TrustLogics ICO Whitepaper
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Page13<br />
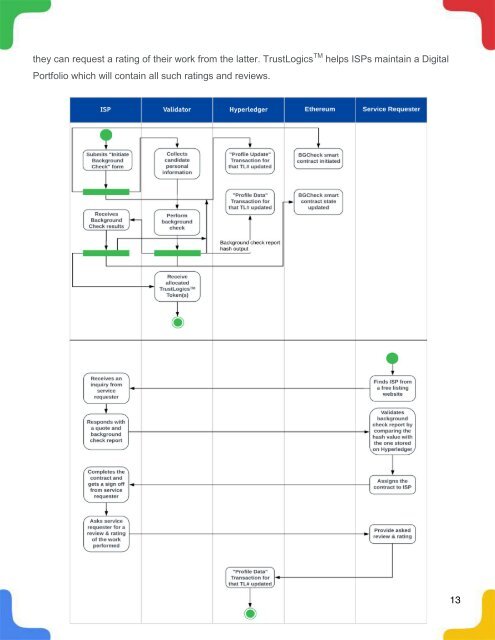
they can request a rating of their work from the latter. <strong>TrustLogics</strong> TM helps ISPs maintain a Digital<br />
Portfolio which will contain all such ratings and reviews.<br />
13