TCP-PCP: A Transport Control Protocol Based on the Prediction of ...
TCP-PCP: A Transport Control Protocol Based on the Prediction of ...
TCP-PCP: A Transport Control Protocol Based on the Prediction of ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Recv( ACK[i] ):<br />
CP[i] → CP[i − 1];<br />
calculate CP[i];<br />
CP[i]-CP[i − 1] →△CP ;<br />
if newACK <strong>the</strong>n<br />
if ACK[i].CE=1<br />
ecn-acti<strong>on</strong>()<br />
SS() or CA()<br />
else<br />
SS() or CA() //Same as Newreno<br />
endif;<br />
else <strong>the</strong>n<br />
if △CP > 0<br />
Rate<str<strong>on</strong>g>C<strong>on</strong>trol</str<strong>on</strong>g>() //Same as Westwood<br />
Retransmit()<br />
else<br />
Retransmit()<br />
endif;<br />
Fig. 2: Pseudo code <strong>of</strong> <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>’s sender receiving procedure<br />
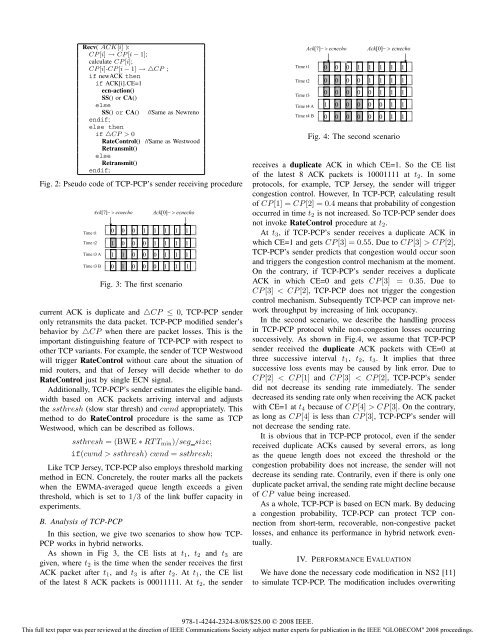
Time t1<br />
Time t2<br />
Ack[ 7]<br />
ecnecho Ack[ 0]<br />
ecnecho<br />
Time t3 A<br />
0 0 0 1 1 1 1 1<br />
1 0 0 0 1 1 1 1<br />
1 1 0 0 0 1 1 1<br />
Time t3 B 0 1 0 0 0 1 1 1<br />
Fig. 3: The first scenario<br />
current ACK is duplicate and △CP ≤ 0, <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> sender<br />
<strong>on</strong>ly retransmits <strong>the</strong> data packet. <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> modified sender’s<br />
behavior by △CP when <strong>the</strong>re are packet losses. This is <strong>the</strong><br />
important distinguishing feature <strong>of</strong> <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> with respect to<br />
o<strong>the</strong>r <str<strong>on</strong>g>TCP</str<strong>on</strong>g> variants. For example, <strong>the</strong> sender <strong>of</strong> <str<strong>on</strong>g>TCP</str<strong>on</strong>g> Westwood<br />
will trigger Rate<str<strong>on</strong>g>C<strong>on</strong>trol</str<strong>on</strong>g> without care about <strong>the</strong> situati<strong>on</strong> <strong>of</strong><br />
mid routers, and that <strong>of</strong> Jersey will decide whe<strong>the</strong>r to do<br />
Rate<str<strong>on</strong>g>C<strong>on</strong>trol</str<strong>on</strong>g> just by single ECN signal.<br />
Additi<strong>on</strong>ally, <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>’s sender estimates <strong>the</strong> eligible bandwidth<br />
based <strong>on</strong> ACK packets arriving interval and adjusts<br />
<strong>the</strong> ssthresh (slow star thresh) and cwnd appropriately. This<br />
method to do Rate<str<strong>on</strong>g>C<strong>on</strong>trol</str<strong>on</strong>g> procedure is <strong>the</strong> same as <str<strong>on</strong>g>TCP</str<strong>on</strong>g><br />
Westwood, which can be described as follows.<br />
ssthresh =(BWE∗RT Tmin)/seg size;<br />
if(cwnd > ssthresh) cwnd = ssthresh;<br />
Like <str<strong>on</strong>g>TCP</str<strong>on</strong>g> Jersey, <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> also employs threshold marking<br />
method in ECN. C<strong>on</strong>cretely, <strong>the</strong> router marks all <strong>the</strong> packets<br />
when <strong>the</strong> EWMA-averaged queue length exceeds a given<br />
threshold, which is set to 1/3 <strong>of</strong> <strong>the</strong> link buffer capacity in<br />
experiments.<br />
B. Analysis <strong>of</strong> <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g><br />
In this secti<strong>on</strong>, we give two scenarios to show how <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<br />
<str<strong>on</strong>g>PCP</str<strong>on</strong>g> works in hybrid networks.<br />
As shown in Fig 3, <strong>the</strong> CE lists at t1, t2 and t3 are<br />
given, where t2 is <strong>the</strong> time when <strong>the</strong> sender receives <strong>the</strong> first<br />
ACK packet after t1, and t3 is after t2. Att1, <strong>the</strong> CE list<br />
<strong>of</strong> <strong>the</strong> latest 8 ACK packets is 00011111. At t2, <strong>the</strong> sender<br />
