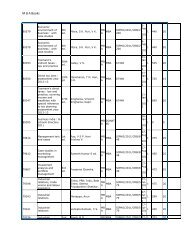
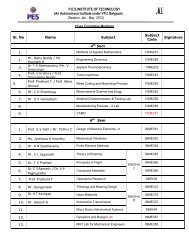
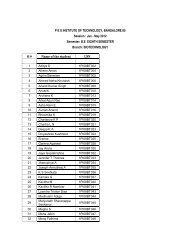
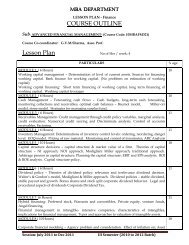
ERROR CONTROL AND CODING QUESTION BANK Subject Code ...
ERROR CONTROL AND CODING QUESTION BANK Subject Code ...
ERROR CONTROL AND CODING QUESTION BANK Subject Code ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>ERROR</strong> <strong>CONTROL</strong> <strong>AND</strong> <strong>CODING</strong><br />
<strong>QUESTION</strong> <strong>BANK</strong><br />
<strong>Subject</strong> <strong>Code</strong>: 10EC 039 Faculty: Kavitha Y.C.<br />
INTRODUCTION TO ALGEBRA<br />
1) Construct the group under modulo-6 addition.<br />
2) Construct the group under modulo-3 multiplication.<br />
3) Let m be the positive integer. If m is not a prime, prove that the set {1,2.,.,.,,m-1} is not a group under modulo-m<br />
multiplication.<br />
4) Construct the prime field GF(11) with modulo -11 addition and multiplication. Find all the primitive elements and<br />
determine the order of other elements.<br />
5) Let m be the positive integer. If m is not a prime, prove that the set {0,1,2.,.,.,,m-1} is not a field under modulo-m<br />
addition and multiplication.<br />
6) Prove that every finite field has a primitive element.<br />
7) Solve the following simultaneous equations of X,Y,Z and W with modulo-2 arithmetic :<br />
X+Y+W=1, X+W+Z=0, Y+Z+W=1,Y+Z+W=0<br />
8) Show thatX 5 +X 3 +1 is irreducible over(2)<br />
9) Find all irreducible polynomials of degree 5 over GF(2).<br />
10) Prove that GF(2 m )is a vector space over GF(2)<br />
11) Construct the vector space V5 of all 5-tuples over GF(2).Find the three dimensional subspace and determine its null<br />
space.<br />
12) Let v be a vector space over a field F.for any element c in F, prove that c 0=0.<br />
13) Let S1 S2 be the two subspaces of a vector v.show that intersection of S1 S2 is also a subspace in v.<br />
LINEAR BLOCK CODES<br />
14) Consider a systematic (8,4) code whose parity check equations are vo=u1+u2+u3, v1=uo+u1+u2,<br />
V2=uo+u1+u3, v3=uo+u2+u3 where uo,u1, u2 and u3 are message digits and vo,v1,v2,and v3 are parity check<br />
digits. Find the generator and parity check matrices for this code. show analytically that minimum distance of this<br />
code is 4.<br />
15) Construct the encoder for the code given in problem 14..<br />
16) Construct the syndrome circuit for the problem in 14.<br />
17) Let c be a linear code with both even weight and odd weight code vectors. Show that number of even weight code<br />
vectors is equal to odd weight code vectors.<br />
18) Prove that hamming distance satisfies triangular in equality that is let x,y and z three n tuples over GF(2), and show<br />
that d(x,y)+d(y,z)>=d(x,z).<br />
19) Prove that a linear code is capable of correcting λ or fewer errors and simultaneously detecting l (l>λ) or fewer errors<br />
if its minimum distance dmin>= λ+l+1.<br />
20) Determine the weight distribution of the (8,4) linear code given in problem 14 .let the transition probability of a BSC<br />
be p=10 -2 . Compute the probability of an undetected error of this code.<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 1/8
21) Because the (8,4) linear code given in problem 14 has minimum distance 4, it is capable of correcting all the single –<br />
error patterns and simultaneously detecting any combination of double errors. Construct a decoder for this code.<br />
The decoder must be capable of correcting any single error and detecting any double errors.<br />
22) The (8,4) linear code given in problem 14. Is capable of correcting 16 error patterns. Suppose that this code is used<br />
for a BSC. Devise a decoder for this code based on the table-lookup decoding scheme. The decoder is designed to<br />
correct the 16 most probable error patterns.<br />
CYCLIC CODE<br />
23) Consider (15,11) cyclic hamming code generated by g(x) =1+X+X 4<br />
a) Determine the parity polynomial h(x) of this code.<br />
