- Page 2 and 3:
This page intentionally left blank
- Page 4 and 5:
This page intentionally left blank
- Page 6 and 7:
Many of the designations used by ma
- Page 8 and 9:
CONTENTS Preface . . . . . . . . .
- Page 10 and 11:
PREFACE This book is intended to su
- Page 12 and 13:
Booksite An important feature of th
- Page 14 and 15:
Acknowledgments This book has been
- Page 16 and 17:
ONE Fundamentals 1.1 Basic Programm
- Page 18 and 19:
4 CHAPTER 1 ■ Fundamentals Algor
- Page 20 and 21:
6 CHAPTER 1 ■ Fundamentals of the
- Page 22 and 23:
1.1 BASIC PROGRAMMING MODEL Our stu
- Page 24 and 25:
10 CHAPTER 1 ■ Fundamentals Basic
- Page 26 and 27:
12 CHAPTER 1 ■ Fundamentals To de
- Page 28 and 29:
14 CHAPTER 1 ■ Fundamentals State
- Page 30 and 31:
16 CHAPTER 1 ■ Fundamentals Short
- Page 32 and 33:
18 CHAPTER 1 ■ Fundamentals Ar r
- Page 34 and 35:
20 CHAPTER 1 ■ Fundamentals doubl
- Page 36 and 37:
22 CHAPTER 1 ■ Fundamentals signa
- Page 38 and 39:
24 CHAPTER 1 ■ Fundamentals P ro
- Page 40 and 41:
26 CHAPTER 1 ■ Fundamentals Basic
- Page 42 and 43:
28 CHAPTER 1 ■ Fundamentals APIs
- Page 44 and 45:
30 CHAPTER 1 ■ Fundamentals Our s
- Page 46 and 47:
32 CHAPTER 1 ■ Fundamentals inten
- Page 48 and 49:
34 CHAPTER 1 ■ Fundamentals St r
- Page 50 and 51:
36 CHAPTER 1 ■ Fundamentals stand
- Page 52 and 53:
38 CHAPTER 1 ■ Fundamentals conve
- Page 54 and 55:
40 CHAPTER 1 ■ Fundamentals Re di
- Page 56 and 57:
42 CHAPTER 1 ■ Fundamentals Stand
- Page 58 and 59:
44 CHAPTER 1 ■ Fundamentals In th
- Page 60 and 61:
46 CHAPTER 1 ■ Fundamentals Binar
- Page 62 and 63:
48 CHAPTER 1 ■ Fundamentals White
- Page 64 and 65:
50 CHAPTER 1 ■ Fundamentals Persp
- Page 66 and 67:
52 CHAPTER 1 ■ Fundamentals Q&A (
- Page 68 and 69:
54 CHAPTER 1 ■ Fundamentals EXERC
- Page 70 and 71:
56 CHAPTER 1 ■ Fundamentals EXERC
- Page 72 and 73:
58 CHAPTER 1 ■ Fundamentals EXERC
- Page 74 and 75:
60 CHAPTER 1 ■ Fundamentals CREAT
- Page 76 and 77:
62 CHAPTER 1 ■ Fundamentals EXPER
- Page 78 and 79:
1.2 DATA ABSTRACTION A data type is
- Page 80 and 81:
66 CHAPTER 1 ■ Fundamentals ■ I
- Page 82 and 83:
68 CHAPTER 1 ■ Fundamentals thems
- Page 84 and 85:
70 CHAPTER 1 ■ Fundamentals publi
- Page 86 and 87:
72 CHAPTER 1 ■ Fundamentals Ar ra
- Page 88 and 89:
74 CHAPTER 1 ■ Fundamentals Examp
- Page 90 and 91:
76 CHAPTER 1 ■ Fundamentals Ge o
- Page 92 and 93:
78 CHAPTER 1 ■ Fundamentals Infor
- Page 94 and 95:
80 CHAPTER 1 ■ Fundamentals St r
- Page 96 and 97:
82 CHAPTER 1 ■ Fundamentals as th
- Page 98 and 99:
84 CHAPTER 1 ■ Fundamentals Imple
- Page 100 and 101:
86 CHAPTER 1 ■ Fundamentals impli
- Page 102 and 103:
88 CHAPTER 1 ■ Fundamentals API,
- Page 104 and 105:
90 CHAPTER 1 ■ Fundamentals More
- Page 106 and 107:
92 CHAPTER 1 ■ Fundamentals diffe
- Page 108 and 109:
94 CHAPTER 1 ■ Fundamentals Visua
- Page 110 and 111:
96 CHAPTER 1 ■ Fundamentals Data-
- Page 112 and 113:
98 CHAPTER 1 ■ Fundamentals Algor
- Page 114 and 115:
100 CHAPTER 1 ■ Fundamentals Int
- Page 116 and 117:
102 CHAPTER 1 ■ Fundamentals St r
- Page 118 and 119:
104 CHAPTER 1 ■ Fundamentals Me m
- Page 120 and 121:
106 CHAPTER 1 ■ Fundamentals you
- Page 122 and 123:
108 CHAPTER 1 ■ Fundamentals an i
- Page 124 and 125:
110 CHAPTER 1 ■ Fundamentals Q &
