Information Security in Korea IT839 strategy
Information Security in Korea IT839 strategy
Information Security in Korea IT839 strategy
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
25<br />
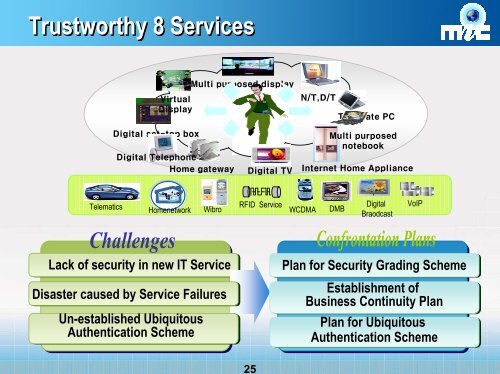
Trustworthy 8 Services<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
Telematics<br />
Homenetwork<br />
Wibro<br />
RFID Service WCDMA DMB<br />
Digital<br />
Braodcast<br />
VoIP<br />
Lack of security <strong>in</strong> new IT Service<br />
Disaster caused by Service Failures<br />
Un-established Ubiquitous<br />
Authentication Scheme<br />
Plan for <strong>Security</strong> Grad<strong>in</strong>g Scheme<br />
Establishment of<br />
Bus<strong>in</strong>ess Cont<strong>in</strong>uity Plan<br />
Plan for Ubiquitous<br />
Authentication Scheme