Time t1<br />
Time t2<br />
Time t3<br />
Time t4 A<br />
Time t4 B<br />
Ack[ 7]<br />
ecnecho Ack[ 0]<br />
ecnecho<br />
0<br />
0<br />
0 1<br />
1 1<br />
0 0 0 0 1 1 1 1<br />
0 0 0 0 0 1 1 1<br />
1 0 0 0 0 0 1 1<br />
0 0 0 0 0 0 1 1<br />
Fig. 4: The sec<strong>on</strong>d scenario<br />
receives a duplicate ACK in which CE=1. So <strong>the</strong> CE list<br />
<strong>of</strong> <strong>the</strong> latest 8 ACK packets is 10001111 at t2. In some<br />
protocols, for example, <str<strong>on</strong>g>TCP</str<strong>on</strong>g> Jersey, <strong>the</strong> sender will trigger<br />
c<strong>on</strong>gesti<strong>on</strong> c<strong>on</strong>trol. However, In <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>, calculating result<br />
<strong>of</strong> CP[1] = CP[2] = 0.4 means that probability <strong>of</strong> c<strong>on</strong>gesti<strong>on</strong><br />
occurred in time t2 is not increased. So <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> sender does<br />
not invoke Rate<str<strong>on</strong>g>C<strong>on</strong>trol</str<strong>on</strong>g> procedure at t2.<br />
At t3, if <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>’s sender receives a duplicate ACK in<br />
which CE=1 and gets CP[3] = 0.55. DuetoCP[3] >CP[2],<br />
<str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>’s sender predicts that c<strong>on</strong>gesti<strong>on</strong> would occur so<strong>on</strong><br />
and triggers <strong>the</strong> c<strong>on</strong>gesti<strong>on</strong> c<strong>on</strong>trol mechanism at <strong>the</strong> moment.<br />
On <strong>the</strong> c<strong>on</strong>trary, if <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>’s sender receives a duplicate<br />
ACK in which CE=0 and gets CP[3] = 0.35. Due to<br />
CP[3] CP[3]. On <strong>the</strong> c<strong>on</strong>trary,<br />
as l<strong>on</strong>g as CP[4] is less than CP[3], <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>’s sender will<br />
not decrease <strong>the</strong> sending rate.<br />
It is obvious that in <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> protocol, even if <strong>the</strong> sender<br />
received duplicate ACKs caused by several errors, as l<strong>on</strong>g<br />
as <strong>the</strong> queue length does not exceed <strong>the</strong> threshold or <strong>the</strong><br />
c<strong>on</strong>gesti<strong>on</strong> probability does not increase, <strong>the</strong> sender will not<br />
decrease its sending rate. C<strong>on</strong>trarily, even if <strong>the</strong>re is <strong>on</strong>ly <strong>on</strong>e<br />
duplicate packet arrival, <strong>the</strong> sending rate might decline because<br />
<strong>of</strong> CP value being increased.<br />
As a whole, <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> is based <strong>on</strong> ECN mark. By deducing<br />
a c<strong>on</strong>gesti<strong>on</strong> probability, <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g> can protect <str<strong>on</strong>g>TCP</str<strong>on</strong>g> c<strong>on</strong>necti<strong>on</strong><br />
from short-term, recoverable, n<strong>on</strong>-c<strong>on</strong>gestive packet<br />
losses, and enhance its performance in hybrid network eventually.<br />
IV. PERFORMANCE EVALUATION<br />
We have d<strong>on</strong>e <strong>the</strong> necessary code modificati<strong>on</strong> in NS2 [11]<br />
to simulate <str<strong>on</strong>g>TCP</str<strong>on</strong>g>-<str<strong>on</strong>g>PCP</str<strong>on</strong>g>. The modificati<strong>on</strong> includes overwriting<br />
978-1-4244-2324-8/08/$25.00 © 2008 IEEE.<br />
This full text paper was peer reviewed at <strong>the</strong> directi<strong>on</strong> <strong>of</strong> IEEE Communicati<strong>on</strong>s Society subject matter experts for publicati<strong>on</strong> in <strong>the</strong> IEEE "GLOBECOM" 2008 proceedings.<br />
1<br />
1