- Page 126 and 127:
112 CHAPTER 1 ■ Fundamentals Q &
- Page 128 and 129:
114 CHAPTER 1 ■ Fundamentals EXER
- Page 130 and 131:
116 CHAPTER 1 ■ Fundamentals EXER
- Page 132 and 133:
118 CHAPTER 1 ■ Fundamentals CREA
- Page 134 and 135:
1.3 BAGS, QUEUES, AND STACKS Severa
- Page 136 and 137:
122 CHAPTER 1 ■ Fundamentals Ge n
- Page 138 and 139:
124 CHAPTER 1 ■ Fundamentals Bags
- Page 140 and 141:
126 CHAPTER 1 ■ Fundamentals enqu
- Page 142 and 143:
128 CHAPTER 1 ■ Fundamentals Ar i
- Page 144 and 145:
130 CHAPTER 1 ■ Fundamentals is e
- Page 146 and 147:
132 CHAPTER 1 ■ Fundamentals StdI
- Page 148 and 149:
134 CHAPTER 1 ■ Fundamentals Ge n
- Page 150 and 151:
136 CHAPTER 1 ■ Fundamentals Arra
- Page 152 and 153:
138 CHAPTER 1 ■ Fundamentals Ite
- Page 154 and 155:
140 CHAPTER 1 ■ Fundamentals deta
- Page 156 and 157:
142 CHAPTER 1 ■ Fundamentals Link
- Page 158 and 159:
144 CHAPTER 1 ■ Fundamentals When
- Page 160 and 161:
146 CHAPTER 1 ■ Fundamentals Othe
- Page 162 and 163:
148 CHAPTER 1 ■ Fundamentals StdI
- Page 164 and 165:
150 CHAPTER 1 ■ Fundamentals Queu
- Page 166 and 167:
to be to or be to null null null or
- Page 168 and 169:
154 CHAPTER 1 ■ Fundamentals B ag
- Page 170 and 171:
156 CHAPTER 1 ■ Fundamentals Over
- Page 172 and 173:
158 CHAPTER 1 ■ Fundamentals Q&A
- Page 174 and 175:
160 CHAPTER 1 ■ Fundamentals Q &
- Page 176 and 177:
162 CHAPTER 1 ■ Fundamentals EXER
- Page 178 and 179:
164 CHAPTER 1 ■ Fundamentals LINK
- Page 180 and 181:
166 CHAPTER 1 ■ Fundamentals LINK
- Page 182 and 183:
168 CHAPTER 1 ■ Fundamentals CREA
- Page 184 and 185:
170 CHAPTER 1 ■ Fundamentals CREA
- Page 186 and 187:
1.4 ANALYSIS OF ALGORITHMS AS peopl
- Page 188 and 189:
174 CHAPTER 1 ■ Fundamentals % mo
- Page 190 and 191:
176 CHAPTER 1 ■ Fundamentals Anal
- Page 192 and 193:
178 CHAPTER 1 ■ Fundamentals So f
- Page 194 and 195:
180 CHAPTER 1 ■ Fundamentals Appr
- Page 196 and 197:
182 CHAPTER 1 ■ Fundamentals prog
- Page 198 and 199:
184 CHAPTER 1 ■ Fundamentals Summ
- Page 200 and 201:
186 CHAPTER 1 ■ Fundamentals Orde
- Page 202 and 203:
188 CHAPTER 1 ■ Fundamentals stan
- Page 204 and 205:
190 CHAPTER 1 ■ Fundamentals prop
- Page 206 and 207:
192 CHAPTER 1 ■ Fundamentals Doub
- Page 208 and 209:
194 CHAPTER 1 ■ Fundamentals so t
- Page 210 and 211:
196 CHAPTER 1 ■ Fundamentals some
- Page 212 and 213:
198 CHAPTER 1 ■ Fundamentals run
- Page 214 and 215:
200 CHAPTER 1 ■ Fundamentals type
- Page 216 and 217:
202 CHAPTER 1 ■ Fundamentals Ar r
- Page 218 and 219:
204 CHAPTER 1 ■ Fundamentals Stri
- Page 220 and 221:
206 CHAPTER 1 ■ Fundamentals Q&A
- Page 222 and 223:
208 CHAPTER 1 ■ Fundamentals EXER
- Page 224 and 225:
210 CHAPTER 1 ■ Fundamentals CREA
- Page 226 and 227:
212 CHAPTER 1 ■ Fundamentals CREA
- Page 228 and 229:
214 CHAPTER 1 ■ Fundamentals EXPE
- Page 230 and 231:
1.5 CASE STUDY: UNION-FIND To illus
- Page 232 and 233:
218 CHAPTER 1 ■ Fundamentals conn
- Page 234 and 235:
220 CHAPTER 1 ■ Fundamentals data
- Page 236 and 237:
222 CHAPTER 1 ■ Fundamentals Impl
- Page 238 and 239:
224 CHAPTER 1 ■ Fundamentals 0 Q
- Page 240 and 241:
226 CHAPTER 1 ■ Fundamentals Quic
- Page 242 and 243:
228 CHAPTER 2 ■ Fundamentals ALGO
- Page 244 and 245:
230 CHAPTER 1 ■ Fundamentals quic
