privacy risk assessment - short form — confidential - International ...
privacy risk assessment - short form — confidential - International ...
privacy risk assessment - short form — confidential - International ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
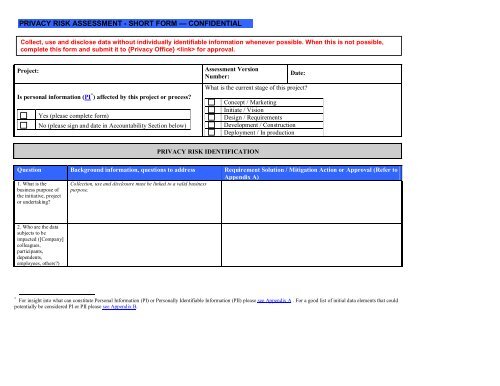
PRIVACY RISK ASSESSMENT - SHORT FORM <strong>—</strong> CONFIDENTIAL<br />
Collect, use and disclose data without individually identifiable in<strong>form</strong>ation whenever possible. When this is not possible,<br />
complete this <strong>form</strong> and submit it to {Privacy Office} for approval.<br />
Project:<br />
Is personal in<strong>form</strong>ation (PI * ) affected by this project or process<br />
Yes (please complete <strong>form</strong>)<br />
No (please sign and date in Accountability Section below)<br />
Assessment Version<br />
Number:<br />
Date:<br />
What is the current stage of this project<br />
Concept / Marketing<br />
Initiate / Vision<br />
Design / Requirements<br />
Development / Construction<br />
Deployment / In production<br />
PRIVACY RISK IDENTIFICATION<br />
Question Background in<strong>form</strong>ation, questions to address Requirement Solution / Mitigation Action or Approval (Refer to<br />
Appendix A)<br />
1. What is the<br />
business purpose of<br />
the initiative, project<br />
or undertaking<br />
Collection, use and disclosure must be linked to a valid business<br />
purpose.<br />
2. Who are the data<br />
subjects to be<br />
impacted ([Company]<br />
colleagues,<br />
participants,<br />
dependents,<br />
employees, others)<br />
* For insight into what can constitute Personal In<strong>form</strong>ation (PI) or Personally Identifiable In<strong>form</strong>ation (PII) please see Appendix A . For a good list of initial data elements that could<br />
potentially be considered PI or PII please see Appendix B.
Question Background in<strong>form</strong>ation, questions to address Requirement Solution / Mitigation Action or Approval (Refer to<br />
Appendix A)<br />
3. What PI is<br />
collected, used,<br />
retained or disclosed<br />
Feel free to use Appendix B as an initial reference, and then be sure<br />
and document any addition data elements here that may be<br />
considered sensitive in the country(s) of concern.<br />
Can the <strong>risk</strong> of unauthorized access be mitigated by de-identifying the PI, in whole<br />
or part<br />
*For each sensitive<br />
data element, please<br />
describe the need for<br />
collecting or using it..<br />
Can each data element be linked to a valid business or legal reason for collection<br />
and use<br />
Comment [A1]: Why are we asking<br />
them if a data element is sensitive<br />
4. Data flow: Please<br />
describe the flow of<br />
PI (between client,<br />
ourselves, any<br />
vendors or third<br />
parties).<br />
5. Are there any client<br />
contractual<br />
requirements<br />
affecting or requiring<br />
this collection, use or<br />
disclosure of PI<br />
6. Will any third party<br />
be collecting,<br />
managing or<br />
processing PI<br />
provided by<br />
[Company] Please<br />
attach any relevant<br />
agreement.<br />
7. To whom is the PI<br />
disclosed Why (i.e.,<br />
business, legal, or<br />
regulatory reason)<br />
8. Where is the PI<br />
stored (physical<br />
location)<br />
Data flows are very helpful to understand how PI moves and with<br />
whom it’s shared: this is a template to use:<br />
Attach relevant contract terms.<br />
If PI is being shared with a third party or being processed by a<br />
vendor, please complete the data flow above.<br />
Include where appropriate, PI shared with employers, vendors of the<br />
client, or other third parties.<br />
Are there any new vendors involved Have the vendor(s) gone through the Vendor<br />
Security & Privacy Risk Assessment<br />
Page 2 of 8
Question Background in<strong>form</strong>ation, questions to address Requirement Solution / Mitigation Action or Approval (Refer to<br />
Appendix A)<br />
9. Is the PI gathered<br />
in one country and<br />
If PI is moving from one country to another or is accessible from<br />
another country, please complete the data flow above.<br />
accessible from,<br />
processed in or<br />
transferred to<br />
another If so, please<br />
describe.<br />
10. Describe any IT<br />
systems in which the<br />
PI is stored or<br />
processed.<br />
Identify databases, servers, or applications.<br />
11. What safeguards<br />
are in place to secure<br />
the PI (physical and<br />
logical) Is PI<br />
transmitted and stored<br />
securely<br />
12. How is access to<br />
the PI restricted<br />
Identify how need-to-know is enforced, and who is responsible to<br />
determine and manage access.<br />
13. How long is the<br />
PI to be retained Is<br />
this the minimal<br />
period Will the PI be<br />
returned to the client<br />
(if applicable)<br />
Describe any issues with regards to retention and/or disposal; is the<br />
PI commingled with other client data<br />
Can individual data elements be removed or deleted sooner<br />
Is automatic retention applied (system-based)<br />
Is the PI securely deleted<br />
Page 3 of 8
Potential Privacy Loss Description (Mandatory):<br />
What are the possible consequences of a <strong>privacy</strong> breach: describe financial, reputational or other impacts.<br />
