The Nino Cipher
2nofXEA
2nofXEA
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
H(K)<br />
K<br />
[3]<br />
K<br />
[2]<br />
K<br />
[1]<br />
K<br />
[0]<br />
101<br />
32<br />
24<br />
16<br />
8<br />
0<br />
102<br />
HE(K0)<br />
111<br />
110<br />
HE(K3)<br />
HE(K3)<br />
HE(M3)<br />
HE(K2)<br />
HE(K1)<br />
HE(M2)<br />
HE(M3)<br />
108<br />
103<br />
105<br />
104<br />
HE(M1)<br />
HE(M0)<br />
107<br />
0 1 2 3 4<br />
HE(K1)<br />
HE(M1)<br />
5 6 7 8<br />
C[0] C[1] C[2] C[3] C[4] C[5] C[6] C[7]<br />
106<br />
HE(K2)<br />
HE(M2)<br />
109<br />
8<br />
8<br />
XOR(K1)<br />
XOR(K1)<br />
M[0]<br />
M[1]<br />
M[2] M[3] M[4] M[5] M[6] M[7]<br />
SECURITY GUARANTEE ZONE (M1)<br />
SECURITY GUARANTEE ZONE (M2)<br />
INSECURITY GUARANTEE<br />
ZONE (M1)<br />
112 113<br />
114 115<br />
8<br />
8<br />
INSECURITY GUARANTEE<br />
ZONE (M2)<br />
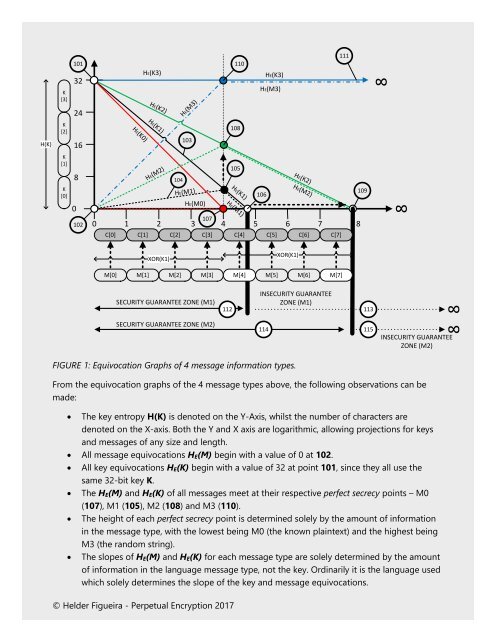
FIGURE 1: Equivocation Graphs of 4 message information types.<br />
From the equivocation graphs of the 4 message types above, the following observations can be<br />
made:<br />
• <strong>The</strong> key entropy H(K) is denoted on the Y-Axis, whilst the number of characters are<br />
denoted on the X-axis. Both the Y and X axis are logarithmic, allowing projections for keys<br />
and messages of any size and length.<br />
• All message equivocations H E(M) begin with a value of 0 at 102.<br />
• All key equivocations H E(K) begin with a value of 32 at point 101, since they all use the<br />
same 32-bit key K.<br />
• <strong>The</strong> H E(M) and H E(K) of all messages meet at their respective perfect secrecy points – M0<br />
(107), M1 (105), M2 (108) and M3 (110).<br />
• <strong>The</strong> height of each perfect secrecy point is determined solely by the amount of information<br />
in the message type, with the lowest being M0 (the known plaintext) and the highest being<br />
M3 (the random string).<br />
• <strong>The</strong> slopes of H E(M) and H E(K) for each message type are solely determined by the amount<br />
of information in the language message type, not the key. Ordinarily it is the language used<br />
which solely determines the slope of the key and message equivocations.<br />
© Helder Figueira - Perpetual Encryption 2017