- Page 246 and 247:
232 CHAPTER 1 ■ Fundamentals quic
- Page 248 and 249:
234 CHAPTER 1 ■ Fundamentals Q&A
- Page 250 and 251:
236 CHAPTER 1 ■ Fundamentals EXER
- Page 252 and 253:
238 CHAPTER 1 ■ Fundamentals CREA
- Page 254 and 255:
240 CHAPTER 1 ■ Fundamentals EXPE
- Page 256 and 257:
TWO Sor t i ng 2.1 Elementary Sorts
- Page 258 and 259:
2.1 ELEMENTARY SORTS For our first
- Page 260 and 261:
246 CHAPTER 2 ■ Sorting Ce r t if
- Page 262 and 263:
248 CHAPTER 2 ■ Sorting Select io
- Page 264 and 265:
250 CHAPTER 2 ■ Sorting Inser t i
- Page 266 and 267:
252 CHAPTER 2 ■ Sorting More gene
- Page 268 and 269:
254 CHAPTER 2 ■ Sorting Comparing
- Page 270 and 271:
256 CHAPTER 2 ■ Sorting Co m p a
- Page 272 and 273:
258 CHAPTER 2 ■ Sorting h = 4 L E
- Page 274 and 275:
260 CHAPTER 2 ■ Sorting input 13-
- Page 276 and 277:
262 CHAPTER 2 ■ Sorting can break
- Page 278 and 279:
264 CHAPTER 2 ■ Sorting EXERCISES
- Page 280 and 281:
266 CHAPTER 2 ■ Sorting CREATIVE
- Page 282 and 283:
268 CHAPTER 2 ■ Sorting EXPERIMEN
- Page 284 and 285:
2.2 MERGESORT The algorithms that w
- Page 286 and 287:
272 CHAPTER 2 ■ Sorting Top-dow n
- Page 288 and 289:
274 CHAPTER 2 ■ Sorting term is t
- Page 290 and 291:
276 CHAPTER 2 ■ Sorting first sub
- Page 292 and 293:
278 CHAPTER 2 ■ Sorting Bottom-up
- Page 294 and 295:
280 CHAPTER 2 ■ Sorting Propositi
- Page 296 and 297:
282 CHAPTER 2 ■ Sorting than ~ N
- Page 298 and 299:
284 CHAPTER 2 ■ Sorting EXERCISES
- Page 300 and 301:
286 CHAPTER 2 ■ Sorting CREATIVE
- Page 302 and 303:
2.3 QUICKSORT The subject of this s
- Page 304 and 305:
290 CHAPTER 2 ■ Sorting before du
- Page 306 and 307:
292 CHAPTER 2 ■ Sorting Partition
- Page 308 and 309:
294 CHAPTER 2 ■ Sorting C N = N
- Page 310 and 311:
296 CHAPTER 2 ■ Sorting If your s
- Page 312 and 313:
298 CHAPTER 2 ■ Sorting One strai
- Page 314 and 315:
300 CHAPTER 2 ■ Sorting equal to
- Page 316 and 317:
302 CHAPTER 2 ■ Sorting Q & A Q.
- Page 318 and 319:
304 CHAPTER 2 ■ Sorting EXERCISES
- Page 320 and 321:
306 CHAPTER 2 ■ Sorting CREATIVE
- Page 322 and 323:
2.4 PRIORITY QUEUES Many applicatio
- Page 324 and 325:
310 CHAPTER 2 ■ Sorting A priorit
- Page 326 and 327:
312 CHAPTER 2 ■ Sorting data stru
- Page 328 and 329:
314 CHAPTER 2 ■ Sorting Definitio
- Page 330 and 331:
316 CHAPTER 2 ■ Sorting violates
- Page 332 and 333:
318 CHAPTER 2 ■ Sorting ALGORITHM
- Page 334 and 335:
320 CHAPTER 2 ■ Sorting Ar ray re
- Page 336 and 337:
322 CHAPTER 2 ■ Sorting M u lti w
- Page 338 and 339:
324 CHAPTER 2 ■ Sorting ALGORITHM
- Page 340 and 341:
326 CHAPTER 2 ■ Sorting input hea
- Page 342 and 343:
328 CHAPTER 2 ■ Sorting Q&A Q. I
- Page 344 and 345:
330 CHAPTER 2 ■ Sorting EXERCISES
- Page 346 and 347:
332 CHAPTER 2 ■ Sorting CREATIVE
- Page 348 and 349:
334 CHAPTER 2 ■ Sorting CREATIVE
- Page 350 and 351:
2.5 APPLICATIONS Sorting algorithms
- Page 352 and 353:
338 CHAPTER 2 ■ Sorting Pointer s
- Page 354 and 355:
340 CHAPTER 2 ■ Sorting Priority
- Page 356 and 357:
342 CHAPTER 2 ■ Sorting Which sor
- Page 358 and 359:
344 CHAPTER 2 ■ Sorting ■ A dif
- Page 360 and 361:
346 CHAPTER 2 ■ Sorting statistic
- Page 362 and 363:
348 CHAPTER 2 ■ Sorting A brief s
- Page 364 and 365:
350 CHAPTER 2 ■ Sorting example,
- Page 366 and 367:
