- Page 1 and 2: Cracking Passwords in Forensic Inve
- Page 3 and 4: iii Acknowledgements This thesis wa
- Page 5 and 6: v Abstract Digital Forensic Investi
- Page 7 and 8: vii Table of Contents Declaration .
- Page 9 and 10: ix Chapter 4 - Research Findings 4.
- Page 11 and 12: xi List of Tables Table 2.1: The Mo
- Page 13 and 14: xiii List of Abbreviations AMD Adva
- Page 15 and 16: 1.1 PROBLEMS FOR DIGITAL FORENSIC I
- Page 17 and 18: approach improves the password crac
- Page 19 and 20: technologies, there exist challenge
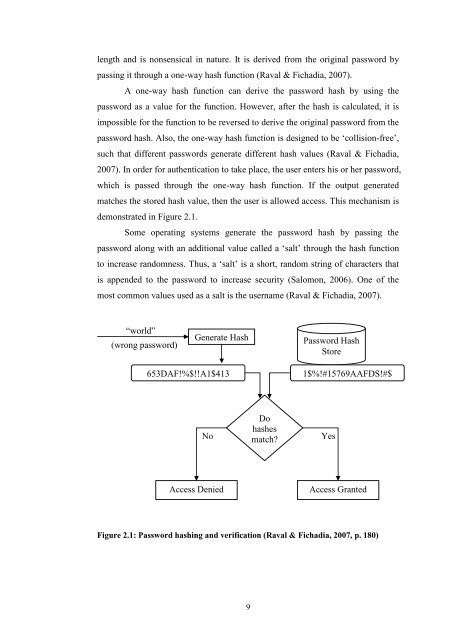
- Page 21: 2.1 PASSWORDS AND PASSWORD RECOVERY
- Page 25 and 26: encrypting the information within s
- Page 27 and 28: iii) If possible, create a custom d
- Page 29 and 30: Since all possible permutations and
- Page 31 and 32: L0phtCrack 6 supports the retrieval
- Page 33 and 34: i) Decryption attack: As discussed
- Page 35 and 36: Full cost refers to the total amoun
- Page 37 and 38: As shown in Table 2.3, a password w
- Page 39 and 40: 5) Weir, Aggarwal, Medeiros, and Gl
- Page 41 and 42: the speed of cracking and the attac
- Page 43 and 44: is inevitable) but rather the optim
- Page 45 and 46: Klein (1990) addressed the most com
- Page 47 and 48: character hashing. Thus, for passwo
- Page 49 and 50: experiments were conducted by gener
- Page 51 and 52: obtained via phishing attacks on th
- Page 53 and 54: Bengtsson (2007) outlined a literat
- Page 55 and 56: applications whose passwords need t
- Page 57 and 58: equired for computing and testing.
- Page 59 and 60: 3.2.3 The Research Questions and Hy
- Page 61 and 62: main experiment, which is the next
- Page 63 and 64: 12,500 x 8 = 100,000 passwords/seco
- Page 65 and 66: 3.3.5 Data Map Figure 3.2: Research
- Page 67 and 68: 4.0 INTRODUCTION Chapter 4 Research
- Page 69 and 70: 4.1.2 Time Budgeting The time budge
- Page 71 and 72: Another computer with the same conf
- Page 73 and 74:
minutes, and 24.8 days respectively
- Page 75 and 76:
vishal@vishal-desktop:~$ sudo addus
- Page 77 and 78:
Table 4.4: Monitoring/action-perfor
- Page 79 and 80:
4.3 ANALYSIS OF DATA The experiment
- Page 81 and 82:
Table 4.6: First 10 accounts’ pas
- Page 83 and 84:
DD:HH:MM:SS format, similar to the
- Page 85 and 86:
4.4 PRESENTATION OF DATA FINDING Af
- Page 87 and 88:
Figure 4.8 shows the time taken for
- Page 89 and 90:
Figure 4.11 displays the comparison
- Page 91 and 92:
5.0 INTRODUCTION Chapter 5 Research
- Page 93 and 94:
Thus, the simulation mirrored the f
- Page 95 and 96:
Table 5.1: Testing hypothesis H0 Hy
- Page 97 and 98:
Table 5.3: Testing hypothesis H2 Hy
- Page 99 and 100:
Q3: What are the guidelines for bes
- Page 101 and 102:
Since the passwords were arranged i
- Page 103 and 104:
Analysis (see Section 3.2.3). All f
- Page 105 and 106:
information for forensic investigat
