JAM: Java agents for Meta-Learning over Distributed Databases
JAM: Java agents for Meta-Learning over Distributed Databases
JAM: Java agents for Meta-Learning over Distributed Databases
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
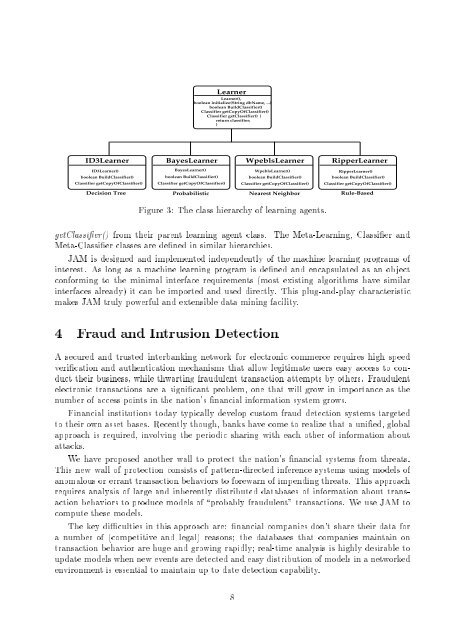
Learner<br />
getClassier()fromtheirparentlearningagentclass.The<strong>Meta</strong>-<strong>Learning</strong>,Classierand<br />
Learner(),<br />
boolean initialize(String dbName, ...)<br />
<strong>Meta</strong>-Classierclassesaredenedinsimilarhierarchies. Figure3:Theclasshierarchyoflearning<strong>agents</strong>.<br />
boolean BuildClassifier()<br />
Classifier getCopyOfClassifier()<br />
Classifier getClassifier() {<br />
return classifier;<br />
}<br />
makes<strong>JAM</strong>trulypowerfulandextensibledataminingfacility. interfacesalready)itcanbeimportedanduseddirectly.Thisplug-and-playcharacteristic interest.Aslongasamachinelearningprogramisdenedandencapsulatedasanobject con<strong>for</strong>mingtotheminimalinterfacerequirements(mostexistingalgorithmshavesimilar <strong>JAM</strong>isdesignedandimplementedindependentlyofthemachinelearningprogramsof<br />
ID3Learner BayesLearner WpeblsLearner RipperLearner<br />
ID3Learner()<br />
BayesLearner()<br />
WpeblsLearner()<br />
RipperLearner()<br />
boolean BuildClassifier()<br />
boolean BuildClassifier()<br />
boolean BuildClassifier()<br />
boolean BuildClassifier()<br />
Classifier getCopyOfClassifier() Classifier getCopyOfClassifier() Classifier getCopyOfClassifier() Classifier getCopyOfClassifier()<br />
4FraudandIntrusionDetection<br />
Decision Tree<br />
Probabilistic<br />
Nearest Neighbor<br />
Rule-Based<br />
Asecuredandtrustedinterbankingnetwork<strong>for</strong>electroniccommercerequireshighspeed<br />
approachisrequired,involvingtheperiodicsharingwitheachotherofin<strong>for</strong>mationabout electronictransactionsareasignicantproblem,onethatwillgrowinimportanceasthe numberofaccesspointsinthenation'snancialin<strong>for</strong>mationsystemgrows. totheirownassetbases.Recentlythough,bankshavecometorealizethataunied,global ducttheirbusiness,whilethwartingfraudulenttransactionattemptsbyothers.Fraudulentvericationandauthenticationmechanismsthatallowlegitimateuserseasyaccesstocon- attacks. Financialinstitutionstodaytypicallydevelopcustomfrauddetectionsystemstargeted<br />
computethesemodels. actionbehaviorstoproducemodelsof\probablyfraudulent"transactions.Weuse<strong>JAM</strong>to anomalousorerranttransactionbehaviorsto<strong>for</strong>ewarnofimpendingthreats.Thisapproach requiresanalysisoflargeandinherentlydistributeddatabasesofin<strong>for</strong>mationabouttrans- Thisnewwallofprotectionconsistsofpattern-directedinferencesystemsusingmodelsof Thekeydicultiesinthisapproachare:nancialcompaniesdon'tsharetheirdata<strong>for</strong> Wehaveproposedanotherwalltoprotectthenation'snancialsystemsfromthreats.<br />
transactionbehaviorarehugeandgrowingrapidly;real-timeanalysisishighlydesirableto anumberof(competitiveandlegal)reasons;thedatabasesthatcompaniesmaintainon updatemodelswhenneweventsaredetectedandeasydistributionofmodelsinanetworked<br />
environmentisessentialtomaintainuptodatedetectioncapability.<br />
8