352 CHAPTER 2 ■ Sorting Q & A Q.
- Page 368 and 369:
354 CHAPTER 2 ■ Sorting EXERCISES
- Page 370 and 371:
356 CHAPTER 2 ■ Sorting CREATIVE
- Page 372 and 373:
358 CHAPTER 2 ■ Sorting EXPERIMEN
- Page 374 and 375:
THREE Se a rch i ng 3.1 Symbol Tabl
- Page 376 and 377:
3.1 SYMBOL TABLES The primary purpo
- Page 378 and 379:
364 CHAPTER 3 ■ Searching entries
- Page 380 and 381:
366 CHAPTER 3 ■ Searching Ordered
- Page 382 and 383:
368 CHAPTER 3 ■ Searching Range q
- Page 384 and 385:
370 CHAPTER 3 ■ Searching keys va
- Page 386 and 387:
372 CHAPTER 3 ■ Searching A symbo
- Page 388 and 389:
374 CHAPTER 3 ■ Searching Sequent
- Page 390 and 391:
376 CHAPTER 3 ■ Searching charact
- Page 392 and 393:
378 CHAPTER 3 ■ Searching Binar y
- Page 394 and 395:
380 CHAPTER 3 ■ Searching public
- Page 396 and 397:
382 CHAPTER 3 ■ Searching A LG O
- Page 398 and 399:
384 CHAPTER 3 ■ Searching method
- Page 400 and 401:
386 CHAPTER 3 ■ Searching quickly
- Page 402 and 403:
388 CHAPTER 3 ■ Searching Q&A (co
- Page 404 and 405:
390 CHAPTER 3 ■ Searching EXERCIS
- Page 406 and 407:
392 CHAPTER 3 ■ Searching CREATIV
- Page 408 and 409:
394 CHAPTER 3 ■ Searching EXPERIM
- Page 410 and 411:
3.2 BINARY SEARCH TREES a subtree I
- Page 412 and 413:
398 CHAPTER 3 ■ Searching ALGORIT
- Page 414 and 415:
400 CHAPTER 3 ■ Searching success
- Page 416 and 417:
402 CHAPTER 3 ■ Searching key val
- Page 418 and 419:
404 CHAPTER 3 ■ Searching Proposi
- Page 420 and 421:
406 CHAPTER 3 ■ Searching Order-b
- Page 422 and 423:
408 CHAPTER 3 ■ Searching go left
- Page 424 and 425:
410 CHAPTER 3 ■ Searching availab
- Page 426 and 427:
412 CHAPTER 3 ■ Searching Range q
- Page 428 and 429:
414 CHAPTER 3 ■ Searching in loga
- Page 430 and 431:
416 CHAPTER 3 ■ Searching EXERCIS
- Page 432 and 433:
418 CHAPTER 3 ■ Searching EXERCIS
- Page 434 and 435:
420 CHAPTER 3 ■ Searching CREATIV
- Page 436 and 437:
422 CHAPTER 3 ■ Searching EXPERIM
- Page 438 and 439:
3.3 BALANCED SEARCH TREES The algor
- Page 440 and 441:
426 CHAPTER 3 ■ Searching inserti
- Page 442 and 443:
428 CHAPTER 3 ■ Searching links c
- Page 444 and 445:
430 CHAPTER 3 ■ Searching insert
- Page 446 and 447:
432 CHAPTER 3 ■ Searching Re d-bl
- Page 448 and 449:
434 CHAPTER 3 ■ Searching h less
- Page 450 and 451:
436 CHAPTER 3 ■ Searching ■ ■
- Page 452 and 453: 438 CHAPTER 3 ■ Searching In summ
- Page 454 and 455: 440 CHAPTER 3 ■ Searching insert
- Page 456 and 457: 442 CHAPTER 3 ■ Searching Remarka
- Page 458 and 459: 444 CHAPTER 3 ■ Searching Propert
- Page 460 and 461: 446 CHAPTER 3 ■ Searching 20 comp
- Page 462 and 463: 448 CHAPTER 3 ■ Searching Q&A Q.
- Page 464 and 465: 450 CHAPTER 3 ■ Searching EXERCIS
- Page 466 and 467: 452 CHAPTER 3 ■ Searching CREATIV
- Page 468 and 469: 454 CHAPTER 3 ■ Searching CREATIV
- Page 470 and 471: 456 CHAPTER 3 ■ Searching EXPERIM
- Page 472 and 473: 3.4 HASH TABLES key hash value a 2
- Page 474 and 475: 460 CHAPTER 3 ■ Searching M - 1.
