TFO & Incident centered security management - Department of ...
TFO & Incident centered security management - Department of ...
TFO & Incident centered security management - Department of ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
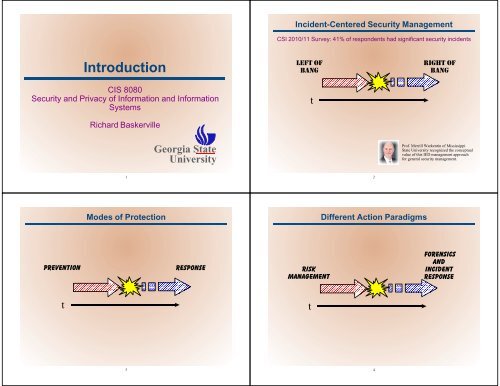
<strong>Incident</strong>-Centered Security Management<br />
CSI 2010/11 Survey: 41% <strong>of</strong> respondents had significant <strong>security</strong> incidents<br />
Introduction<br />
CIS 8080<br />
Security and Privacy <strong>of</strong> Information and Information<br />
Systems<br />
Richard Baskerville<br />
LEFT OF<br />
BANG<br />
t<br />
RIGHT OF<br />
BANG<br />
Georgia State<br />
University<br />
Pr<strong>of</strong>. Merrill Warkentin <strong>of</strong> Mississippi<br />
State University recognized the conceptual<br />
value <strong>of</strong> this IED <strong>management</strong> approach<br />
for general <strong>security</strong> <strong>management</strong>.<br />
1<br />
2<br />
Modes <strong>of</strong> Protection<br />
Different Action Paradigms<br />
Prevention<br />
Response<br />
Risk<br />
Management<br />
Forensics<br />
and<br />
<strong>Incident</strong><br />
Response<br />
t<br />
t<br />
3<br />
4
Model Assumptions<br />
Logical Structure <strong>of</strong> Models<br />
5<br />
6<br />
Organizing Principles<br />
Interaction <strong>of</strong> Left & Right Paradigms<br />
Left <strong>of</strong> <strong>Incident</strong><br />
Right <strong>of</strong> <strong>Incident</strong><br />
Indications &<br />
Warnings<br />
Prevent<br />
Refine<br />
Information System<br />
Resource<br />
Contain, Recover, Harden<br />
Threat<br />
<strong>Incident</strong><br />
Detect<br />
Respond<br />
Deter<br />
Legislate &<br />
Policy Setting<br />
Investigate, Notify,<br />
Sue, Prosecute,<br />
Retaliate<br />
Adapted from Denning, D. E. (1999). Information Warfare and<br />
Security. Reading Mass: Addison-Wesley.<br />
7<br />
8
<strong>Incident</strong>s<br />
Theory <strong>of</strong> Secure Information<br />
Systems<br />
Prevention<br />
t<br />
Recovery<br />
H<strong>of</strong>fman, L., Michelman, E., and Clements, D. "SECURATE - Security evaluation and analysis<br />
using fuzzy metrics," in: AFIPS National Computer Conference Proceedings, 1978, pp. 531-<br />
540.<br />
The natural relationship involves the association <strong>of</strong> potential<br />
intrusion activities associated with each member <strong>of</strong> the set <strong>of</strong><br />
system objects. These threat-object relations defined a set <strong>of</strong><br />
edges T i O j that manifest the components <strong>of</strong> in<strong>security</strong> or risk<br />
in systems.<br />
T 1<br />
T 2<br />
O 1<br />
O 2<br />
T 3<br />
O 3<br />
T 4<br />
O m<br />
T n<br />
T<br />
O<br />
9<br />
10<br />
Theory <strong>of</strong> Secure Information<br />
Systems<br />
The relationship between a set <strong>of</strong> system objects (each with a<br />
loss value), a set <strong>of</strong> threats (each with a likelihood), and a set<br />
<strong>of</strong> system <strong>security</strong> features (each with a resistance). In a<br />
protected system, all edges are instead prescribed in the form<br />
T i F k and F k O j that represents the insertion <strong>of</strong> <strong>security</strong> features<br />
between threats and system objects.<br />
Security Objects<br />
T 1<br />
T 2<br />
F 1<br />
F 2<br />
T 3<br />
F 3<br />
T 4<br />
T n<br />
O 1<br />
O 2<br />
O 3<br />
F l<br />
O m<br />
T F O<br />
11<br />
12
Types <strong>of</strong> Security Objects<br />
PPhysical Assets<br />
< Computers and communications machinery<br />
< Attack with physical assaults<br />
PS<strong>of</strong>t Assets<br />
< Protocols and s<strong>of</strong>tware<br />
< Attack with cracking and malicious code<br />
PPsychic Assets<br />
< Perceptions and information<br />
< Attack with data falsification<br />
Security Threats<br />
13<br />
14<br />
Security Breaches<br />
CSI 2010/2011 Computer Crime and Security Survey<br />
P Malware Infection: 67%<br />
P Misrepresented by phishing: 39%<br />
P Laptop/mobile theft: 34%<br />
P Bots or zombies inside the organization: 29%<br />
P Insider abuse <strong>of</strong> internet (porno, pirate, abusive email):<br />
25%<br />
P Denial <strong>of</strong> service attacks: 17%<br />
P Insider unauthorized access to info: 13%<br />
P Password sniffing: 12%<br />
P Outsider system penetration: 11%<br />
Impacts<br />
CSI 2010/2011 Computer Crime and Security Survey<br />
P Compromise <strong>of</strong> personal identifiable info 16%<br />
P Theft <strong>of</strong> proprietary information: 10%<br />
P Financial fraud: 9%<br />
P Targeted attacks: 45.2%<br />
P Concern for insider & fraud giving way to “targeted<br />
attacks”<br />
< Advanced Persistent Threats<br />
< Attack 2.0<br />
15<br />
16
Data Breach Victims<br />
2013 Verizon Data Breach Investigation Report<br />
Data Breach Perpetrators<br />
2013 Verizon Data Breach Investigation Report<br />
17<br />
18<br />
Breaching Techniques<br />
2013 Verizon Data Breach Investigation Report<br />
Data Breach Commonalities<br />
2013 Verizon Data Breach Investigation Report<br />
19<br />
20
Security Features<br />
Security Features<br />
International<br />
Treaties<br />
Standards<br />
Laws<br />
Institutions<br />
Security<br />
Policies &<br />
Organizations<br />
Practices &<br />
Safeguards<br />
CobiT<br />
ISO 27001<br />
ISO 27002<br />
21<br />
22<br />
Regulatory Compliance Improves Security<br />
Double-Edged Complexity<br />
T 1<br />
T 2<br />
O 1<br />
O 2<br />
T 3<br />
O 3<br />
T 4<br />
O m<br />
T n<br />
T<br />
O<br />
Applicable regulations from:<br />
2010/2011 CSI Computer<br />
Security Survey<br />
T 1<br />
T 2<br />
F 1<br />
F 2<br />
T 3<br />
F 3<br />
T 4<br />
T n<br />
O 1<br />
O 2<br />
O 3<br />
F l<br />
O m<br />
T F O<br />
23<br />
24
Introduction<br />
CIS 8080<br />
Security and Privacy <strong>of</strong> Information and Information<br />
Systems<br />
Richard Baskerville<br />
Georgia State<br />
University<br />
25<br />
26