Understanding and Simulating the IEC 61850 Standard - CiteSeerX
Understanding and Simulating the IEC 61850 Standard - CiteSeerX
Understanding and Simulating the IEC 61850 Standard - CiteSeerX
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
SERVER<br />
LOGICAL-DEVICE<br />
LOGICAL-NODE<br />
DATA OBJECT<br />
LOGICAL-DEVICE<br />
LOGICAL-NODE<br />
DATA OBJECT<br />
DATA ATTRIBUTE<br />
LOGICAL-DEVICE<br />
LOGICAL-NODE<br />
DATA OBJECT<br />
DATA ATTRIBUTE<br />
...<br />
...<br />
...<br />
...<br />
Figure 3: Hierarchy of <strong>the</strong> <strong>IEC</strong> <strong>61850</strong> data model<br />
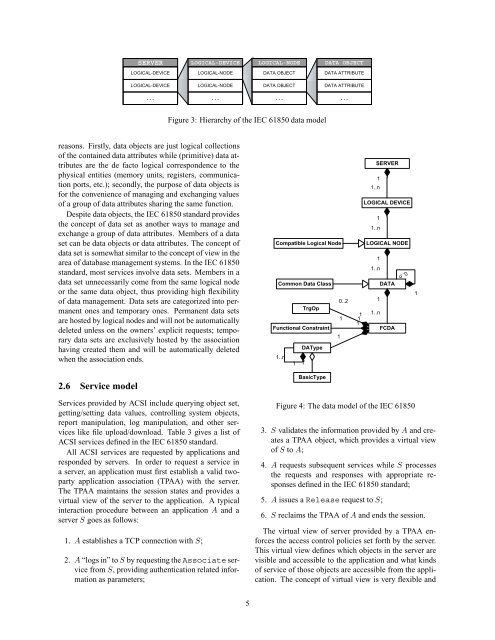
reasons. Firstly, data objects are just logical collections<br />
of <strong>the</strong> contained data attributes while (primitive) data attributes<br />
are <strong>the</strong> de facto logical correspondence to <strong>the</strong><br />
physical entities (memory units, registers, communication<br />
ports, etc.); secondly, <strong>the</strong> purpose of data objects is<br />
for <strong>the</strong> convenience of managing <strong>and</strong> exchanging values<br />
of a group of data attributes sharing <strong>the</strong> same function.<br />
Despite data objects, <strong>the</strong> <strong>IEC</strong> <strong>61850</strong> st<strong>and</strong>ard provides<br />
<strong>the</strong> concept of data set as ano<strong>the</strong>r ways to manage <strong>and</strong><br />
exchange a group of data attributes. Members of a data<br />
set can be data objects or data attributes. The concept of<br />
data set is somewhat similar to <strong>the</strong> concept of view in <strong>the</strong><br />
area of database management systems. In <strong>the</strong> <strong>IEC</strong> <strong>61850</strong><br />
st<strong>and</strong>ard, most services involve data sets. Members in a<br />
data set unnecessarily come from <strong>the</strong> same logical node<br />
or <strong>the</strong> same data object, thus providing high flexibility<br />
of data management. Data sets are categorized into permanent<br />
ones <strong>and</strong> temporary ones. Permanent data sets<br />
are hosted by logical nodes <strong>and</strong> will not be automatically<br />
deleted unless on <strong>the</strong> owners’ explicit requests; temporary<br />
data sets are exclusively hosted by <strong>the</strong> association<br />
having created <strong>the</strong>m <strong>and</strong> will be automatically deleted<br />
when <strong>the</strong> association ends.<br />
Compatible Logical Node<br />
Common Data Class<br />
0..2<br />
TrgOp<br />
1<br />
Functional Constraint<br />
1<br />
DAType<br />
1..n<br />
1 1*<br />
1<br />
1<br />
1<br />
SERVER<br />
1<br />
1..n<br />
LOGICAL DEVICE<br />
1<br />
1..n<br />
LOGICAL NODE<br />
1<br />
1..n<br />
DATA<br />
1<br />
1..n<br />
FCDA<br />
0..n<br />
1<br />
2.6 Service model<br />
BasicType<br />
Services provided by ACSI include querying object set,<br />
getting/setting data values, controlling system objects,<br />
report manipulation, log manipulation, <strong>and</strong> o<strong>the</strong>r services<br />
like file upload/download. Table 3 gives a list of<br />
ACSI services defined in <strong>the</strong> <strong>IEC</strong> <strong>61850</strong> st<strong>and</strong>ard.<br />
All ACSI services are requested by applications <strong>and</strong><br />
responded by servers. In order to request a service in<br />
a server, an application must first establish a valid twoparty<br />
application association (TPAA) with <strong>the</strong> server.<br />
The TPAA maintains <strong>the</strong> session states <strong>and</strong> provides a<br />
virtual view of <strong>the</strong> server to <strong>the</strong> application. A typical<br />
interaction procedure between an application A <strong>and</strong> a<br />
server S goes as follows:<br />
1. A establishes a TCP connection with S;<br />
2. A “logs in” to S by requesting <strong>the</strong> Associate service<br />
from S, providing au<strong>the</strong>ntication related information<br />
as parameters;<br />
Figure 4: The data model of <strong>the</strong> <strong>IEC</strong> <strong>61850</strong><br />
3. S validates <strong>the</strong> information provided by A <strong>and</strong> creates<br />
a TPAA object, which provides a virtual view<br />
of S to A;<br />
4. A requests subsequent services while S processes<br />
<strong>the</strong> requests <strong>and</strong> responses with appropriate responses<br />
defined in <strong>the</strong> <strong>IEC</strong> <strong>61850</strong> st<strong>and</strong>ard;<br />
5. A issues a Release request to S;<br />
6. S reclaims <strong>the</strong> TPAA of A <strong>and</strong> ends <strong>the</strong> session.<br />
The virtual view of server provided by a TPAA enforces<br />
<strong>the</strong> access control policies set forth by <strong>the</strong> server.<br />
This virtual view defines which objects in <strong>the</strong> server are<br />
visible <strong>and</strong> accessible to <strong>the</strong> application <strong>and</strong> what kinds<br />
of service of those objects are accessible from <strong>the</strong> application.<br />
The concept of virtual view is very flexible <strong>and</strong><br />
5