Download PDF - Department of Navy Chief Information Officer - U.S. ...
Download PDF - Department of Navy Chief Information Officer - U.S. ...
Download PDF - Department of Navy Chief Information Officer - U.S. ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Sailor Stores PII in Commercial Facility;<br />
Fails to Pay the Bill<br />
By Steve Muck<br />
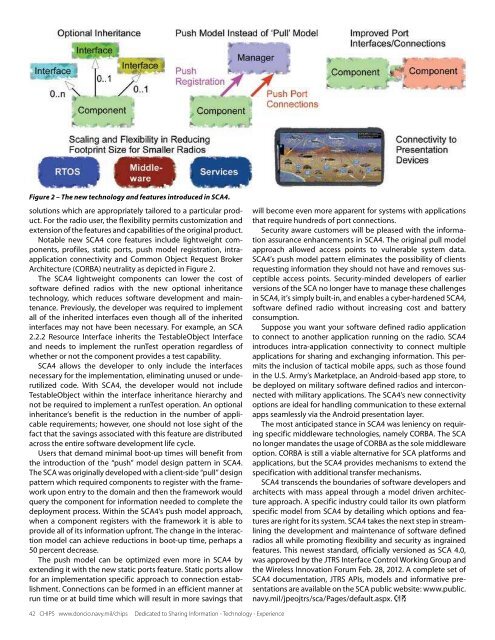
Figure 2 – The new technology and features introduced in SCA4.<br />
solutions which are appropriately tailored to a particular product.<br />
For the radio user, the flexibility permits customization and<br />
extension <strong>of</strong> the features and capabilities <strong>of</strong> the original product.<br />
Notable new SCA4 core features include lightweight components,<br />
pr<strong>of</strong>iles, static ports, push model registration, intraapplication<br />
connectivity and Common Object Request Broker<br />
Architecture (CORBA) neutrality as depicted in Figure 2.<br />
The SCA4 lightweight components can lower the cost <strong>of</strong><br />
s<strong>of</strong>tware defined radios with the new optional inheritance<br />
technology, which reduces s<strong>of</strong>tware development and maintenance.<br />
Previously, the developer was required to implement<br />
all <strong>of</strong> the inherited interfaces even though all <strong>of</strong> the inherited<br />
interfaces may not have been necessary. For example, an SCA<br />
2.2.2 Resource Interface inherits the TestableObject Interface<br />
and needs to implement the runTest operation regardless <strong>of</strong><br />
whether or not the component provides a test capability.<br />
SCA4 allows the developer to only include the interfaces<br />
necessary for the implementation, eliminating unused or underutilized<br />
code. With SCA4, the developer would not include<br />
TestableObject within the interface inheritance hierarchy and<br />
not be required to implement a runTest operation. An optional<br />
inheritance’s benefit is the reduction in the number <strong>of</strong> applicable<br />
requirements; however, one should not lose sight <strong>of</strong> the<br />
fact that the savings associated with this feature are distributed<br />
across the entire s<strong>of</strong>tware development life cycle.<br />
Users that demand minimal boot-up times will benefit from<br />
the introduction <strong>of</strong> the “push” model design pattern in SCA4.<br />
The SCA was originally developed with a client-side “pull” design<br />
pattern which required components to register with the framework<br />
upon entry to the domain and then the framework would<br />
query the component for information needed to complete the<br />
deployment process. Within the SCA4’s push model approach,<br />
when a component registers with the framework it is able to<br />
provide all <strong>of</strong> its information upfront. The change in the interaction<br />
model can achieve reductions in boot-up time, perhaps a<br />
50 percent decrease.<br />
The push model can be optimized even more in SCA4 by<br />
extending it with the new static ports feature. Static ports allow<br />
for an implementation specific approach to connection establishment.<br />
Connections can be formed in an efficient manner at<br />
run time or at build time which will result in more savings that<br />
will become even more apparent for systems with applications<br />
that require hundreds <strong>of</strong> port connections.<br />
Security aware customers will be pleased with the information<br />
assurance enhancements in SCA4. The original pull model<br />
approach allowed access points to vulnerable system data.<br />
SCA4’s push model pattern eliminates the possibility <strong>of</strong> clients<br />
requesting information they should not have and removes susceptible<br />
access points. Security-minded developers <strong>of</strong> earlier<br />
versions <strong>of</strong> the SCA no longer have to manage these challenges<br />
in SCA4, it’s simply built-in, and enables a cyber-hardened SCA4,<br />
s<strong>of</strong>tware defined radio without increasing cost and battery<br />
consumption.<br />
Suppose you want your s<strong>of</strong>tware defined radio application<br />
to connect to another application running on the radio. SCA4<br />
introduces intra-application connectivity to connect multiple<br />
applications for sharing and exchanging information. This permits<br />
the inclusion <strong>of</strong> tactical mobile apps, such as those found<br />
in the U.S. Army’s Marketplace, an Android-based app store, to<br />
be deployed on military s<strong>of</strong>tware defined radios and interconnected<br />
with military applications. The SCA4’s new connectivity<br />
options are ideal for handling communication to these external<br />
apps seamlessly via the Android presentation layer.<br />
The most anticipated stance in SCA4 was leniency on requiring<br />
specific middleware technologies, namely CORBA. The SCA<br />
no longer mandates the usage <strong>of</strong> CORBA as the sole middleware<br />
option. CORBA is still a viable alternative for SCA platforms and<br />
applications, but the SCA4 provides mechanisms to extend the<br />
specification with additional transfer mechanisms.<br />