b) Determine the generator polynomial of its dual code.<br />
c) Find the generator and parity matrices in systematic form for this code.<br />
24) Devise an encoder and a decoder for the (15,11) cyclic hamming code generated by g(X)= 1+X+X 4<br />
25) Show that g(X) =1+x 2 +X 4 +X 6 +X 7 +X 10 generates a (21,11) cyclic code. Devise a syndrome computation circuit for<br />
this code. Let r(X) =1+X 5 +X 17 be a received polynomial. Compute the syndrome of r(X).display the contents of the<br />
syndrome register after each digit of r has been shifted in to the syndrome computation circuit.<br />
26) Shorten this (15,11) cyclic hamming by deleting the seven leading high order message digits.the resultant code is<br />
an (8,4) shortened cyclic code. design a decoder for this code that eliminates the extra shifts of the syndrome<br />
register.<br />
27) Shorten the (31,26) cyclic hamming by deleting the 11 leading high order message digits. The resultant code is a<br />
(20,15) shortened cyclic code. devise a decoding circuit for this code that requires no extra shifts of the syndrome<br />
register.<br />
28) Suppose that the (15,10) cyclic hamming code of minimum distance 4 is used for error detection over a BSC with<br />
transition probability p=10 -2 .compute the probability of an undetected error ,pu(E), for this code.<br />
29) Devise a decoding circuit for the (7,3) hamming code generated by g(X)=(X+1)(X 3 +X+1).The decoding circuits<br />
corrects all the single error patterns and all the double adjacent error patterns.<br />
30) For a cyclic code, if an error pattern e(X) is detectable ,show that its ith cyclic shift e (i) (X) is also detectable.<br />
31) Let g(X) be the generator polynomial of an (n,k)cyclic code c. suppose c is interleaved to a depth of λ.prove that the<br />
interleaved code c λ is also cyclic and its generator polynomial is g(X λ ).<br />
32) Show that the probability of an undetected error for the distance -4 cyclic hamming codes is upper bounded by<br />
2 -(m+1).<br />
BINARY BCH CODES<br />
33) Determine the generator polynomials of all the primitive BCH codes of length 31.use the Galois field GF(2 5 )<br />
generated by p(X) =1+X 2 +X 5.<br />
34) Suppose that the double error correcting BCH code of length 31 constructed in problem 33 is used for error<br />
correction on a BSC. Decode the received polynomials r1(X)=X 7 +X 30 and r2(X)=1+X 17 +X 28 .<br />
35) Devise a chien’s searching circuit for the binary double error correcting (31,21)BCH code.<br />
36) Devise a syndrome computation circuit for the binary double error correcting (31,21) BCH code.<br />
37) Is there a binary t-error correcting BCH code of length 2 m +1 for m>=3 and t
MAJORITY- LOGIC DECODABLE <strong>AND</strong> FINITE GEOMETRY CODES<br />
39) Consider the (31,5) maximum –length code whose parity check polynomial is p(X)=1+X+X 2 +X 5 .Find all the<br />
polynomials orthogonal on the digit position X 30 .Devise both type-I and type –II majority –logic decoders for this<br />
code.<br />
40) Example 39 shows that the (15,7)BCH code is one step majority logic decodable and is capable of correcting any<br />
combination of two or fewer errors.show that the code is also capable of correcting some error patterns of three<br />
errors and some error patterns of four errors. List some of these error patterns.<br />
41) Show that the extended cyclic hamming code is invariant under the affine permutations.<br />
42) Show that the extended primitive BCH code is invariant under the affine permutations.<br />
43) Prove that if J parity check sums orthogonal on any digit position can be formed for a linear code(cyclic or<br />
noncyclic), the minimum distance of the code is at least J+1.<br />
44) Find the generator polynomial of the first order cyclic RM code of length 2 5 -1.describe how to decode this code.<br />
45) Find the generator polynomial of the third order cyclic RM code of length 2 6 -1.describe how to decode this code.<br />
