Weakness is a better teacher than strength ... - PDF Archive
Weakness is a better teacher than strength ... - PDF Archive
Weakness is a better teacher than strength ... - PDF Archive
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
-~-----------------------...<br />
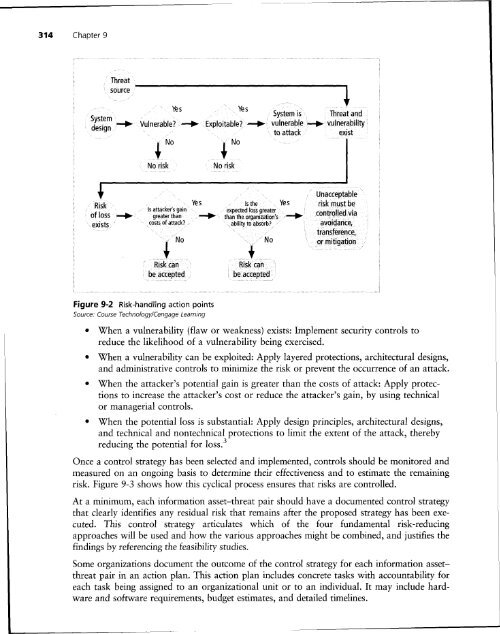
314 Chapter 9<br />
Threat<br />
source<br />
'"'--------------------<br />
Yes<br />
Yes<br />
System <strong>is</strong> Threat and<br />
System .........<br />
design . toattack ex<strong>is</strong>t<br />
Vulnerable? -+ Exploitable?-+- vull1erapl~·......i vulnerability<br />
+No<br />
~ No<br />
No r<strong>is</strong>k<br />
No r<strong>is</strong>k<br />
Figure 9-2<br />
R<strong>is</strong>k-handling action points<br />
Source: Course Technology/Cengage Learning<br />
• When a vulnerability (flaw or weakness) ex<strong>is</strong>ts: Implement security controls to<br />
reduce the likelihood of a vulnerability being exerc<strong>is</strong>ed.<br />
• When a vulnerability can be exploited: Apply layered protections, architectural designs,<br />
and admin<strong>is</strong>trative controls to minimize the r<strong>is</strong>k or prevent the occurrence of an attack.<br />
• When the attacker's potential gain <strong>is</strong> greater <strong>than</strong> the costs of attack: Apply protections<br />
to increase the attacker's cost or reduce the attacker's gain, by using technical<br />
or managerial controls.<br />
• When the potential loss <strong>is</strong> substantial: Apply design principles, architectural designs,<br />
and technical and nontechnical protections to limit the extent of the attack, thereby<br />
reducing the potential for loss. 3<br />
Once a control strategy has been selected and implemented, controls should be monitored and<br />
measured on an ongoing bas<strong>is</strong> to determine their effectiveness and to estimate the remaining<br />
r<strong>is</strong>k. Figure 9-3 shows how th<strong>is</strong> cyclical process ensures that r<strong>is</strong>ks are controlled.<br />
At a minimum, each information asset-threat pair should have a documented control strategy<br />
that clearly identifies any residual r<strong>is</strong>k that remains after the proposed strategy has been executed.<br />
Th<strong>is</strong> control strategy articulates which of the four fundamental r<strong>is</strong>k-reducing<br />
approaches will be used and how the various approaches might be combined, and justifies the<br />
findings by referencing the feasibility studies.<br />
Some organizations document the outcome of the control strategy for each information assetthreat<br />
pair in an action plan. Th<strong>is</strong> action plan includes concrete tasks with accountability for<br />
each task being assigned to an organizational unit or to an individual. It may include hardware<br />
and software requirements, budget estimates, and detailed timelines.