- Page 476 and 477: 462 CHAPTER 3 ■ Searching public
- Page 478 and 479: 464 CHAPTER 3 ■ Searching key has
- Page 480 and 481: 466 CHAPTER 3 ■ Searching Proposi
- Page 482 and 483: 468 CHAPTER 3 ■ Searching 125 = 1
- Page 484 and 485: 470 CHAPTER 3 ■ Searching ALGORIT
- Page 486 and 487: 472 CHAPTER 3 ■ Searching before
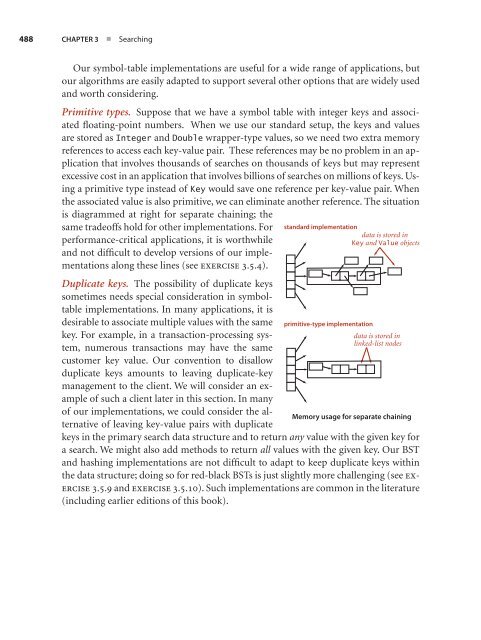
- Page 488 and 489: 474 CHAPTER 3 ■ Searching Proposi
- Page 490 and 491: 476 CHAPTER 3 ■ Searching The plo
- Page 492 and 493: 478 CHAPTER 3 ■ Searching Q&A Q.
- Page 494 and 495: 480 CHAPTER 3 ■ Searching EXERCIS
- Page 496 and 497: 482 CHAPTER 3 ■ Searching EXERCIS
- Page 498 and 499: 484 CHAPTER 3 ■ Searching CREATIV
- Page 500 and 501: 3.5 APPLICATIONS From the early day
- Page 504 and 505: 490 CHAPTER 3 ■ Searching Extendi
- Page 506 and 507: 492 CHAPTER 3 ■ Searching Diction
- Page 508 and 509: 494 CHAPTER 3 ■ Searching % more
- Page 510 and 511: 496 CHAPTER 3 ■ Searching of thin
- Page 512 and 513: 498 CHAPTER 3 ■ Searching Inv e r
- Page 514 and 515: 500 CHAPTER 3 ■ Searching FileInd
- Page 516 and 517: 502 CHAPTER 3 ■ Searching Sparse
- Page 518 and 519: 504 CHAPTER 3 ■ Searching array o
- Page 520 and 521: 506 CHAPTER 3 ■ Searching Q&A Q.
- Page 522 and 523: 508 CHAPTER 3 ■ Searching EXERCIS
- Page 524 and 525: 510 CHAPTER 3 ■ Searching CREATIV
- Page 526 and 527: 512 CHAPTER 3 ■ Searching CREATIV
- Page 528 and 529: FOUR Graphs 4.1 Undirected Graphs .
- Page 530 and 531: 516 CHAPTER 4 ■ Graphs Maps. A pe
- Page 532 and 533: 4.1 UNDIRECTED GRAPHS Our stARting
- Page 534 and 535: 520 CHAPTER 4 ■ Graphs An acyclic
- Page 536 and 537: 522 CHAPTER 4 ■ Graphs Undirected
- Page 538 and 539: 524 CHAPTER 4 ■ Graphs Re pres e
- Page 540 and 541: 526 CHAPTER 4 ■ Graphs Graph data
- Page 542 and 543: 528 CHAPTER 4 ■ Graphs Design pat
- Page 544 and 545: 530 CHAPTER 4 ■ Graphs maze graph
- Page 546 and 547: 532 CHAPTER 4 ■ Graphs tinyCG.txt
- Page 548 and 549: 534 CHAPTER 4 ■ Graphs This basic
- Page 550 and 551: 536 CHAPTER 4 ■ Graphs ALGORITHM
- Page 552 and 553:
538 CHAPTER 4 ■ Graphs Breadth-fi
- Page 554 and 555:
540 CHAPTER 4 ■ Graphs ALGORITHM
- Page 556 and 557:
542 CHAPTER 4 ■ Graphs 20% 40% 60
- Page 558 and 559:
544 CHAPTER 4 ■ Graphs ALGORITHM
- Page 560 and 561:
546 CHAPTER 4 ■ Graphs connected(
- Page 562 and 563:
548 CHAPTER 4 ■ Graphs routes.txt
- Page 564 and 565:
550 CHAPTER 4 ■ Graphs public sta
- Page 566 and 567:
552 CHAPTER 4 ■ Graphs Sy m bo l
- Page 568 and 569:
554 CHAPTER 4 ■ Graphs friends ab
- Page 570 and 571:
556 CHAPTER 4 ■ Graphs Summary In
- Page 572 and 573:
558 CHAPTER 4 ■ Graphs EXERCISES
- Page 574 and 575:
560 CHAPTER 4 ■ Graphs EXERCISES
- Page 576 and 577:
562 CHAPTER 4 ■ Graphs CREATIVE P
- Page 578 and 579:
564 CHAPTER 4 ■ Graphs EXPERIMENT
- Page 580 and 581:
4.2 DIRECTED GRAPHS In directed gra
- Page 582 and 583:
568 CHAPTER 4 ■ Graphs Digraph da
- Page 584 and 585:
570 CHAPTER 4 ■ Graphs Re achabil
- Page 586 and 587:
572 CHAPTER 4 ■ Graphs dfs(0) dfs
- Page 588 and 589:
574 CHAPTER 4 ■ Graphs Cycles and
- Page 590 and 591:
576 CHAPTER 4 ■ Graphs Cycles in
- Page 592 and 593:
