Use Of Technology To Stalk
Use Of Technology To Stalk
Use Of Technology To Stalk
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
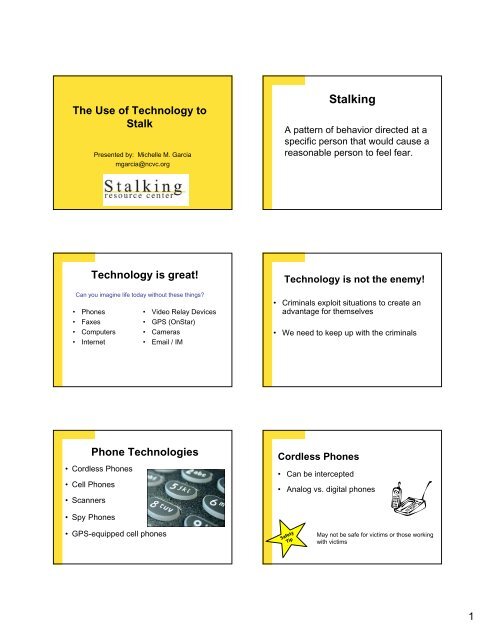
The <strong>Use</strong> of <strong>Technology</strong> to<br />
<strong>Stalk</strong><br />
Presented by: Michelle M. Garcia<br />
mgarcia@ncvc.org<br />
<strong>Technology</strong> is great!<br />
Can you imagine life today without these things?<br />
• Phones<br />
• Faxes<br />
• Computers<br />
• Internet<br />
• Video Relay Devices<br />
• GPS (OnStar)<br />
• Cameras<br />
• Email / IM<br />
Phone Technologies<br />
• Cordless Phones<br />
• Cell Phones<br />
• Scanners<br />
• Spy Phones<br />
• GPS-equipped cell phones<br />
<strong>Stalk</strong>ing<br />
A pattern of behavior directed at a<br />
specific person that would cause a<br />
reasonable person to feel fear.<br />
<strong>Technology</strong> is not the enemy!<br />
• Criminals exploit situations to create an<br />
advantage for themselves<br />
• We need to keep up with the criminals<br />
Cordless Phones<br />
• Can be intercepted<br />
• Analog vs. digital phones<br />
Safety<br />
Tip<br />
May not be safe for victims or those working<br />
with victims<br />
1
Cell & Mobile Phones<br />
• Analog v. Digital<br />
• Understand features of your phone –<br />
auto answer<br />
Scanners<br />
Scanners<br />
Spy Phones<br />
2
Tracking via cell phones<br />
With<br />
People<br />
Finder<br />
3
SIM Recovery<br />
• Subscriber Identity Module<br />
• Portable memory chip used by cell carriers<br />
operating on the Global System for Mobile<br />
Communication (GSM) network: AT&T/Cingular, T-<br />
Mobile, and others<br />
Texting<br />
4
Answering Machines &<br />
Voice Mail<br />
• <strong>Stalk</strong>er accesses victim’s voice mail or<br />
answering machine to gather information<br />
• <strong>Stalk</strong>er leaves messages<br />
– If stalker leaves a message, permission to be<br />
taped is usually assumed<br />
Caller ID<br />
• Good for avoiding calls<br />
• Blocking your number: *67 + number<br />
• 800# exception<br />
Answering Machines &<br />
Voice Mail<br />
• Talk to local prosecutors/law<br />
enforcement about their preferred<br />
method of evidence collection<br />
• Get answering machines donated<br />
& train on use (to screen calls &<br />
document harassing messages)<br />
• Spoof cards<br />
Anonymizers<br />
• Assistive technologies<br />
Spoof Card<br />
Safety<br />
Tip<br />
No computer needed! Simply dial the toll free number<br />
from the calling card you purchase.<br />
1. Enter your pin number.<br />
2. Enter Destination number.<br />
3. Enter Any Caller ID Number you wish to display.<br />
4. Choose the voice you would like to use.<br />
5. Your call is connected using the specified Caller ID Number.<br />
As an added bonus, we offer you the option to record your<br />
conversation for FREE which you can later retrieve by logging-in to<br />
your control panel or calling our 800 number from anywhere.<br />
In addition, we also offer the ability to change your voice<br />
to sound like a man, a women or yourself for FREE.<br />
5
IP Relay www.ip-relay.com<br />
Assistive <strong>Technology</strong><br />
Devices<br />
• Learn available TTY, relay, & interpreter<br />
resources<br />
• Talk to victim about potential<br />
impersonation & develop a system for<br />
identifying caller (code word)<br />
• Safety plan around TTY devices &<br />
clearing the history<br />
Safety<br />
