Exceed onDemand A Technical Whitepaper
Exceed onDemand A Technical Whitepaper
Exceed onDemand A Technical Whitepaper
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>Exceed</strong> <strong>onDemand</strong> 5 — A <strong>Technical</strong> <strong>Whitepaper</strong><br />
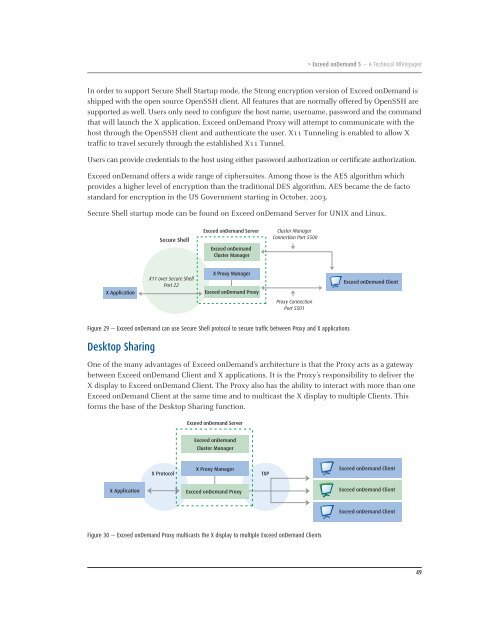
In order to support Secure Shell Startup mode, the Strong encryption version of <strong>Exceed</strong> <strong>onDemand</strong> is<br />
shipped with the open source OpenSSH client. All features that are normally offered by OpenSSH are<br />
supported as well. Users only need to configure the host name, username, password and the command<br />
that will launch the X application. <strong>Exceed</strong> <strong>onDemand</strong> Proxy will attempt to communicate with the<br />
host through the OpenSSH client and authenticate the user. X11 Tunneling is enabled to allow X<br />
traffic to travel securely through the established X11 Tunnel.<br />
Users can provide credentials to the host using either password authorization or certificate authorization.<br />
<strong>Exceed</strong> <strong>onDemand</strong> offers a wide range of ciphersuites. Among those is the AES algorithm which<br />
provides a higher level of encryption than the traditional DES algorithm. AES became the de facto<br />
standard for encryption in the US Government starting in October, 2003.<br />
Secure Shell startup mode can be found on <strong>Exceed</strong> <strong>onDemand</strong> Server for UNIX and Linux.<br />
X Application<br />
Secure Shell<br />
X11 over Secure Shell<br />
Port 22<br />
<strong>Exceed</strong> <strong>onDemand</strong> Server<br />
<strong>Exceed</strong> <strong>onDemand</strong><br />
Cluster Manager<br />
X Proxy Manager<br />
<strong>Exceed</strong> <strong>onDemand</strong> Proxy<br />
Cluster Manager<br />
Connection Port 5500<br />
Proxy Connection<br />
Port 5501<br />
Figure 29 — <strong>Exceed</strong> <strong>onDemand</strong> can use Secure Shell protocol to secure traffic between Proxy and X applications<br />
Desktop Sharing<br />
<strong>Exceed</strong> <strong>onDemand</strong> Client<br />
One of the many advantages of <strong>Exceed</strong> <strong>onDemand</strong>’s architecture is that the Proxy acts as a gateway<br />
between <strong>Exceed</strong> <strong>onDemand</strong> Client and X applications. It is the Proxy’s responsibility to deliver the<br />
X display to <strong>Exceed</strong> <strong>onDemand</strong> Client. The Proxy also has the ability to interact with more than one<br />
<strong>Exceed</strong> <strong>onDemand</strong> Client at the same time and to multicast the X display to multiple Clients. This<br />
forms the base of the Desktop Sharing function.<br />
X Application<br />
<strong>Exceed</strong> <strong>onDemand</strong> Server<br />
<strong>Exceed</strong> <strong>onDemand</strong><br />
Cluster Manager<br />
X Proxy Manager<br />
X Protocol TXP<br />
<strong>Exceed</strong> <strong>onDemand</strong> Proxy<br />
Figure 30 — <strong>Exceed</strong> <strong>onDemand</strong> Proxy multicasts the X display to multiple <strong>Exceed</strong> <strong>onDemand</strong> Clients<br />
<strong>Exceed</strong> <strong>onDemand</strong> Client<br />
<strong>Exceed</strong> <strong>onDemand</strong> Client<br />
<strong>Exceed</strong> <strong>onDemand</strong> Client<br />
49