Management Action(s) (Completed/Proposed):<br />
Are the <strong>risk</strong>s described in this <strong>assessment</strong> acceptable to the business If not, what actions will be undertaken to reduce <strong>risk</strong>s to an acceptable level<br />
PRIVACY RISK EXPOSURE SCORE (High, Medium or Low) (Optional)<br />
PROBABILITY: Probability of negative outcome<br />
LOSS: Degree or severity of harm if negative outcome occurs<br />
Status:<br />
PRIVACY RISK TRACKING – ACCOUNTABILITY (please sign or indicate approval) - MANDATORY<br />
Project Sponsor/Business Owner:<br />
Date:<br />
Cost Centre:<br />
Line of Business/Department:<br />
Project Manager:<br />
Privacy Risk Assessment reviewed<br />
by:<br />
Follow-up Actions:<br />
Date:<br />
Date:<br />
Date:<br />
Escalation (if required):<br />
Exception request required<br />
Page 4 of 8
Final/Residual Risk Notes:<br />
Additional Comments/Discussion:<br />
Page 5 of 8
Appendix A<br />
Personal In<strong>form</strong>ation (PI) or Personally Identifiable In<strong>form</strong>ation (PII) includes in<strong>form</strong>ation collected in any <strong>form</strong> about an identifiable<br />
individual (including [Company]’s own colleagues). Examples of PI or PII include: age, identification numbers, income, ethnic origin, opinions<br />
of or about the individual, comments, credit records, account history and intentions (for example, to acquire goods or services). PII may also<br />
include two discrete pieces of in<strong>form</strong>ation which individually do not identify an individual, but together can or may.<br />
Sensitive PI: Sensitive PI includes an individual’s first name and last name, or first initial and last name, in combination with one or more of<br />
the following:<br />
• National or government-issued identifiers, such as Social Security Number, Social Insurance Number, or driver’s license<br />
• Driver's license number or state-issued identification card number<br />
• Financial account number, credit or debit card number<br />
• Protected Health In<strong>form</strong>ation (PHI)<br />
Sensitive PI does not include in<strong>form</strong>ation that is lawfully obtained from publicly available in<strong>form</strong>ation, or from federal, state, or local<br />
government records made available to the general public. Sensitive PI also does not include in<strong>form</strong>ation which is otherwise considered<br />
sensitive when all in<strong>form</strong>ation identifying the individual is removed. Note that this definition is dependent on national and regional laws, and<br />
that guidance should be sought from Compliance & Professional Standards and the Legal Department.<br />
Requirement Solution / Mitigation Action or Approval<br />
If you have mitigation actions, please include in this section otherwise this section will be used for Privacy updates<br />
Page 6 of 8
Appendix B<br />
DATA ELEMENT<br />
WHO IS THE DATA ABOUT<br />
(Place an X in each box that applies for every data element in scope of the project)<br />
Company<br />
Client/Consumer<br />
Personal In<strong>form</strong>ation<br />
Employee,<br />
Temporary<br />
Worker, or<br />
dependents<br />
Corporate<br />
Contact<br />
(e.g., John<br />
Smith, X<br />
Corp)<br />
Employee,<br />
Temporary<br />
Worker<br />
Consumer<br />
Patient<br />
Customer<br />
Dependents<br />
Other<br />
(describe<br />
in the<br />
Comments<br />
field)<br />
Comments<br />
(if applicable)<br />
Name including first name or initials<br />
Business Contact Details (e.g. Business Address,<br />
phone, email)<br />
Personal Contact Details (e.g. Home Address,<br />
phone, email)<br />
Dates Of Birth<br />
Applicant Data (e.g. accounts, insurance<br />
application <strong>form</strong>s)<br />
Compensation Data<br />
Human Resources Data<br />
...Employee Attendance Data<br />
…Employee Identification Demographic Data<br />
...Employee Status<br />
...Employee Travel Details<br />
...Employee Work History<br />
…Employee Training and Related Records<br />
…Payroll / Salary Data<br />
…Employee Per<strong>form</strong>ance Data<br />
...Family /Dependent/Beneficiary In<strong>form</strong>ation<br />
IP Address<br />
Page 7 of 8
WHO IS THE DATA ABOUT<br />
(Place an X in each box that applies for every data element in scope of the project)<br />
Sensitive In<strong>form</strong>ation<br />
Company<br />
Employee,<br />
Temporary<br />
Worker, or<br />
dependents<br />
Corporate<br />
Contact<br />
(e.g., John<br />
Smith, X<br />
Corp)<br />
Employee,<br />
Temporary<br />
Worker<br />
Client<br />
Consumer<br />
Patient<br />
Customer<br />
Dependents<br />
Other<br />
(describe<br />
in the<br />
Comments<br />
field)<br />
Comments<br />
(if applicable)<br />
Social Security Numbers (SSN-U.S.)<br />
Other Government Issued ID Numbers<br />
Banking / Financial Info / Account History<br />
Credit Card, Debit Card + PIN, and Banking<br />
In<strong>form</strong>ation<br />
Visa or Passport Numbers<br />
Driver's License<br />
In<strong>form</strong>ation relating to race or ethnic origin,<br />
religious beliefs, health, political opinions, sexual<br />
orientation or criminal record. Please detail what<br />
is collected.<br />
National or Health Insurance Numbers<br />
…Medical History<br />
…Medical Claims<br />
…Medical Insurance Numbers<br />
Page 8 of 8