BURST –<strong>ERROR</strong>- CORRECTING CODES<br />
46) Show that if an (n,k) cyclic code is designed to correct all burst errors of length l or less and simultaneously to detect<br />
all burst errors of length d>=l or less, the number of parity check digits of the code must be at least l+d.<br />
47) Devise an error trapping decoder for an l-burst error correcting cyclic code. The received polynomial is shifted in to<br />
the syndrome register from the right end. Describe the decoding operation of your decoder.<br />
48) Prove that the fire code generated by (20,4) is capable of correcting any error burst of length l or less.<br />
49) The polynomial p(X)=1+X+X 4 is a primitive polynomial over GF(2). Find the generator polynomial of a fire code<br />
that is capable of correcting any single error burst of length 4 or less .what is the length of this code? Devise a<br />
simple error trapping decoder for this code.<br />
50) Devise a high speed error trapping decoder for the fire code constructed in problem 49 .describe the decoding<br />
operation.<br />
********<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 3/8
MULTI MEDIA COMMUNICATION<br />
<strong>QUESTION</strong> <strong>BANK</strong><br />
<strong>Subject</strong> <strong>Code</strong>: 10EC052 Faculty: Mr. MJR<br />
Chapter: Multimedia Communication<br />
1) What is Multimedia?<br />
2) Differentiate between Multimedia and Hypermedia?<br />
3) What are the different types of communication networks?<br />
4) What is Dither matrix?<br />
5) Briefly explain network QOS parameters<br />
6) Briefly explain Application QOS parameters.<br />
Chapter: Information Representation<br />
7) Explain different types of multimedia information representation.<br />
8) Explain different multimedia applications<br />
9) Name lossless and lossy compression algorithms<br />
10) Explain Huffman coding with an example.<br />
11) Explain Dynamic Huffman coding.<br />
12) Explain LZW Compression.<br />
13) Explain Linear predictive coding<br />
14) Explain DPCM and ADPCM<br />
15) Explain the differences between uniform and non-uniform quantization.<br />
16) Explain H.261 encoding and decoding.<br />
17) What is motion estimation and motion compensation?<br />
18) Explain different types frames.<br />
19) What are the differences between I-Frame and P-Frames?<br />
20) What is the significance of D-Frame?<br />
21) Explain P1.323 compression technique?<br />
22) Explain MPEG1 encoding and decoding techniques.<br />
Chapter: Detailed Study of MPEG-4<br />
23) Explain MPEG4 encoding and decoding techniques<br />
24) Explain JPEG encoding and decoding techniques.<br />
25) Compare MPEG4 with MPEG1.<br />
26) Compare MPEG4 with MPEG2.<br />
27) What do you meant VOP?<br />
28) What are the salient features of JPEG 2000?<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 4/8
Chapter: Synchronization<br />
29) What is the notion of Synchronization?<br />
30) Explain SMIL.<br />
31) Explain different Multimedia Operating Systems.<br />
32) Explain Resource Management.<br />
33) Explain Process Management.<br />
Chapter: Multimedia Communication across Networks<br />
34) What is layered video coding?<br />
35) Explain Error resilient video coding technique?<br />
36) Explain RSVP protocol.<br />
37) Explain RTP protocol.<br />
38) Explain RTCP protocol.<br />
39) Explain DVMPP protocol.<br />
40) Explain the applications of Multimedia in mobile networks.<br />
41) Explain the applications of multimedia in broadcast networks.<br />
********<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 5/8
REAL TIME OPERATING SYSTEMS<br />
<strong>QUESTION</strong> <strong>BANK</strong><br />
<strong>Subject</strong> <strong>Code</strong>: 10EC126 Faculty: Ms. BVK<br />
Chapter 1: Introduction<br />
1. Define i) Real Time System ii) Organic System<br />
2. Compare soft, hard and firm real time systems, with an example for each<br />
3. Differentiate between asynchronous and synchronous events<br />
