412-79V9 Exam Practice Software
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
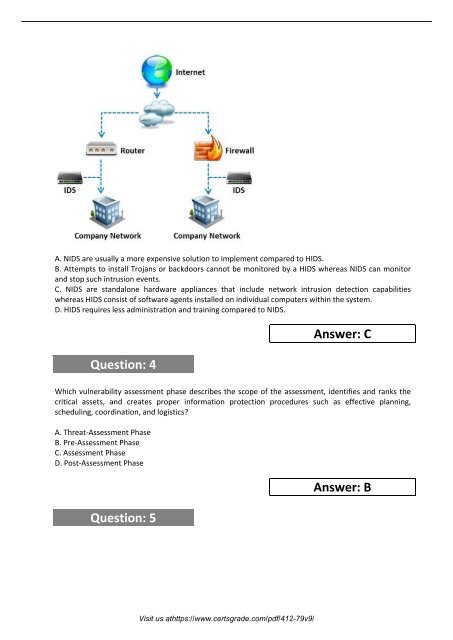
A. NIDS are usually a more expensive solution to implement compared to HIDS.<br />
B. Attempts to install Trojans or backdoors cannot be monitored by a HIDS whereas NIDS can monitor<br />
and stop such intrusion events.<br />
C. NIDS are standalone hardware appliances that include network intrusion detection capabilities<br />
whereas HIDS consist of software agents installed on individual computers within the system.<br />
D. HIDS requires less administration and training compared to NIDS.<br />
Question: 4<br />
Answer: C<br />
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the<br />
critical assets, and creates proper information protection procedures such as effective planning,<br />
scheduling, coordination, and logistics?<br />
A. Threat-Assessment Phase<br />
B. Pre-Assessment Phase<br />
C. Assessment Phase<br />
D. Post-Assessment Phase<br />
Question: 5<br />
Answer: B<br />
Visit us athttps://www.certsgrade.com/pdf/<strong>412</strong>-79v9/