A Structured Approach to Classifying Security Vulnerabilities - Cert
A Structured Approach to Classifying Security Vulnerabilities - Cert
A Structured Approach to Classifying Security Vulnerabilities - Cert
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
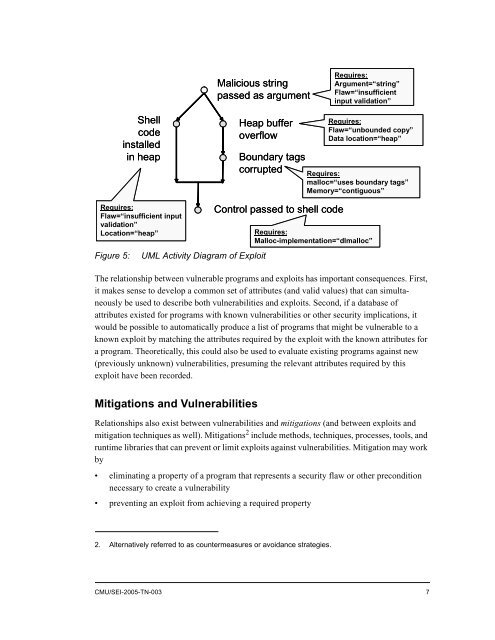
Malicious string<br />
passed as argument<br />
Requires:<br />
Argument=“string”<br />
Flaw=“insufficient<br />
input validation”<br />
Shell<br />
code<br />
installed<br />
in heap<br />
Heap buffer<br />
overflow<br />
Boundary tags<br />
corrupted<br />
Requires:<br />
Flaw=“unbounded copy”<br />
Data location=“heap”<br />
Requires:<br />
malloc=“uses boundary tags”<br />
Memory=“contiguous”<br />
Requires:<br />
Flaw=“insufficient input<br />
validation”<br />
Location=“heap”<br />
Figure 5:<br />
UML Activity Diagram of Exploit<br />
Control passed <strong>to</strong> shell code<br />
Requires:<br />
Malloc-implementation=“dlmalloc”<br />
The relationship between vulnerable programs and exploits has important consequences. First,<br />
it makes sense <strong>to</strong> develop a common set of attributes (and valid values) that can simultaneously<br />
be used <strong>to</strong> describe both vulnerabilities and exploits. Second, if a database of<br />
attributes existed for programs with known vulnerabilities or other security implications, it<br />
would be possible <strong>to</strong> au<strong>to</strong>matically produce a list of programs that might be vulnerable <strong>to</strong> a<br />
known exploit by matching the attributes required by the exploit with the known attributes for<br />
a program. Theoretically, this could also be used <strong>to</strong> evaluate existing programs against new<br />
(previously unknown) vulnerabilities, presuming the relevant attributes required by this<br />
exploit have been recorded.<br />
Mitigations and <strong>Vulnerabilities</strong><br />
Relationships also exist between vulnerabilities and mitigations (and between exploits and<br />
mitigation techniques as well). Mitigations 2 include methods, techniques, processes, <strong>to</strong>ols, and<br />
runtime libraries that can prevent or limit exploits against vulnerabilities. Mitigation may work<br />
by<br />
• eliminating a property of a program that represents a security flaw or other precondition<br />
necessary <strong>to</strong> create a vulnerability<br />
• preventing an exploit from achieving a required property<br />
2. Alternatively referred <strong>to</strong> as countermeasures or avoidance strategies.<br />
CMU/SEI-2005-TN-003 7