4. Describe the following addressing modes<br />
i) Direct<br />
ii) Immediate<br />
iii) Register direct<br />
iv) Register indirect<br />
5. Write a program to evaluate the function sum = (a+b) – (c*d), using one address instruction format<br />
6. Write a program that performs the calculation using zero address machine<br />
x 2 – xy + y 2<br />
Z =<br />
x 2 + y 2<br />
7. Write a program that performs the calculation using zero address machine<br />
– b + √b2 – 4*a*c<br />
root =<br />
2*a<br />
8. Write short notes on the following:<br />
i) Pipelining<br />
ii) Coprocessors<br />
iii) DMA Controller<br />
iv) Programmed I/O and Interrupt I/O<br />
v) Interrupt controller<br />
vi) Watchdog timer<br />
Chapter 2: Device drivers<br />
9. Explain the steps involved in writing a device driver<br />
10. Describe a device driver using interrupt service routine<br />
11. Define context switching, latency with respect to interrupts<br />
Chapter 3: Embedded systems<br />
12. Compare different processor architectures for real time embedded system design.<br />
13. Compare RISC and CISC architectures<br />
14. Explain the architecture of ARM processors<br />
15. Explain the various features of Strong ARM Processor<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 6/8
16. Write short notes on the foll:<br />
i) Big Endean vs Little Endean<br />
ii) Exceptions<br />
Chapter 4: Real Time Operating System<br />
17. Explain various fundamental requirements of RTOS<br />
18. Explain Kernel hierarchy and different types of Kernel<br />
19. A simple process consists of 3 states, at the end of each state a flag is set and the process is terminated. Upon<br />
termination the process resumes where it left off. Write the pseudo code.<br />
20. Explain polled loop system with an example. What are its merits & demerits<br />
21. Explain the different approaches to CPU scheduling in real time OS. Comment upon the suitability of them for<br />
process, task and thread scheduling.<br />
22. With a state transition diagram and TCB, explain the functions of the various states.<br />
23. Describe round robin scheduling policy<br />
24. Explain preemptive scheduling<br />
25. Explain the cooperative round robin scheduling using a circular queue of ready tasks<br />
26. Write short notes on:<br />
i) Scheduling of periodic, sporadic and aperiodic tasks<br />
ii) Advanced scheduling algorithm<br />
27. Define tasks. What are different features of tasks<br />
28. What is the need for synchronization between process, tasks and threads? What are the various methods of<br />
synchronization?<br />
Chapter 5: Memory and File Management<br />
29. Define internal and external fragmentation. What is the use of a relocation register?<br />
30. Describe virtual memory concept and demand paged memory allocation technique<br />
31. Explain segmentation in memory management. What are the approaches followed by different processors for<br />
implementation of segmentation.<br />
32. Explain how pipelines, message queues and mail boxes can be used for inter-process synchronization.<br />
33. Compare message queue, mailbox & pipes<br />
34. Write short notes on the foll:<br />
i) Semaphores<br />
ii) Mail box<br />
iii) Massage Queues<br />
iv) Inter task comunication<br />
35. Explain cache organization. What are the different address translation mechanisms used for mapping<br />
addresses to cache locations.<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 7/8
Chapter 6: Case Study<br />
36. Explain the features of VxWorks.<br />
37. Compare the tools needed for verification, validation and testing of embedded systems.<br />
38. Explain the features of MUCOS<br />
39. Explain the features of Psos.<br />
Chapter 7: Development and Verification of Real Time Software<br />
40. Explain building of real time applications<br />
41. What are the approaches to double buffering in real time embedded systems?<br />
******<br />
P.E.S.I.T DEPT. OF TE III SEM M.Tech. (DECS) 8/8