SCA4 transcends the boundaries <strong>of</strong> s<strong>of</strong>tware developers and<br />
architects with mass appeal through a model driven architecture<br />
approach. A specific industry could tailor its own platform<br />
specific model from SCA4 by detailing which options and features<br />
are right for its system. SCA4 takes the next step in streamlining<br />
the development and maintenance <strong>of</strong> s<strong>of</strong>tware defined<br />
radios all while promoting flexibility and security as ingrained<br />
features. This newest standard, <strong>of</strong>ficially versioned as SCA 4.0,<br />
was approved by the JTRS Interface Control Working Group and<br />
the Wireless Innovation Forum Feb. 28, 2012. A complete set <strong>of</strong><br />
SCA4 documentation, JTRS APIs, models and informative presentations<br />
are available on the SCA public website: www.public.<br />
navy.mil/jpeojtrs/sca/Pages/default.aspx.<br />
T<br />
he following is a recently reported personally identifiable<br />
information (PII) data breach involving a Sailor<br />
who improperly handled PII. Incidents such as this one<br />
will be reported in CHIPS magazine to increase PII awareness.<br />
Names have been changed or omitted, but details are factual<br />
and based on reports sent to the <strong>Department</strong> <strong>of</strong> the <strong>Navy</strong><br />
<strong>Chief</strong> <strong>Information</strong> <strong>Officer</strong> Privacy Office.<br />
The Incident<br />
A Sailor removed several boxes <strong>of</strong> personnel and training<br />
records from his command and stored them, along with his<br />
personal gear, in an <strong>of</strong>f-base commercial facility. Months<br />
passed during which time the Sailor failed to pay his monthly<br />
storage fee. While the bills remained unpaid, the Sailor transferred<br />
to a new command. After a several months-long delinquency<br />
period, the storage facility auctioned <strong>of</strong>f the property<br />
to a church. In assessing the contents, the church discovered<br />
hundreds <strong>of</strong> documents containing PII and notified the base<br />
security <strong>of</strong>ficer who then retrieved the boxes and reported<br />
the incident as a PII breach.<br />
The Cyber Security Division with Marine Corps Camp Lejeune implemented required training for <strong>Department</strong><br />
<strong>of</strong> Defense personnel to increase awareness and protect the Marine Corps network. Devices such as thumb<br />
drives and smart phones, when connected to a computer, are one <strong>of</strong> the many ways a government computer<br />
can contract malware. U.S. Marine Corps photo by Pfc. Nikki Phongsisattanak.<br />
Actions Taken<br />
The records had to be reviewed to identify the extent and seriousness<br />
<strong>of</strong> the PII breach. Names <strong>of</strong> more than 2,800 personnel with<br />
associated personally identifiable information were identified.<br />
A list <strong>of</strong> personnel with high-risk PII elements, such as Social<br />
Security number, date <strong>of</strong> birth and place <strong>of</strong> birth, reduced the<br />
total number <strong>of</strong> personnel who were considered at risk for potential<br />
identity fraud to 1,200. The DON CIO Privacy Office determined<br />
that notifications to the high-risk personnel were required.<br />
Approximately half the high-risk personnel had left the command<br />
and in those cases, home addresses were researched. The irresponsible<br />
Sailor was punished for mishandling PII and failure to<br />
follow DON policy in accordance with the Privacy Act <strong>of</strong> 1974.<br />
Lessons Learned<br />
» Unless it is your own, personally identifiable information<br />
should never be taken home.<br />
» PII must be physically secured at all times.<br />
» A breach <strong>of</strong> this magnitude requires extensive administrative<br />
work to mitigate.<br />
» Supervisors must monitor their workplace and be mindful<br />
that subordinates need continual training and supervision.<br />
» Paper and electronic records must be reviewed on a routine<br />
basis for retention or destruction.<br />
» The DON CIO Privacy Office can provide assistance in finding<br />
addresses <strong>of</strong> personnel who have transferred to a new command<br />
or have left the service.<br />
Similar acts <strong>of</strong> carelessness are frequently reported to the<br />
DON CIO Privacy Office. While this particular incident caused<br />
a number <strong>of</strong> people a substantial amount <strong>of</strong> administrative<br />
work, the department is fortunate in that a responsible person<br />
returned the documents to government control. This minimized<br />
the potential risk to those personnel whose documents<br />
were improperly stored. DON personnel are reminded to properly<br />
safeguard all PII when it is under their control and to report<br />
any breach as soon as it is discovered.<br />
Steve Muck is the privacy lead for the <strong>Department</strong> <strong>of</strong> the <strong>Navy</strong><br />
<strong>Chief</strong> <strong>Information</strong> <strong>Officer</strong>.<br />
42 CHIPS www.doncio.navy.mil/chips Dedicated to Sharing <strong>Information</strong> - Technology - Experience CHIPS April – June 2012 43