TFO & Incident centered security management - Department of ...
TFO & Incident centered security management - Department of ...
TFO & Incident centered security management - Department of ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
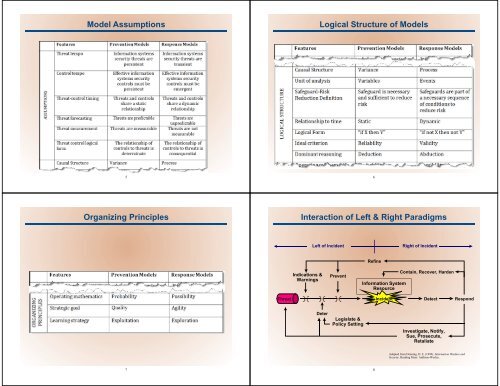
Model Assumptions<br />
Logical Structure <strong>of</strong> Models<br />
5<br />
6<br />
Organizing Principles<br />
Interaction <strong>of</strong> Left & Right Paradigms<br />
Left <strong>of</strong> <strong>Incident</strong><br />
Right <strong>of</strong> <strong>Incident</strong><br />
Indications &<br />
Warnings<br />
Prevent<br />
Refine<br />
Information System<br />
Resource<br />
Contain, Recover, Harden<br />
Threat<br />
<strong>Incident</strong><br />
Detect<br />
Respond<br />
Deter<br />
Legislate &<br />
Policy Setting<br />
Investigate, Notify,<br />
Sue, Prosecute,<br />
Retaliate<br />
Adapted from Denning, D. E. (1999). Information Warfare and<br />
Security. Reading Mass: Addison-Wesley.<br />
7<br />
8