578 CHAPTER 4 ■ Graphs When execu
- Page 594 and 595:
580 CHAPTER 4 ■ Graphs D e pth- f
- Page 596 and 597:
582 CHAPTER 4 ■ Graphs Propositio
- Page 598 and 599:
584 CHAPTER 4 ■ Graphs St rong co
- Page 600 and 601:
586 CHAPTER 4 ■ Graphs Accordingl
- Page 602 and 603:
588 CHAPTER 4 ■ Graphs Kosaraju
- Page 604 and 605:
590 CHAPTER 4 ■ Graphs A larger e
- Page 606 and 607:
592 CHAPTER 4 ■ Graphs understand
- Page 608 and 609:
594 CHAPTER 4 ■ Graphs Summary In
- Page 610 and 611:
596 CHAPTER 4 ■ Graphs EXERCISES
- Page 612 and 613:
598 CHAPTER 4 ■ Graphs CREATIVE P
- Page 614 and 615:
600 CHAPTER 4 ■ Graphs CREATIVE P
- Page 616 and 617:
602 CHAPTER 4 ■ Graphs EXPERIMENT
- Page 618 and 619:
4.3 MINIMUM SPANNING TREES V tinyEW
- Page 620 and 621:
606 CHAPTER 4 ■ Graphs Underlying
- Page 622 and 623:
608 CHAPTER 4 ■ Graphs Edge-weigh
- Page 624 and 625:
610 CHAPTER 4 ■ Graphs We ighte d
- Page 626 and 627:
612 CHAPTER 4 ■ Graphs Compar ing
- Page 628 and 629:
614 CHAPTER 4 ■ Graphs Test data.
- Page 630 and 631:
616 CHAPTER 4 ■ Graphs ineligible
- Page 632 and 633:
618 CHAPTER 4 ■ Graphs After havi
- Page 634 and 635:
620 CHAPTER 4 ■ Graphs E ager ver
- Page 636 and 637:
622 CHAPTER 4 ■ Graphs ALGORITHM
- Page 638 and 639:
624 CHAPTER 4 ■ Graphs next MST e
- Page 640 and 641:
626 CHAPTER 4 ■ Graphs 20% The fi
- Page 642 and 643:
628 CHAPTER 4 ■ Graphs Perspectiv
- Page 644 and 645:
630 CHAPTER 4 ■ Graphs Q&A Q. Do
- Page 646 and 647:
632 CHAPTER 4 ■ Graphs EXERCISES
- Page 648 and 649:
634 CHAPTER 4 ■ Graphs CREATIVE P
- Page 650 and 651:
636 CHAPTER 4 ■ Graphs EXPERIMENT
- Page 652 and 653:
4.4 SHORTEST PATHS edge-weighted di
- Page 654 and 655:
640 CHAPTER 4 ■ Graphs 0 6->0 1 n
- Page 656 and 657:
642 CHAPTER 4 ■ Graphs D i rec te
- Page 658 and 659:
644 CHAPTER 4 ■ Graphs V tinyEWD.
- Page 660 and 661:
646 CHAPTER 4 ■ Graphs Data struc
- Page 662 and 663:
648 CHAPTER 4 ■ Graphs Ve r tex r
- Page 664 and 665:
650 CHAPTER 4 ■ Graphs Theoretica
- Page 666 and 667:
652 CHAPTER 4 ■ Graphs Dijkst r a
- Page 668 and 669:
654 CHAPTER 4 ■ Graphs The implem
- Page 670 and 671:
656 CHAPTER 4 ■ Graphs Source-sin
- Page 672 and 673:
658 CHAPTER 4 ■ Graphs Acyclic ed
- Page 674 and 675:
660 CHAPTER 4 ■ Graphs ALGORITHM
- Page 676 and 677:
662 CHAPTER 4 ■ Graphs The figure
- Page 678 and 679:
664 CHAPTER 4 ■ Graphs job start
- Page 680 and 681:
666 CHAPTER 4 ■ Graphs original j
- Page 682 and 683:
668 CHAPTER 4 ■ Graphs V tinyEWDn
- Page 684 and 685:
670 CHAPTER 4 ■ Graphs Strawman I
- Page 686 and 687:
672 CHAPTER 4 ■ Graphs Queue-base
- Page 688 and 689:
674 CHAPTER 4 ■ Graphs ALGORITHM
- Page 690 and 691:
676 CHAPTER 4 ■ Graphs tinyEWDn.t
- Page 692 and 693:
678 CHAPTER 4 ■ Graphs The exampl
- Page 694 and 695:
680 CHAPTER 4 ■ Graphs A r bitra
- Page 696 and 697:
682 CHAPTER 4 ■ Graphs Perspectiv
- Page 698 and 699:
684 CHAPTER 4 ■ Graphs Q&A Q. Why
- Page 700 and 701:
686 CHAPTER 4 ■ Graphs EXERCISES
- Page 702 and 703:
688 CHAPTER 4 ■ Graphs CREATIVE P
- Page 704 and 705:
690 CHAPTER 4 ■ Graphs CREATIVE P
- Page 706 and 707:
692 CHAPTER 4 ■ Graphs EXPERIMENT
- Page 708 and 709:
FIVE St r i ngs 5.1 String Sorts .