- Page 107 and 108:
5.3.1.2 Second Step - Find Password
- Page 109 and 110:
Therefore, T (in seconds) = 12,500,
- Page 111 and 112:
6.0 RESEARCH SUMMARY Chapter 6 Conc
- Page 113 and 114:
udgets, the passwords were added to
- Page 115 and 116:
SECONDARY RESEARCH QUESTION 3: What
- Page 117 and 118:
overcome the security barriers of p
- Page 119 and 120:
Clayton, R., & Bond, M. (2003). Exp
- Page 121 and 122:
Openwall Project. (2010). John the
- Page 123 and 124:
APPENDIX 1: Time Budget Calculation
- Page 125 and 126:
51 Bas -2-38 TOTAL TIME REQUIRED FO
- Page 127 and 128:
96 Bas -2-27 97 Bas -2-28 98 Bas -2
- Page 129 and 130:
140 Adv -1-26 141 Bas -3-07 142 Adv
- Page 131 and 132:
182 Adv -1-21 183 Adv -1-22 Diction
- Page 133 and 134:
main12:$1$CSD0Tppt$0gO4c883evmn9sQR
- Page 135 and 136:
main41.txt: main41:$1$B43.jKTn$5EPi
- Page 137 and 138:
main70.txt: main70:$1$7kHK0PnH$yJ5x
- Page 139 and 140:
main99:$1$UQiTB..u$SJUkwarkM1kzvnvt
- Page 141 and 142:
main128.txt: main128:$1$n7OEbAyB$d6
- Page 143 and 144:
main157.txt: main157:$1$VRmaYxPu$Iy
- Page 145 and 146:
main186:$1$HFNaeUkb$t1lZ5QcrH9iy8G/
- Page 147 and 148:
SHA 1: a168282ad70a94fbb8d5917f3505
- Page 149 and 150:
C:\Main Test\MainTest-passwdFiles\B
- Page 151 and 152:
Job Started: 7/13/10 8:49:24 File M
- Page 153 and 154:
File Modified: 7/13/10 6:58:08 SHA
- Page 155 and 156:
File Version: Unknown Job Started:
- Page 157 and 158:
SHA 1: b95b12e95c70b66df01af148502e
- Page 159 and 160:
File Size: 60 File Version: Unknown
- Page 161 and 162:
Job Status: Finished on 7/13/10 8:5
- Page 163 and 164:
Identified Type: *nix passwd File S
- Page 165 and 166:
Password Type: Password Where Found
- Page 167 and 168:
Job Status: Finished on 7/13/10 10:
- Page 169 and 170:
File Size: 60 File Version: Unknown
- Page 171 and 172:
MD5: df7c66c8b6b8528176d42314926021
- Page 173 and 174:
Result: trapezoidal@ Description: U
- Page 175 and 176:
Where Found: (ADV-1-20) Dictionary
- Page 177 and 178:
Password Type: Password Where Found
- Page 179 and 180:
Where Found: (BAS-3-04) Dictionary
- Page 181 and 182:
Commonly Registered Type: crypt use
- Page 183 and 184:
File Size: 61 File Version: Unknown
- Page 185 and 186:
Commonly Registered Type: crypt use
- Page 187 and 188:
Where Found: --- C:\Main Test\MainT
- Page 189 and 190:
MD5: 17632fca93fa27bb8d0a89c80a2ba9
- Page 191 and 192:
Description: Unknown Password Type:
- Page 193 and 194:
File Modified: 7/13/10 7:44:34 SHA
- Page 195 and 196:
File Version: Unknown Job Started:
- Page 197 and 198:
Commonly Registered Type: crypt use
- Page 199 and 200:
File Modified: 7/13/10 7:55:34 SHA
- Page 201 and 202:
APPENDIX 4: Time Analysis for all B
- Page 203 and 204:
main60 main61 main62 main63 main64
- Page 205 and 206:
main127 main128 main129 main130 mai
- Page 207:
main192 main193 main194 main195 mai