You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Level of privacy (R)<br />
1<br />
0.9<br />
0.8<br />
0.7<br />
0.6<br />
0.5<br />
0.4<br />
0.3<br />
0.2<br />
0.1<br />
Simulation result<br />
Formal result<br />
0<br />
0 50 100 150 200<br />
Number of compromised members (c)<br />
Level of privacy(R)<br />
1<br />
0.9<br />
0.8<br />
0.7<br />
0.6<br />
0.5<br />
0.4<br />
0.3<br />
0.2<br />
0.1<br />
2.8. Related work<br />
Tree based authentication<br />
Group based authentication<br />
0<br />
0 50 100 150 200<br />
Number of compromised members (c)<br />
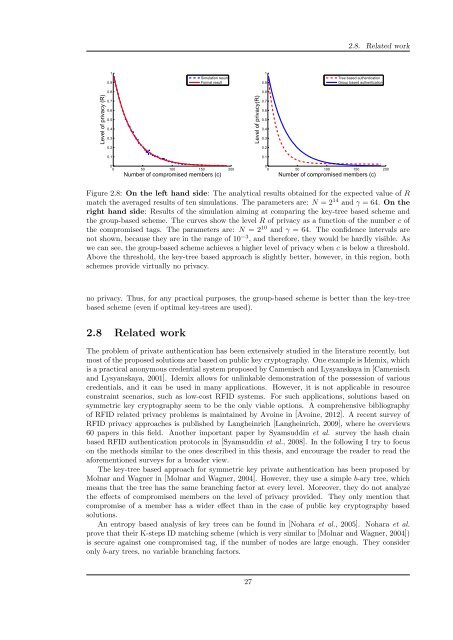
Figure 2.8: On the left hand side: The analytical results obtained for the expected value of R<br />
match the averaged results of ten simulations. The parameters are: N = 2 14 and γ = 64. On the<br />
right hand side: Results of the simulation aiming at comparing the key-tree based scheme and<br />
the group-based scheme. The curves show the level R of privacy as a function of the number c of<br />
the compromised tags. The parameters are: N = 2 10 and γ = 64. The confidence intervals are<br />
not shown, because they are in the range of 10 −3 , and therefore, they would be hardly visible. As<br />
we can see, the group-based scheme achieves a higher level of privacy when c is below a threshold.<br />
Above the threshold, the key-tree based approach is slightly better, however, in this region, both<br />
schemes provide virtually no privacy.<br />
no privacy. Thus, for any practical purposes, the group-based scheme is better than the key-tree<br />
based scheme (even if optimal key-trees are used).<br />
2.8 Related work<br />
The problem of private authentication has been extensively studied in the literature recently, but<br />
most of the proposed solutions are based on public key cryptography. One example is Idemix, which<br />
is a practical anonymous credential system proposed by Camenisch and Lysyanskaya in [Camenisch<br />
and Lysyanskaya, 2001]. Idemix allows for unlinkable demonstration of the possession of various<br />
credentials, and it can be used in many applications. However, it is not applicable in resource<br />
constraint scenarios, such as low-cost RFID systems. For such applications, solutions based on<br />
symmetric key cryptography seem to be the only viable options. A comprehensive bibliography<br />
of RFID related privacy problems is maintained by Avoine in [Avoine, 2012]. A recent survey of<br />
RFID privacy approaches is published by Langheinrich [Langheinrich, 2009], where he overviews<br />
60 papers in this field. Another important paper by Syamsuddin et al. survey the hash chain<br />
based RFID authentication protocols in [Syamsuddin et al., 2008]. In the following I try to focus<br />
on the methods similar to the ones described in this thesis, and encourage the reader to read the<br />
aforementioned surveys for a broader view.<br />
The key-tree based approach for symmetric key private authentication has been proposed by<br />
Molnar and Wagner in [Molnar and Wagner, 2004]. However, they use a simple b-ary tree, which<br />
means that the tree has the same branching factor at every level. Moreover, they do not analyze<br />
the effects of compromised members on the level of privacy provided. They only mention that<br />
compromise of a member has a wider effect than in the case of public key cryptography based<br />
solutions.<br />
An entropy based analysis of key trees can be found in [Nohara et al., 2005]. Nohara et al.<br />
prove that their K-steps ID matching scheme (which is very similar to [Molnar and Wagner, 2004])<br />
is secure against one compromised tag, if the number of nodes are large enough. They consider<br />
only b-ary trees, no variable branching factors.<br />
27