Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
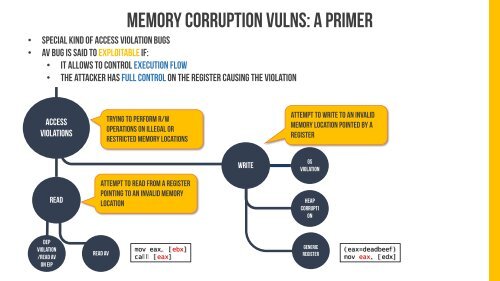
Memory corruption vulns: a primer<br />
• Special kind of access violation bugs<br />
• Av bug is said to exploitable if:<br />
• It allows to control execution flow<br />
• the attacker has full control on the register causing the violation<br />
ACCESS<br />
VIOLATIONS<br />
Trying to perform r/w<br />
operations on illegal or<br />
restricted memory locations<br />
Attempt to write to an invalid<br />
memory location pointed by a<br />
register<br />
WRITE<br />
GS<br />
Violation<br />
READ<br />
Attempt to read from a register<br />
pointing to an invalid memory<br />
location<br />
HEAP<br />
CORRUPTI<br />
ON<br />
DEP<br />
Violation<br />
/Read AV<br />
on EIP<br />
READ AV<br />
mov eax, [ebx]<br />
call [eax]<br />
G<strong>EN</strong>ERIC<br />
register<br />
(eax=deadbeef)<br />
mov eax, [edx]