Cyber Defense eMagazine November Edition for 2021
Cyber Defense eMagazine November Edition for 2021 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, US Editor-in-Chief, Pieruligi Paganini, International Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES See you at RSA Conference 2022 - Our 10th Year Anniversary - Our 10th Year @RSAC #RSACONFERENCE #USA - Thank you so much!!! - Team CDMG
Cyber Defense eMagazine November Edition for 2021 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, US Editor-in-Chief, Pieruligi Paganini, International Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
See you at RSA Conference 2022 - Our 10th Year Anniversary - Our 10th Year @RSAC #RSACONFERENCE #USA - Thank you so much!!! - Team CDMG
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
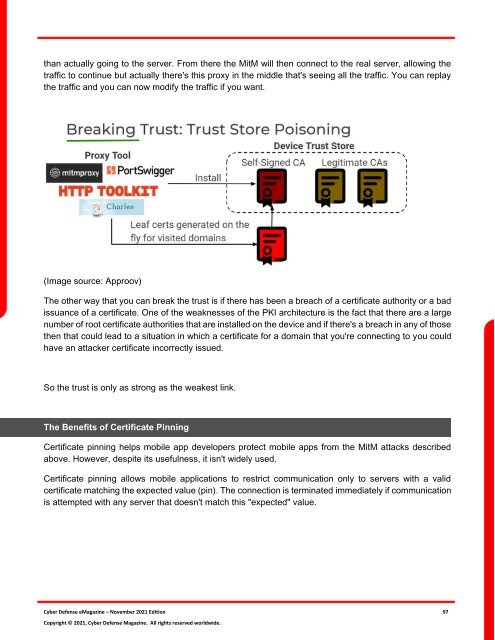
than actually going to the server. From there the MitM will then connect to the real server, allowing the<br />
traffic to continue but actually there's this proxy in the middle that's seeing all the traffic. You can replay<br />
the traffic and you can now modify the traffic if you want.<br />
(Image source: Approov)<br />
The other way that you can break the trust is if there has been a breach of a certificate authority or a bad<br />
issuance of a certificate. One of the weaknesses of the PKI architecture is the fact that there are a large<br />
number of root certificate authorities that are installed on the device and if there's a breach in any of those<br />
then that could lead to a situation in which a certificate <strong>for</strong> a domain that you're connecting to you could<br />
have an attacker certificate incorrectly issued.<br />
So the trust is only as strong as the weakest link.<br />
The Benefits of Certificate Pinning<br />
Certificate pinning helps mobile app developers protect mobile apps from the MitM attacks described<br />
above. However, despite its usefulness, it isn't widely used.<br />
Certificate pinning allows mobile applications to restrict communication only to servers with a valid<br />
certificate matching the expected value (pin). The connection is terminated immediately if communication<br />
is attempted with any server that doesn't match this "expected" value.<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>November</strong> <strong>2021</strong> <strong>Edition</strong> 97<br />
Copyright © <strong>2021</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.