- Page 710 and 711:
696 CHAPTER 5 ■ Strings The plan
- Page 712 and 713:
698 CHAPTER 5 ■ Strings We primar
- Page 714 and 715:
700 CHAPTER 5 ■ Strings access. W
- Page 716 and 717:
5.1 STRING SORTS For many sorting a
- Page 718 and 719:
704 CHAPTER 5 ■ Strings i 0 1 2 3
- Page 720 and 721:
706 CHAPTER 5 ■ Strings LSD st r
- Page 722 and 723:
708 CHAPTER 5 ■ Strings J 6 A
- Page 724 and 725:
710 CHAPTER 5 ■ Strings J 6 A
- Page 726 and 727:
712 CHAPTER 5 ■ Strings ALGORITHM
- Page 728 and 729:
714 CHAPTER 5 ■ Strings input she
- Page 730 and 731:
716 CHAPTER 5 ■ Strings Extra spa
- Page 732 and 733:
718 CHAPTER 5 ■ Strings When N is
- Page 734 and 735:
720 CHAPTER 5 ■ Strings ALGORITHM
- Page 736 and 737:
722 CHAPTER 5 ■ Strings Randomiza
- Page 738 and 739:
724 CHAPTER 5 ■ Strings Which str
- Page 740 and 741:
726 CHAPTER 5 ■ Strings EXERCISES
- Page 742 and 743:
728 CHAPTER 5 ■ Strings EXPERIMEN
- Page 744 and 745:
5.2 TRIES As with sorting, we can t
- Page 746 and 747:
732 CHAPTER 5 ■ Strings Tr ies In
- Page 748 and 749:
734 CHAPTER 5 ■ Strings In s e r
- Page 750 and 751:
736 CHAPTER 5 ■ Strings Keys in t
- Page 752 and 753:
738 CHAPTER 5 ■ Strings Col l e c
- Page 754 and 755:
740 CHAPTER 5 ■ Strings "she" pub
- Page 756 and 757:
742 CHAPTER 5 ■ Strings The code
- Page 758 and 759:
744 CHAPTER 5 ■ Strings tions is
- Page 760 and 761:
746 CHAPTER 5 ■ Strings get("sea"
- Page 762 and 763:
748 CHAPTER 5 ■ Strings TST and i
- Page 764 and 765:
750 CHAPTER 5 ■ Strings and searc
- Page 766 and 767:
752 CHAPTER 5 ■ Strings Which str
- Page 768 and 769:
754 CHAPTER 5 ■ Strings EXERCISES
- Page 770 and 771:
756 CHAPTER 5 ■ Strings CREATIVE
- Page 772 and 773:
5.3 SUBSTRING SEARCH A fundamental
- Page 774 and 775:
760 CHAPTER 5 ■ Strings public st
- Page 776 and 777:
762 CHAPTER 5 ■ Strings text afte
- Page 778 and 779:
764 CHAPTER 5 ■ Strings DFA simul
- Page 780 and 781:
766 CHAPTER 5 ■ Strings 1 2 3 4 5
- Page 782 and 783:
768 CHAPTER 5 ■ Strings ALGORITHM
- Page 784 and 785:
770 CHAPTER 5 ■ Strings Boyer-Mo
- Page 786 and 787:
772 CHAPTER 5 ■ Strings ALGORITHM
- Page 788 and 789:
774 CHAPTER 5 ■ Strings Rabin-Kar
- Page 790 and 791:
776 CHAPTER 5 ■ Strings Implement
- Page 792 and 793:
778 CHAPTER 5 ■ Strings same valu
- Page 794 and 795:
780 CHAPTER 5 ■ Strings Q&A Q. Th
- Page 796 and 797:
782 CHAPTER 5 ■ Strings EXERCISES
- Page 798 and 799:
784 CHAPTER 5 ■ Strings CREATIVE
- Page 800 and 801:
786 CHAPTER 5 ■ Strings EXPERIMEN
- Page 802 and 803:
5.4 REGULAR EXPRESSIONS IN many app
- Page 804 and 805:
790 CHAPTER 5 ■ Strings Regular e
- Page 806 and 807:
792 CHAPTER 5 ■ Strings REs in ap
- Page 808 and 809:
794 CHAPTER 5 ■ Strings Nondeter
- Page 810 and 811:
796 CHAPTER 5 ■ Strings A A A 0 1
- Page 812 and 813:
798 CHAPTER 5 ■ Strings 0 1 2 3 4
- Page 814 and 815:
800 CHAPTER 5 ■ Strings Building
- Page 816 and 817:
802 CHAPTER 5 ■ Strings ALGORITHM
- Page 818 and 819:
804 CHAPTER 5 ■ Strings Propositi
- Page 820 and 821:
806 CHAPTER 5 ■ Strings EXERCISES
- Page 822 and 823:
808 CHAPTER 5 ■ Strings CREATIVE
- Page 824 and 825:
5.5 DATA COMPRESSION The world is a
- Page 826 and 827:
812 CHAPTER 5 ■ Strings Binary in
- Page 828 and 829:
814 CHAPTER 5 ■ Strings public cl
- Page 830 and 831:
816 CHAPTER 5 ■ Strings Limitatio
- Page 832 and 833:
818 CHAPTER 5 ■ Strings The pract
- Page 834 and 835:
820 CHAPTER 5 ■ Strings The same
- Page 836 and 837:
822 CHAPTER 5 ■ Strings Run-lengt
- Page 838 and 839:
824 CHAPTER 5 ■ Strings public st
- Page 840 and 841:
826 CHAPTER 5 ■ Strings Huffman c
- Page 842 and 843:
828 CHAPTER 5 ■ Strings private s
- Page 844 and 845:
830 CHAPTER 5 ■ Strings Trie cons
- Page 846 and 847:
832 CHAPTER 5 ■ Strings trie repr
- Page 848 and 849:
834 CHAPTER 5 ■ Strings leaves A
- Page 850 and 851:
836 CHAPTER 5 ■ Strings ALGORITHM
- Page 852 and 853:
838 CHAPTER 5 ■ Strings One reaso
- Page 854 and 855:
840 CHAPTER 5 ■ Strings input LZW
- Page 856 and 857:
842 CHAPTER 5 ■ Strings ALGORITHM
- Page 858 and 859:
844 CHAPTER 5 ■ Strings A LG O R
- Page 860 and 861:
846 CHAPTER 5 ■ Strings Q&A Q. Wh
- Page 862 and 863:
848 CHAPTER 5 ■ Strings EXERCISES
- Page 864 and 865:
850 CHAPTER 5 ■ Strings CREATIVE
- Page 866 and 867:
SIX Context
- Page 868 and 869:
854 CONTEXT several advanced contex
- Page 870 and 871:
856 CONTEXT advance time to t + dt
- Page 872 and 873:
858 CONTEXT resolution (at time t +
- Page 874 and 875:
860 CONTEXT Particles. Exercise 6.1
- Page 876 and 877:
862 CONTEXT A second twist in the i
- Page 878 and 879:
864 CONTEXT Event- b a s e d s i m
- Page 880 and 881:
866 CONTEXT B-t re es In Chapter 3,
- Page 882 and 883:
868 CONTEXT any. It is convenient t
- Page 884 and 885:
870 CONTEXT Representation. As just
- Page 886 and 887:
872 CONTEXT ALGORITHM 6.12 B-tree s
- Page 888 and 889:
874 CONTEXT this book) that the ave
- Page 890 and 891:
876 CONTEXT brute-force solution im
- Page 892 and 893:
878 CONTEXT accessed web page. Agai
- Page 894 and 895:
880 CONTEXT public class LRS { publ
- Page 896 and 897:
882 CONTEXT Implementation. The cod
- Page 898 and 899:
884 CONTEXT Improved implementation
- Page 900 and 901:
886 CONTEXT Ne twor k-flow algor it
- Page 902 and 903:
888 CONTEXT but our discussion appl
- Page 904 and 905:
890 CONTEXT public class FlowEdge F
- Page 906 and 907:
892 CONTEXT Ford-Fulkerson maxflow
- Page 908 and 909:
894 CONTEXT Proposition F. ( Maxflo
- Page 910 and 911:
896 CONTEXT Fl ow e d g e d a t a t
- Page 912 and 913:
898 CONTEXT ALGORITHM 6.14 Ford-Ful
- Page 914 and 915:
900 CONTEXT Shortest augmenting pat
- Page 916 and 917:
902 CONTEXT The practical applicati
- Page 918 and 919:
904 CONTEXT end up costing linearit
- Page 920 and 921:
906 CONTEXT Proposition J. The foll
- Page 922 and 923:
908 CONTEXT Proposition K. The foll
- Page 924 and 925:
910 CONTEXT Int r actabilit y The a
- Page 926 and 927:
912 CONTEXT The crux of the matter
- Page 928 and 929:
914 CONTEXT Easy search problems. T
- Page 930 and 931:
916 CONTEXT The main question. Nond
- Page 932 and 933:
918 CONTEXT Definition. A search pr
- Page 934 and 935:
920 CONTEXT Boolean satisfiability.
- Page 936 and 937:
922 CONTEXT EXERCISES on collision
- Page 938 and 939:
924 CONTEXT EXERCISES on B-Trees 6.
- Page 940 and 941:
926 CONTEXT EXERCISES on suffix arr
- Page 942 and 943:
928 CONTEXT EXERCISES on maxflow 6.
- Page 944 and 945:
930 CONTEXT EXERCISES on reductions
- Page 946 and 947:
Index
- Page 948 and 949:
934 INDEX cost model 182 divide-and
- Page 950 and 951:
936 INDEX Center of a graph 559 Cer
- Page 952 and 953:
938 INDEX adjacency-lists represent
- Page 954 and 955:
940 INDEX Huffman encoding 830 mini
- Page 956 and 957:
942 INDEX using objects 69 variable
- Page 958 and 959:
944 INDEX See Mincut problem Minota
- Page 960 and 961:
946 INDEX Cycle 547 Date 91, 103, 2
- Page 962 and 963:
948 INDEX defined 432 delete the ma
- Page 964 and 965:
950 INDEX Draw 82-83 In 41, 82-83 O
- Page 966 and 967:
952 INDEX odd cycle detection 562 p
- Page 968 and 969:
ALGORITHMS Fundamentals 1.1 Pushdow