Tip<br />
Assistive <strong>Technology</strong> Devices<br />
• Provide a valuable resource for deaf and<br />
hard of hearing persons<br />
• Safety plan around TTY devices & clearing<br />
the history<br />
• Talk to victim about potential<br />
impersonation & develop a system for<br />
identifying caller (code word or phrase)<br />
IP Relay Case<br />
• This is Zack your relay operator 5243 we<br />
have a message. You’re a heartless,<br />
sick, nerdy b@$#%. Die and go to hell.<br />
End of message. Thank you IP relay…<br />
• This is Ashley relay operator 7041 with a<br />
message. Go suck some person…yes,<br />
hope you get AIDS. End of message.<br />
Thank you IP relay 7041 Goodbye. End<br />
of message. <strong>To</strong> delete this….<br />
Global Positioning Systems<br />
(GPS) & Locating Devices<br />
6
$250<br />
7
Vehicle Tracking Menu Cameras<br />
Spy Cams<br />
How can they be disguised?<br />
Eyeball cam<br />
8
Why would stalkers use them?<br />
• Keep track of victims—learn routine, etc.<br />
• Keep track of victim without being seen<br />
• Find new victims—boyfriends, etc.<br />
• Scare and harass— “I’m watching and<br />
know what you are doing”<br />
Camera Detection<br />
• If remote transmit, there will be a signal.<br />
– Can buy a device that will tell you if such<br />
signals are being transmitted.<br />
• If it is wired instead of wireless… no way<br />
to detect except by finding it with your<br />
own eyes.<br />
What to know<br />
• Purchasing surveillance equipment is<br />
getting cheaper -- kits start under $100<br />
• Cameras can be hidden in just about<br />
anything<br />
• Remote as well as hardwired cameras<br />
• Plenty of information available on how to<br />
operate systems<br />
Cameras for Safety<br />
• Personal security– can put cameras up<br />
around the home<br />
• Can be used to document stalking or<br />
capture evidence<br />
COMPUTERS Computers<br />
Safety<br />
Tip<br />
• Information gained by subterfuge and<br />
illegal activity<br />
• Information about ourselves we put out<br />
there<br />
9
Spyware & Computer Monitoring<br />
• Software program or hardware component that<br />
helps an an unauthorized third party gather<br />
information about the user’s computer use without<br />
user’s knowledge or consent.<br />
• Can be encoded in an email message, game, or<br />
Web site<br />
• Very hard to detect!<br />
• Symptoms: often none, they typically run in stealth<br />
mode so user never knows it’s installed.<br />
• Some are legitimate: parental controls, employee<br />
monitoring<br />
“Make the Remote Computer Talk”<br />
ComputerGOD 1.00<br />
ComputerGOD silently records all keystrokes, websites visited,<br />
email received, passwords, instant messages, details of<br />
applications and windows opened, and snapshots of the screen<br />
taken periodically. In addition, this application can control most<br />
functions of a remote computer. It can restart, shutdown, and<br />
logoff a computer, send chat messages, control the remote<br />
computer’s desktop and mouse, transfer files, and make the<br />
remote computer talk any words. ComputerGOD is also remote<br />
installation capable and is designed to allow a user to monitor<br />
and control multiple computers.<br />
These powerful features make ComputerGOD the most powerful remote surveillance and control program on the market.<br />
10
Limited Prevention/<br />
Identification<br />
Safety<br />
Tip<br />
Safety Tips for Advocates<br />
