JSR-000058 Java TM 2 Platform, Enterprise Edition 1.3 Specification
JSR-000058 Java TM 2 Platform, Enterprise Edition 1.3 Specification
JSR-000058 Java TM 2 Platform, Enterprise Edition 1.3 Specification
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
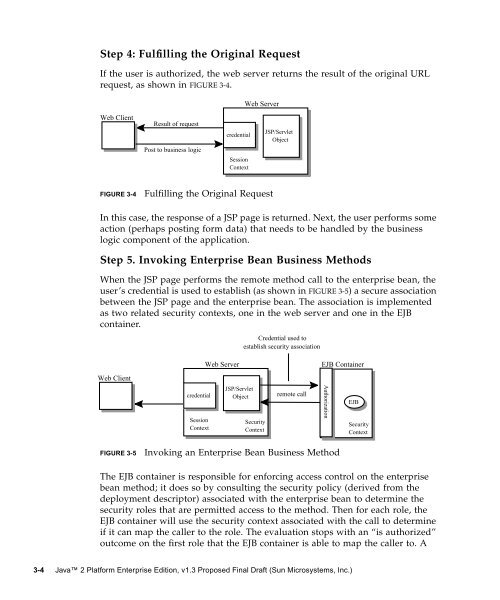
Step 4: Fulfilling the Original Request<br />
If the user is authorized, the web server returns the result of the original URL<br />
request, as shown in FIGURE 3-4.<br />
Web Client<br />
FIGURE 3-4 Fulfilling the Original Request<br />
In this case, the response of a JSP page is returned. Next, the user performs some<br />
action (perhaps posting form data) that needs to be handled by the business<br />
logic component of the application.<br />
Step 5. Invoking <strong>Enterprise</strong> Bean Business Methods<br />
When the JSP page performs the remote method call to the enterprise bean, the<br />
user’s credential is used to establish (as shown in FIGURE 3-5) a secure association<br />
between the JSP page and the enterprise bean. The association is implemented<br />
as two related security contexts, one in the web server and one in the EJB<br />
container.<br />
Web Client<br />
Result of request<br />
Post to business logic<br />
credential<br />
Session<br />
Context<br />
credential<br />
Session<br />
Context<br />
Web Server<br />
JSP/Servlet<br />
Object<br />
Web Server<br />
JSP/Servlet<br />
Object<br />
Credential used to<br />
establish security association<br />
Security<br />
Context<br />
remote call<br />
FIGURE 3-5 Invoking an <strong>Enterprise</strong> Bean Business Method<br />
EJB Container<br />
The EJB container is responsible for enforcing access control on the enterprise<br />
bean method; it does so by consulting the security policy (derived from the<br />
deployment descriptor) associated with the enterprise bean to determine the<br />
security roles that are permitted access to the method. Then for each role, the<br />
EJB container will use the security context associated with the call to determine<br />
if it can map the caller to the role. The evaluation stops with an “is authorized”<br />
outcome on the first role that the EJB container is able to map the caller to. A<br />
3-4 <strong>Java</strong> 2 <strong>Platform</strong> <strong>Enterprise</strong> <strong>Edition</strong>, v<strong>1.3</strong> Proposed Final Draft (Sun Microsystems, Inc.)<br />
Authorization<br />
EJB<br />
Security<br />
Context