes X into factor ma
- Page 650 and 651:
Normliaed Cost 2.5 2 1.5 1 0.5 0 Ma
- Page 652 and 653:
Acknowledgments We thank our shephe
- Page 654 and 655:
[55] C. Olston, J. Jiang, and J. Wi
- Page 656 and 657:
〈 x˜ t − x ∗ , g˜ t 〉 = 1
- Page 658:
inaccurate, values in order to get
- Page 661 and 662:
Memcached ETC SYS 100% 95.83 93.87
- Page 663 and 664:
Container 1 … Container N Infinis
- Page 665 and 666:
Each RDMA dispatch queue has a limi
- Page 667 and 668:
We have implemented INFINISWAP as a
- Page 669 and 670:
workloads with different rates of S
- Page 671 and 672:
Completion time (s) 5000 4000 3000
- Page 673 and 674:
[3] Amazon EC2 Pricing. https://aws
- Page 675 and 676:
[59] F. Mietke, R. Rex, R. Baumgart
- Page 677 and 678:
Send QUERY_MEM messages Receive FRE
- Page 680 and 681:
TUX 2 : Distributed Graph Computati
- Page 682 and 683:
Model: User 0 rƸ ui = q T i p u Us
- Page 684 and 685:
dates. This is because they are sca
- Page 686 and 687:
ExchangeStage:: Exchange(v_doc, v_w
- Page 688 and 689:
Time per iteration (s) 140 120 100
- Page 690 and 691:
Time per iteration (s) 1000 100 10
- Page 692 and 693:
[3] Petuum v0.93. https://github.co
- Page 694 and 695:
Correct by Construction Networks us
- Page 696 and 697:
zone 1 security policy core zone 3
- Page 698 and 699:
RouterZoneIn RouterZoneOut zone cor
- Page 700 and 701:
possible outputs of ^R on this pack
- Page 702 and 703:
vm1 vm2 vm3 vnet 1 vrouter vm4 vm5
- Page 704 and 705:
Scale Hosts Switches NetKAT Policy
- Page 706 and 707:
References [1] M. Al-Fares, A. Louk
- Page 708 and 709:
given in terms of: • a packet p
- Page 710 and 711:
Verifying Reachability in Networks
- Page 712 and 713:
function with a set of packets to f
- Page 714 and 715:
Intrusion Prevention Systems We con
- Page 716 and 717:
parallel and origin-agnostic middle
- Page 718 and 719:
Time (seconds) 500 450 400 350 300
- Page 720 and 721:
1000 1000 Subnet 1 100 100 SB Time
- Page 722 and 723:
References [1] AMAZON. Amazon EC2 S
- Page 724 and 725:
[56] VELNER, Y., ALPERNAS, K., PAND
- Page 726 and 727:
uration parameters that control, e.
- Page 728 and 729:
C Formal Definition of Slices Given
- Page 730 and 731:
Automated Bug Removal for Software-
- Page 732 and 733:
1 FlowTable(@Swi,Hdr,Prt) :- Packet
- Page 734 and 735:
h1 Tuple(@C,Tab,Val1,Val2) :- Base(
- Page 736 and 737:
function GENERATEREPAIRCANDIDATES(P
- Page 738 and 739:
7(v1) FlowTable(@Swi,Hdr,Prt) :- Pa
- Page 740 and 741:
Query description Result Q1 H20 is
- Page 742 and 743:
Q1 Q2 Q3 Q4 Q5 Trema (Ruby) 7/2 10/
- Page 744:
[33] D. Logothetis, S. De, and K. Y
- Page 747 and 748:
To address this problem, this paper
- Page 749 and 750:
s 2 s 3 r 1 r 2 r 3 s 1 r 4 s 4 (a)
- Page 751 and 752:
in the graph on which link(r) is in
- Page 753 and 754:
Algorithm 3 Compute all-pairs reach
- Page 755 and 756:
CDF 1 0.8 0.6 0.4 0.2 0 Berkley INE
- Page 757 and 758:
48, 26, 35, 17, 33] and online [27,
- Page 759 and 760:
[41] NUNES, B. A. A., MENDONCA, M.,