• Regularly ask:<br />
– “Do you use a computer?” and<br />
Safety<br />
Tips<br />
– “Does the offender have onsite or remote<br />
access to it?”<br />
• Encourage using a “safer” computer at<br />
the library or elsewhere<br />
• Discuss risk from tech savvy stalkers<br />
Keystroke Logging Hardware<br />
Keystroke logging keyboard<br />
Information We Put<br />
Out There<br />
11
Email<br />
How do stalkers use email?<br />
• Send email to victim<br />
• Intercept and monitor email<br />
• Impersonate victim and send offensive<br />
messages to others<br />
What can Victims do?<br />
� Passwords: <strong>Use</strong> variations of numbers<br />
and letters<br />
� Save all harassing or suspicious emails<br />
� Never open suspicious emails or<br />
attachments<br />
Instant Messaging Social Networking Sites<br />
Where am I?<br />
At Library – 3rd Floor Stacks<br />
Safety<br />
Tip<br />
• Creating an online community for friends &<br />
family members or meeting new friends<br />
(examples: My Space, Facebook, LinkedIn)<br />
• Computers can bring people together in<br />
various ways<br />
– Message boards/pursuits of specific interests<br />
– Online trading and commerce<br />
– Community activism<br />
12
What Other<br />
Information is Out<br />
There?<br />
Directories & Search Engines<br />
• Photos<br />
Think Before You Post<br />
• School information<br />
• Work information<br />
• Favorite hangouts<br />
Safety<br />
Tip<br />
• What is on your friends’ pages about<br />
you?<br />
<strong>Stalk</strong>ers & The Web<br />
• Using Web sites<br />
– Pages that assist stalkers<br />
• Creating Web sites<br />
– Pages created to:<br />
• Harass<br />
• Record or document behaviors<br />
• Slander or defame<br />
• Solicit others<br />
• What’s out there about you?<br />
• How about the survivor, witnesses or<br />
suspects?<br />
13
ZabaSearch ~ Free Databases<br />
Births<br />
Adoptions<br />
Courts<br />
Marriages<br />
Sex offenders<br />
Military<br />
Schools<br />
Property<br />
Vehicles<br />
Licenses<br />
Campaign $<br />
Veromi<br />
Court & Government Sites Individual & Organization Sites<br />
Information Brokers<br />
PTA<br />
Other Databases<br />
• Chain store discount cards<br />
• Lotteries<br />
• National associations & organizations<br />
Protect your information<br />
14
Privacy & Safety Tips<br />
Safety<br />
Tip<br />
• Talk to schools about records<br />
• Protect your home address and phone<br />
number<br />
• Protect your email address and Web<br />
postings<br />
• Search for yourself – often – using<br />
directories and information brokers<br />
"It's actually obscene what you can find<br />
out about people on the Internet.“<br />
-Liam Youens<br />
<strong>Stalk</strong>ers & The Web<br />
• Using Web sites<br />
– Pages that assist stalkers<br />
• Creating Web sites<br />
– Pages created to:<br />
• Harass<br />
• Record or document behaviors<br />
• Slander or defame<br />
• Solicit others<br />
15
Practitioners: 202-467-8700<br />
Victims: 1-800-FYI-CALL<br />
gethelp@ncvc.org<br />
www.ncvc.org/src<br />
Privacy & Safety Tips<br />
• P.O. Boxes or Parcel Plus, UPS Store<br />
(DMV may print P.O. Box on drivers license)<br />
• Virtual Voice Mail phone number<br />
• Utilities<br />
− consider an apartment with them included<br />
− small apartment complex vs. national chain<br />
• Consider 2 legal residences<br />
• Research address confidentiality programs<br />
• Check voter registration policies<br />
16